CCNA: Address Resolution Protocol (ARP)
The Network DNA
JULY 16, 2024
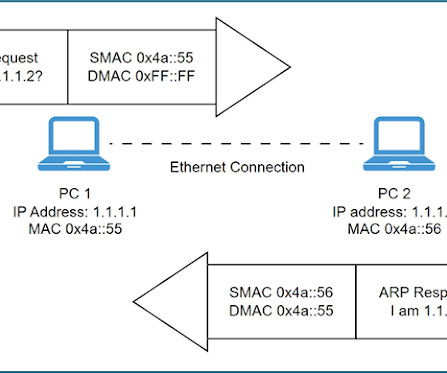
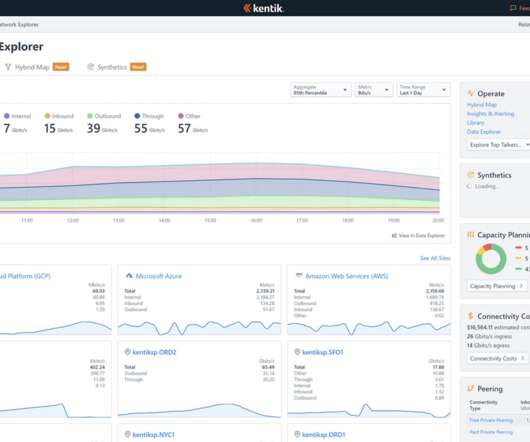
CCNA: Address Resolution Protocol (ARP) In this article, we will talk about ARP that maps the layer 3 address to the layer 2 MAC address. This is similar to Address Resolution Protocol, which maps layer 3 IP addresses to the layer MAC addresses. CCNA RnS Article #28: Why Spanning Tree Protocol? IP address.










Let's personalize your content