EP144: The 9 Algorithms That Dominate Our World
ByteByteGo
JANUARY 4, 2025
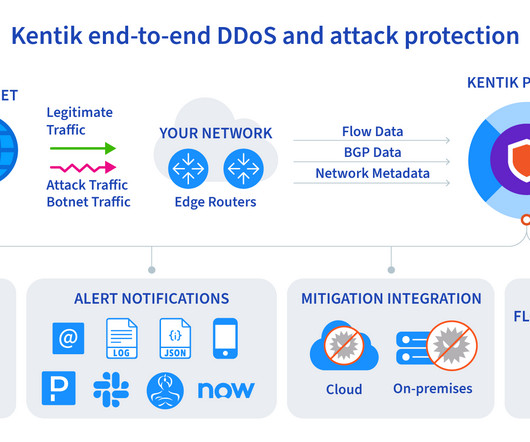
They are used in internet search engines, social networks, WiFi, cell phones, and even satellites. Sorting Dijkstra’s Algorithm Transformers Link Analysis RSA Algorithm Integer Factorization Convolutional Neural Networks Huffman Coding Secure Hash Algorithm Over to you: Are there any other commonly used algorithms we missed?














































Let's personalize your content