The Quantum Sky Is Falling! Understanding the Quantum Threat to Network Security
Cisco Wireless
MARCH 12, 2025
Demystify the potential threat that quantum computing poses to encryption and the security of the network.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Cisco Wireless
MARCH 12, 2025
Demystify the potential threat that quantum computing poses to encryption and the security of the network.
Network Engineering
MARCH 24, 2025
I was reading the Expo documentation and came across the following excerpt: Restrictive network conditions (common for public WiFi), firewalls (common for Windows users), or Emulator misconfiguration can make it difficult to connect a remote device to your dev server over lan/localhost.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cisco Wireless
SEPTEMBER 9, 2024
Success in cybersecurity requires continuous learning and awareness. That's why Cisco University offers industry-leading courses to help keep you ahead of the game. Get an inside look at how it helped one attendee, in our latest blog.

DCNN Magazine
FEBRUARY 14, 2025
The London Internet Exchange ( LINX ), a not-for-profit organisation working for the good of the Internet, has hit a new record maximum traffic peak of 725Gbps at its Manchester network fabric, highlighting the importance of regionalising network traffic. Key initiatives such as the 23.8 For more from LINX, click here.

Cisco Wireless
OCTOBER 16, 2024
Discover how Cisco Secure Firewall 7.4, now on the DoDIN Approved Products List, enhances network security with advanced threat detection, improved performance, and streamlined management.

Cisco Wireless
FEBRUARY 11, 2025
In the changing landscape of network security, the combination of Universal Zero Trust Network Access and Hybrid Mesh Firewalls offers a powerful defense.

Packet Pushers
MARCH 4, 2025
How big is the network security market? What effect is SASE having on security spending? Will security products or security operators get more effective thanks to AI? Director, Enterprise Security and Networkingat the Dell’Oro Group, a. Read more » How big is the network security market?

Cisco Wireless
APRIL 2, 2025
Cisco serves as a Proud Technology Partner of the club, leveraging its solutions across networking, security, Wi-Fi and digital signage to help ensure fans can have one of the most immersive matchday experiences in sports at its stadium, Energizer Park.

Cisco Wireless
SEPTEMBER 4, 2024
Cisco Secure Network Analytics provides pervasive network visibility and security analytics for advanced protection across the extended network and cloud. The purpose of this blog is to review two methods of using threat intelligence in Secure Network Analytics.

Cisco Wireless
APRIL 1, 2025
Secure Network Analytics version 7.5.2 has been released, offering exciting new features such as the Network Visibility Module (NVM) and Zeek detections.

Cisco Wireless
NOVEMBER 8, 2024
You can use public Cisco Talos blogs and third-party threat intelligence data with Cisco Secure Network Analytics to build custom security events.

Cisco Wireless
SEPTEMBER 26, 2024
Pioneering Cisco customers understand that digital resilience helps keep their networks and businesses humming; their customer, employee, and partner experiences consistently great; and their admins… Read more on Cisco Blogs

Cisco Wireless
OCTOBER 17, 2024
Explore how Cisco's streamlined solutions can enhance your network security as the Cybersecurity Pilot Program officially launches.

Cisco Wireless
SEPTEMBER 25, 2024
We believe Cisco is the only leader in the Forrester Wave that offers complete network security. Learn how Cisco microsegments everything.

Cisco Wireless
OCTOBER 24, 2024
Leverage networking, security, collaboration, and AI-ready platforms to enhance customer value and operational efficiency. Cisco technology and partner managed services drive outcome-oriented solutions. Discover more at #CiscoPS24.

Cisco Wireless
AUGUST 14, 2024
We are bringing our Networking, Security, and Collaboration teams together as one organization led by Jeetu Patel as he takes on an expanded role as Cisco’s EVP and Chief Product Officer.

Packet Pushers
APRIL 11, 2025
Network security has evolved from stateful perimeter firewalls with maybe some IDS/IPS to a complex stack delivered as numerous unique tools, which often don’t talk to one another and may need to be operated by specialists.
NW Kings
MARCH 21, 2025
Are you aspiring to become a Cloud Network Engineer? This guide will walk you through the essential steps, qualifications, and resources needed to kickstart your journey as a Cloud Network Engineer. As businesses increasingly migrate to cloud-based solutions, the demand for skilled Cloud Network Engineers continues to rise.

NW Kings
FEBRUARY 28, 2025
As we progress into 2025, the landscape of networking continues to evolve rapidly, with new technologies, protocols, and security measures shaping the way organizations design and manage their networks. CCNA Interview Questions The CCNA certification serves as a foundational credential for network engineers.

NW Kings
MARCH 21, 2025
Are you aspiring to become a Cloud Network Engineer? This guide will walk you through the essential steps, qualifications, and resources needed to kickstart your journey as a Cloud Network Engineer. As businesses increasingly migrate to cloud-based solutions, the demand for skilled Cloud Network Engineers continues to rise.

Dataversity
JANUARY 9, 2023
Network security uses physical and software security solutions to protect network infrastructure from unauthorized access, misuse, failure, alteration, disruption, or unauthorized disclosure of sensitive data. Network security applies to both public […].

CATO Networks
MAY 20, 2020
Since the release of Gartners Market Guide for Zero Trust Network Access (ZTNA) last April, ZTNA has been one of the biggest buzzwords in network security, and for good reason. A policy of zero trust helps enterprises limit exposure to the myriad of threats facing the modern network. Lets find out.

Juniper
JANUARY 10, 2025
Official Juniper Networks Blogs A new threat to network security has surfaced (and its not the quantum computer) The quantum computing era has officially arrived, which is a good thing. This has led some network security vendors to claim that you should upgrade to their PQC solutions today.
The Network DNA
FEBRUARY 20, 2025
Introduction to Universal Zero Trust Network Access (UZTNA) Universal Zero Trust Network Access (UZTNA) is a cutting-edge security framework that consistently applies zero-trust principles to all environments, whether users are on-premises, remote, or hybrid. This special capacity stems from a cloud-native ZTNA.

CATO Networks
JULY 28, 2024
A vision born from complexity Most security companies grow reactively, a continuous, complex cycle of funding and building point solutions to address emerging point problems. It began not just with a forward-looking question, but with a reflective look into the past: What if network security could be as straightforward as clicking a button?
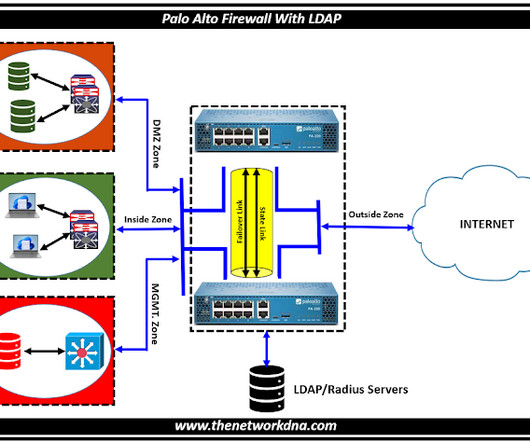
The Network DNA
MARCH 6, 2025
Palo Alto Network Firewalls with LDAP LDAP serves as a protocol designed for interacting with and managing directory services, primarily for verifying user identities and permissions. Palo Alto Network Firewalls with LDAP Unified Authentication : Consider a scenario where numerous systems and devices require user credentials for access.

CATO Networks
NOVEMBER 15, 2020
Network security covers many different areas, including access control, cloud security, malware protection, BYOD security, remote workforce, and web security. The modern digital business of any size, industry, or location needs to keep up with all these responsibilities to maintain a strong security posture.

Packet Pushers
APRIL 30, 2021
Today's Heavy Networking examines the role of deception and "canaries" in network security. A canary sits on a network segment (or multiple segments) and sounds the alarm if it comes under attack. Is this an effective security tool? Is this an effective security tool? How is it deployed and operated?

CATO Networks
FEBRUARY 26, 2020
Forbes recent cybersecurity predictions for 2020 cited an old quote from Cato Networks co-founder Shlomo Kramer. Almost 15 years later, the comparison applies perfectly to the state of network security. So, after all the running weve done in the 2010s, where is network security headed in 2020?

Packet Pushers
JANUARY 31, 2022
Today on the Tech Bytes podcast were talk network security at scale. That is, in a cloud environment, how can you build security capabilities and features into the network while also being able to keep up with security policies, operations, compliance, and more.
CATO Networks
DECEMBER 8, 2022
I opened asking: Can I ask you a few questions about network security ? And CG answered: Sure, I would be happy to help with any questions you have about network security. Encryption : This is the process of encoding data so that it can be transmitted securely and only accessed by authorized users.

Kentik
MARCH 20, 2019
A new research report, “ Network Engineering and Operations in the Multi-Cloud Era ,” looks at the networking challenges enterprises face as they move to cloud environments. Hybrid Cloud Networking Challenges. Therefore, it’s no surprise to see that this study found “security is a huge issue for hybrid cloud networking.”.

CATO Networks
AUGUST 14, 2023
With the transition to the cloud and remote work, some organizations are undervaluing network security. However, network vulnerabilities and threats still require attention. Enterprises should not forgo the core capabilities required to secure the network from security threats.

Packet Pushers
MARCH 28, 2025
There are both benefits and challenges when adopting automation in the public sector, but Red Hat Ansible enhances efficiency, security and service delivery. With the right tooling, network operators can integrate automation into existing environments and improve network security. Read more »

ByteByteGo
JANUARY 4, 2025
They are used in internet search engines, social networks, WiFi, cell phones, and even satellites. Sorting Dijkstra’s Algorithm Transformers Link Analysis RSA Algorithm Integer Factorization Convolutional Neural Networks Huffman Coding Secure Hash Algorithm Over to you: Are there any other commonly used algorithms we missed?

Cisco Wireless
SEPTEMBER 5, 2024
The NFL and Cisco have worked together to develop a playbook that is now coming to life across our partnership, leveraging the collective power of our industry-leading networking, security and observability expertise and solutions.

Router-switch
OCTOBER 14, 2024
The latest security standard, WPA3, aims to prevent potential hackers from accessing your Wi-Fi networks. This article explains WPA3, its benefits, and the reasons that upgrading to a Cisco router that supports WPA3 might significantly increase network security.

CATO Networks
FEBRUARY 9, 2023
As new trends emerge in both cyber attacks and defenses every year, we have decided to list our predictions for the top network security trends of 2023 and beyond. #1. These play a major role in many cyberattacks as cyber criminals gain access to an organizations network and systems, and expand that reach to exploit resources.

Packet Pushers
FEBRUARY 24, 2020
On today's Tech Bytes we discuss the essential role that visibility plays in network security. We explore how Riverbed brings together logs, flow records, and packet capture to provide a full-fidelity view from multiple angles to help you respond to analyze security events. Riverbed is our sponsor. Riverbed is our sponsor.

Clear to Send
DECEMBER 31, 2024
Austin, from Nile Secure, joins us on the show to talk about how Nile is disrupting the networking industry. We talk about the complexity and challenges people face in managing and scaling their networks. What we were interested in learning about is how Nile Secure differentiates themselves in the industry.

Packet Pushers
FEBRUARY 11, 2025
The Cloud Security Maturity Model (CSMM) is a practical blueprint for improving the security of your public cloud deployments. Developed in partnership with the Cloud Security Alliance, IANS, and Securosis, the model covers 12 categories, such as network security and application security, across 3 domains.

Kentik
AUGUST 30, 2021
If you haven’t yet heard the term “network observability,” you will be hearing it soon. Some say that network observability is just marketing hype from vendors. They say, “networks have always been observable, so there’s nothing new here.” I say network observability is not just vendor hype, and this blog will make the case.

Kentik
FEBRUARY 20, 2023
What is cloud networking? Cloud networking is the IT infrastructure necessary to host or interact with applications and services in public or private clouds, typically via the internet. Why is cloud networking important? Cloud networking vs. cloud computing Cloud networking can be thought of as a subset of cloud computing.
CATO Networks
FEBRUARY 18, 2025
This past year was a defining one for all of us at Cato Networks and for the industry at large. The enterprise networking and security market is undergoing a seismic shiftone that we have long anticipated. The days of fragmented, bolt-on security solutions are over. The best is yet to come.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content