Debian 11. Cellular network interface stop transmitting data if MTU value was changed [closed]
Network Engineering
JANUARY 9, 2025
I have issue with cellular modem when I change MTU setting for mobile network interface.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 Network Interface Related Topics
Network Interface Related Topics 
Network Engineering
JANUARY 9, 2025
I have issue with cellular modem when I change MTU setting for mobile network interface.
Network Engineering
MARCH 5, 2025
I also tried removing and re-adding the network interface of the VM. Recently I removed and re-added a connection from the guest and it seems this is when the issue started. I tried using different dns servers, but without success. nslookup also works fine so this likely isn't the issue. What do you suggest I do next?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
DCNN Magazine
JANUARY 16, 2025
The company states that this is the only single-chip timing product that delivers the most resilient performance for AI compute-nodes with high bandwidth and network synchronisation. through to 2027.

Network Engineering
MAY 6, 2024
However, when I tried tracing the route to a ClusterIP service, traceroute could only get as far as the NAT's network interface. I was able to trace the route to another pod (which hopped via the IP address of the host EC2 instance as expected).

Network Engineering
NOVEMBER 27, 2023
Example contents of the /etc/network/interfaces file: auto swp1 iface swp1 auto swp2 iface swp2. I've done this on a SN3700 with Onyx OS, and on a Ruckus switch with FastIron, but I don't believe I have the correct configuration for this SN3700 running Cumulus Linux 5.6.

Packet Pushers
NOVEMBER 8, 2023
What if you could have a multi-cloud network that was cloud-native, but you didnt have to know the nitty-gritty details for each of the clouds? That is, you work with a cloud network interface, and that platform handles the networking–in a cloud-native way–for you. Read more »

Akins IT
OCTOBER 4, 2019
Although theres more than one way to control cross network communication, this blog will cover the method of using Network Security Groups (NSG) to achieve this goal. NSGs can be deployed through the Azure Marketplace and associated to either a subnet, VM network interface or both.
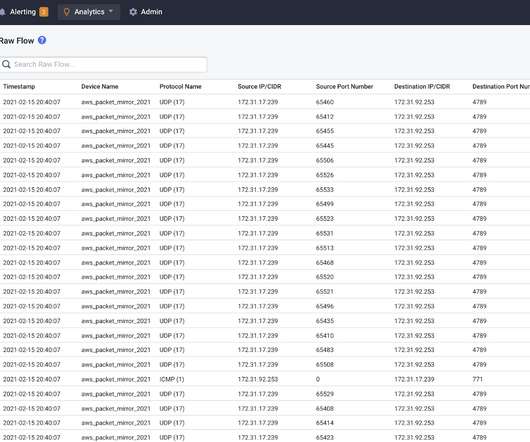
Kentik
MARCH 9, 2021
With this feature, customers can send a copy of their inbound and outbound traffic going through the instances’ network interfaces to a network observability solution for performance, connectivity, and security issues troubleshooting. AWS Mirrored Traffic Granular View using Kentik Data Explorer.

Juniper
MARCH 2, 2025
Additionally, it optimizes the entire network stack, including NVIDIA Collective Communications Library (NCCL), AMD ROCm Communication Collective Library (RCCL), Network Interface Controller (NIC), storage, and network fabric, to ensure maximum performance.

CloudFaire
JANUARY 3, 2025
Aggregation : MPTCP can aggregate the bandwidth of many network interfaces. For example, in a data center scenario, it's common to use interface bonding. A single flow can make use of just one physical interface. MPTCP, by being able to launch many subflows, can expose greater overall bandwidth.
Kentik
JANUARY 19, 2021
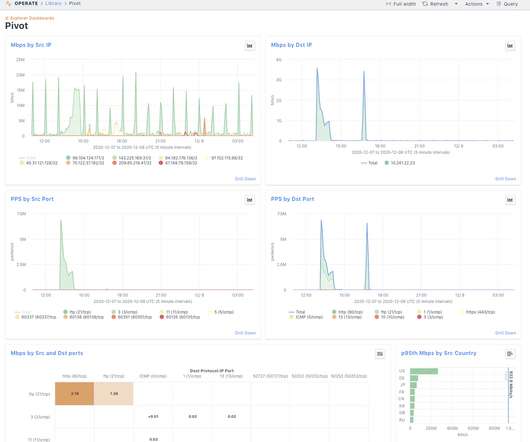
With Kentik, organizations can easily ingest IBM VPC flow logs, visualize inter- and intra-VPC traffic, click on a map to drill into traffic data all the way down to an instance’s vNIC (virtual network interface card), be alerted to anomalies, and troubleshoot complex issues with a powerful yet user-friendly query engine.
The Network DNA
JUNE 4, 2024
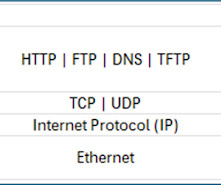
It specifies how data should be packetized, addressed, transmitted, and routed across the network. TCP/IP stack has four layers Application, Transport, Internet, and Network Interface. The OSI Layer Data Link and Physical layer maps to the Network Interface layer of the TCP/IP stack.

Kentik
NOVEMBER 15, 2018
You can create and enable flow logs per ENI (Elastic Network Interface), per subnet or per VPC. These flow logs can be used to analyze and troubleshoot issues within a cloud environment in a few key ways: They’re agentless. This makes integration much easier and cleaner. They include security context. Image source: AWS.
Kentik
APRIL 6, 2021
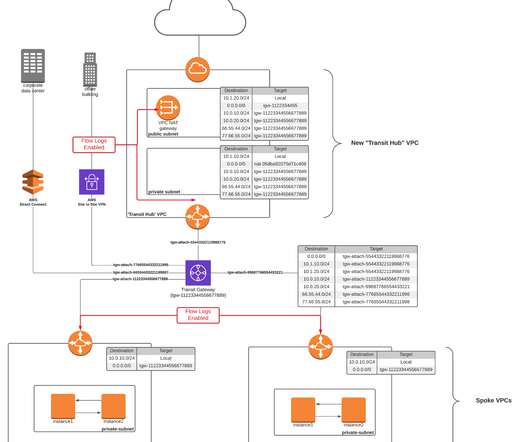
Flow logs are generated only from VPCs, subnets, and network interfaces. One way to quickly instrument this change is to configure flow logs on an interface basis. To do so, just navigate to the “EC2 > Network Interfaces” page in the AWS console and search for the string “gateway.”
CloudFaire
MARCH 19, 2025
Virtual Private Networks (VPNs), forward proxies, and proxy protocols (aka PAC files ) are all methods to enable a machine outside your private network to reach a private IP address/hostname within the private network.
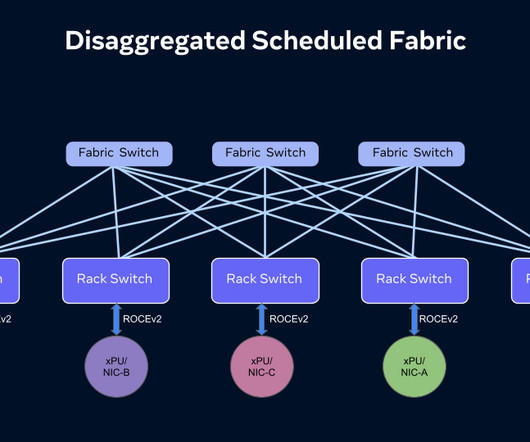
Engineering at Meta
OCTOBER 15, 2024
FBNIC’s key features include: Network interfaces for up to 4×100/4×50/4×25 GE with SerDes support for up to 56G PAM4 per lane. It can support up to four hosts with complete datapath isolation for each host.The FBNIC driver has been upstreamed (available from v6.11 version 1.2.0,
TechDirectArchive
MARCH 6, 2025
To disable IPMI, please login to the ObjectFirst Management Console, click on Settings and select Network. This alone does not change the warning message in this image.

CATO Networks
MAY 23, 2024
Cato Networks is not aware of any malicious exploitation of its ZTNA using this technique. Details of the attack When a VPN client operates, it begins by creating an encrypted version of the original packet received from its virtual network interface.

Kentik
NOVEMBER 7, 2018
AWS was the first cloud provider to make their VPC Flow Logs available to customers, with the goal of helping their users to troubleshoot connectivity and security issues and make sure that network access rules work as expected. Can be enabled per ENI (Elastic Network Interface), per subnet or per VPC.
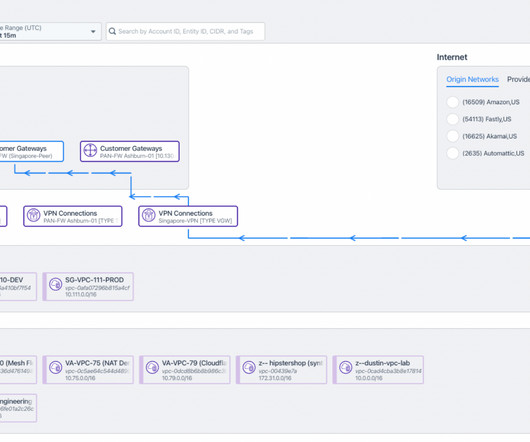
Kentik
APRIL 24, 2023
Here’s a ridiculous list for you: Switches Routers Firewalls CASBs IDS/IPS appliances Wireless access points Public clouds Network load balancers Application load balancers Service provider networks 5G networks Data center overlays SD-WAN overlays Container network interfaces Proxies DHCP services IPAM databases …and the list goes on.

The Network DNA
JANUARY 14, 2025
Ethernet is the group of network technologies that are used at layer 1 and layer 2 of the OSI layer. Ethernet at layer 2 provides the physical addressing to the Network Interface Cards in a networking device. Lets try to learn what Ethernet is here in this small article.

How Funky
JULY 16, 2024
Intel has developed and sold classic Ethernet Network Interface Cards (NICs) for a long time, but many might not be as familiar with their product offerings in the SmartNIC and more advanced NIC categories.
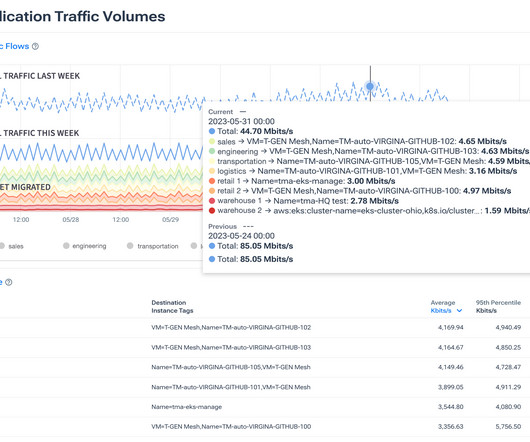
Kentik
JUNE 7, 2023
Flow logs are a valuable source of network traffic information in AWS. They capture detailed metadata about the traffic flowing through various components of your network, such as VPCs, subnets, and network interfaces. AWS Transit Gateways act as a centralized hub for connecting multiple VPCs and on-premises networks.

Kentik
MARCH 6, 2019
Big Cloud Fabric (Big Switch Networks) - is designed to run Kubernetes in private cloud/on-premises environments. CNI-Genie (Huawei) - CNI is short for “Container Network Interface;” this implementation enables Kubernetes to simultaneously have access to different implementations of the Kubernetes network model in runtime.
Cloudera Blog
FEBRUARY 12, 2024
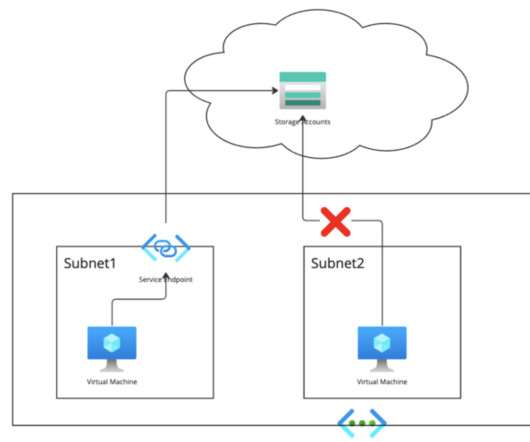
Private Endpoint There is a network interface with a private IP address created with a private endpoint, and there is a private link service associated with a specific network interface, so that other resources in the private network can access this service through the private network IP address.

Kentik
SEPTEMBER 26, 2016
For one, if you’re using an appliance, even a virtual one, you’re assuming that you can connect to and record packets from a network interface of some sort. API calls may be happening between all sorts of components within a cloud that don’t have a distinct “network interface” that an appliance can attach to.

CATO Networks
DECEMBER 12, 2024
Device identification based on MAC address lookup: A mac address is a unique identifier assigned to a devices network interface card (NIC). These rule-based identifications provide the data required for device fingerprinting based on the device mac address, as explained below.
Kentik
JANUARY 13, 2021
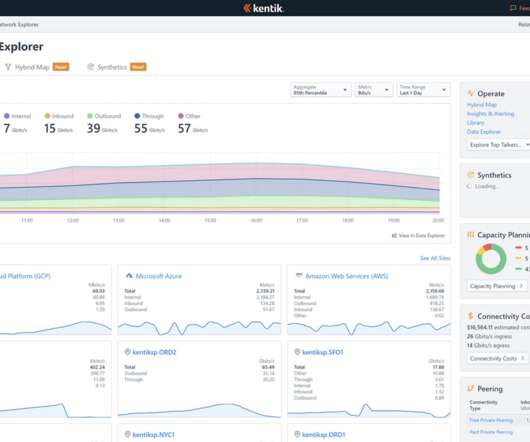
On a network, configurations are constantly changing. Unfortunately, configuration change accidents can happen that bring down parts of the network. Interface dropping packets. Interface issues caused by misconfigurations, errors, or queue limits lead to network traffic failing to reach its destination.

Kentik
SEPTEMBER 11, 2018
It is used to record statistical, infrastructure, routing, and other metadata about traffic traversing an sFlow-enabled network device. sFlow can also export metrics derived from time-based sampling of network interfaces or other system statistics.
CATO Networks
SEPTEMBER 28, 2022
Limited Scalability : Appliance-based security solutions, such as network firewalls , are limited by their hardware. A computer only has so much memory and CPU, and a network interface card has a maximum throughput.

DoorDash Engineering
NOVEMBER 29, 2022
Hashicorp Terraform # Associate the VGW in our VPN to the DXG resource "aws_dx_gateway_association" "vgw_to_dxg" { dx_gateway_id = aws_dx_gateway.doordash_dxg.id

Confluent
JULY 1, 2019
For more complex networking, this might be an IP address associated with a given network interface on a machine. which means listening on all interfaces. I’m using the Docker config names—the equivalents if you’re configuring server.properties directly (e.g., on AWS, etc.) The default is 0.0.0.0,

CATO Networks
JUNE 14, 2023
Figure 1: Different network protocols for OS identification based on the OSI model Starting from the bottom of the stack, at the data link layer, exists the medium access control (MAC) protocol. Over this protocol, a unique physical identifier, called the MAC address, is allocated to the network interface card (NIC) of each network device.

Kentik
MAY 8, 2023
This is another facet of network resilience. How network flows enter and leave a network Network flows enter and leave a network through network interfaces or routers, which are devices that connect different networks together. Let’s consider the most important concepts.

CloudFaire
DECEMBER 30, 2024
To follow along at home, clone a copy of the quiche repository, start a packet capture on the appropriate network interface and then run: cd quiche/h3i SSLKEYLOGFILE="h3i-example.keys" cargo run --example content_length_mismatch In our decrypted capture, we see the expected sequence of handshake, request, response, and then closure.

CATO Networks
JULY 22, 2017
Enterprise firewalls share all networks, objects, and firewall inspection rules between all functions in the system, and all functions use them for enforcement and inspection. One customer over-utilizing the appliances CPUs, memory, or network interfaces will impact other customers sharing those resources.

Engineering at Meta
NOVEMBER 21, 2022
The quality of the network router switches and network interfaces. The software/driver/firmware stack that needs to be executed to send or receive a network packet (referred to as the open systems interconnection, or OSI). There is a famous saying: “If you can measure it, you can manage it.”

CATO Networks
FEBRUARY 4, 2019
As a practical matter, though, you cant fully virtualize a service demarcation; something has to provide the carrier-to-user connection, harmonize practical local network interfaces (like Ethernet) with a carrier service interface, and provide a point of management handoff where SLA enforcement can be monitored by both sides.

Kentik
AUGUST 14, 2017
Classifying Network Interfaces Enhances Engineering and Business Insights. Given that Kentik was founded primarily by network engineers, it’s easy to think of our raison d’etre in terms of addressing the day-to-day challenges of network operations.

Engineering at Meta
NOVEMBER 21, 2022
Another major challenge we faced was ensuring PTP worked with multi-host NICs – multiple hosts sharing the same physical network interface and therefore a single PHC. However, ptp4l has no knowledge of this and tries to discipline the PHC like there are no other neighbors.

Network Engineering
APRIL 16, 2025
To achieve this, I am following this guide to set up a bridge on the Debian machine: [link] I am at the point where I need to put the following config into /etc/network/interfaces: # If unsure what 'netmask' or 'gateway' should be, ask your hosting provider.

Network Engineering
APRIL 15, 2025
An internet gateway at the PUB subnet An Elastic IP attached to one of GW's network interface The GW instance has two network interfaces: one at the PUB subnet (10.25.0.2/24) 24) The WEB instance has one network interface (10.25.240.50/24). 24) with the EIP attributed one at the PVT subnet (10.25.240.2/24)
Network Engineering
FEBRUARY 14, 2025
Router (PC running Linux with two network interfaces, a WAN port, and a LAN port) configured as a gateway between LAN and WAN, receiving the "public" IP address on its WAN port directly connected to the AT&T Fiber Modem.
Network Engineering
JANUARY 31, 2025
Similarly, setting the switch KSZ8873 as DSA device would mean two separate network interfaces. If I were to manage both ports as separate Ethernet connection at the same time, then VLAN would make sense. Is this statement correct?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content