How Precision Time Protocol is being deployed at Meta
Engineering at Meta
NOVEMBER 21, 2022
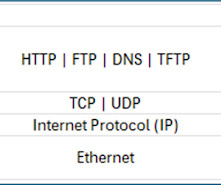
Implementing Precision Time Protocol (PTP) at Meta allows us to synchronize the systems that drive our products and services down to nanosecond precision. Network card Our ultimate goal is to make protocols such as PTP propagate over the packet network.






















Let's personalize your content