Paolo Maffezzoli posted an update: Unsecured Tunneling Protocols Expose 4.2 Million Hosts, [ ]
4sysops
JANUARY 21, 2025
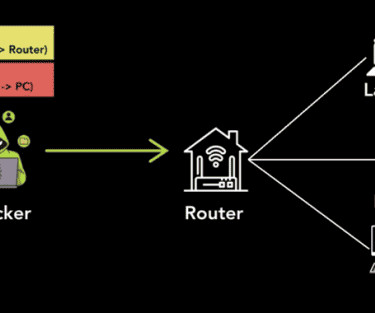
Unsecured Tunneling Protocols Expose 4.2 Million Hosts, Including VPNs and Routers Recent research has identified significant security vulnerabilities in various tunneling protocols, which could be exploited by attackers to conduct a host of malicious activities. Approximately 4.2
































Let's personalize your content