Bridging the LAN and the WAN: Our WAN Bridge IoT Hack
PubNub
JANUARY 8, 2025
At last week's Hackendo, we bridged the LAN and the WAN, connecting devices on the Wide Area Network securely and reliably with a WAN bridge
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

PubNub
JANUARY 8, 2025
At last week's Hackendo, we bridged the LAN and the WAN, connecting devices on the Wide Area Network securely and reliably with a WAN bridge

Packet Pushers
JUNE 20, 2022
The same FortiGate NGFW appliance includes networking capabilities including a router, SD-WAN, ZTNA, and a LAN controller. The same FortiGate NGFW appliance includes networking capabilities including a router, SD-WAN, ZTNA, and a LAN controller.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CATO Networks
MAY 24, 2022
As critical applications migrate into Microsoft Azure, enterprises are challenged with building a WAN that can deliver the necessary cloud performance without dramatically increasing costs and complexity. Theres been no good approach to building an Azure SD-WAN until now. Nor does edge SD-WAN help. Lets see how.

Obkio
MAY 29, 2023
Discover the importance of end-to-end network monitoring & how Obkio can revolutionize your network performance. Unleash the power of proactive monitoring.
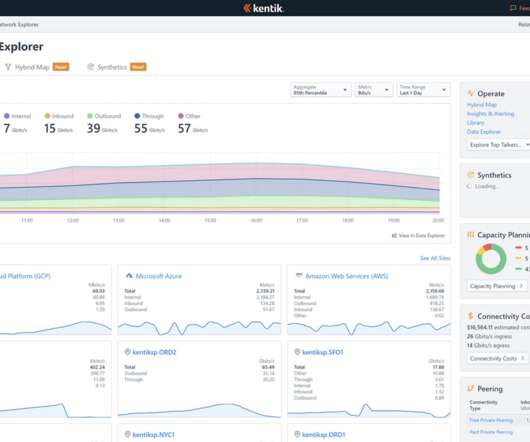
Kentik
JANUARY 13, 2021
The Network is the Key. The network is down!” — I’m sure you heard that before. Despite your best efforts as a network engineer, network failures happen, and you have to fix them. Network troubleshooting becomes easier if your network is observable. Network Troubleshooting Defined.
Network Engineering
NOVEMBER 28, 2016
Need help here Site B TZ105 x0 Lan 192.168.162.1 X2 LAN 10.0.3.1 Site A TZ300 X0 LAN 10.0.1.1 and everything else on this network From Site A, I can only ping 10.0.3.1. SITE B Secondly, I'm going to be connecting up a VOIP/SIP network onto this router for Site B. network? From Site B I can ping 10.0.1.1

Obkio
JULY 10, 2023
Learn how to use Obkio Visions Visual Traceroute tool to troubleshoot network problems with traceroutes in your LAN, WAN, and everything in between.

Kentik
MAY 16, 2021
In today’s digitally transformed world, everyone from internet service providers to enterprises depend upon high-performing and secure networks for business success. It doesn’t matter if you’re Zoom or Major League Baseball, if you’ve got a problem with your network… you’ve got a problem with your business. Hail to the Network.

CATO Networks
AUGUST 17, 2021
You probably know what WAN stands for, but what about all of the other acronyms and abbreviations in the networking world? Heres a list of the key acronyms to help you keep up with the latest in WAN transformation. According to Gartner that coined the term, SASE is the future of network security.
Network Engineering
JANUARY 30, 2025
I'm a beginner to networking and as part of some assignments I have a setup of virtual machines that looks like this: In words, I have two pfsense machines, one on the "right" that is connected to NAT on the WAN interface, my Kali machine on the LAN, the interface having the ip 192.168.53.1 24 network as its target.
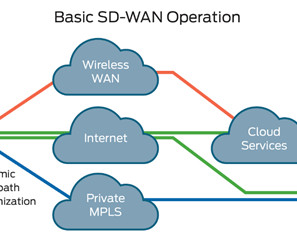
Akins IT
OCTOBER 26, 2001
In 2019, it became clear that SD-WAN had secured its position as the way forward for enterprise WAN connectivity. Market adoption is growing rapidly, and industry experts have declared a winner in the SD-WAN vs MPLS debate. SO WHAT IS SD-WAN? Whats driving all the excitement around SD-WAN?
CATO Networks
MARCH 19, 2018
For the past two years, Cato Networks has led a revolution in enterprise networking: the convergence of software-defined wide area networks ( SD-WAN ) and network security delivered as a single cloud service. For decades, networking and security evolved as silos, creating separate point products in each category.
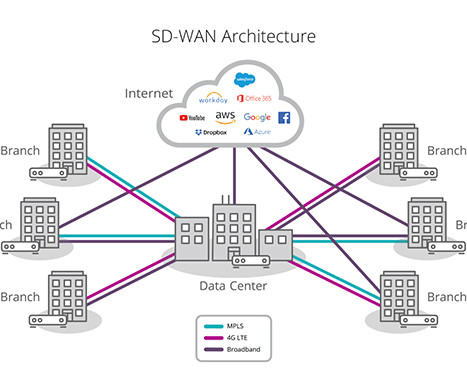
Akins IT
NOVEMBER 17, 2020
Not all network traffic is created equal. Luckily, SD-WAN can be configured to prioritize business-critical traffic and real-time services like Voice over Internet Protocol (VoIP) and then effectively steer it over the most efficient route. The good news is many SD-WAN solutions offer built-in security. IMPROVES PERFORMANCE.

CATO Networks
OCTOBER 31, 2018
Traditional hub-and-spoke networking has enterprises backhauling WAN traffic from branches over MPLS circuits to a central site and applying security policies before sending the traffic to the cloud or the public Internet. SD-WAN has emerged as a popular alternative to MPLS.

CATO Networks
AUGUST 5, 2018
And, as most real-time conversations last orders of magnitude longer than most other types of internet interactions, the probability of a network incident impacting the packet transmission is dramatically higher. The challenge is that in the network world getting Service Level Agreement (SLA) determinism generally has a steep price.

Obkio
JANUARY 25, 2023
Learn how to use Obkio Network Monitoring to identify & check packet loss in your network. Check for packet loss affecting your LAN, WAN, devices and apps.
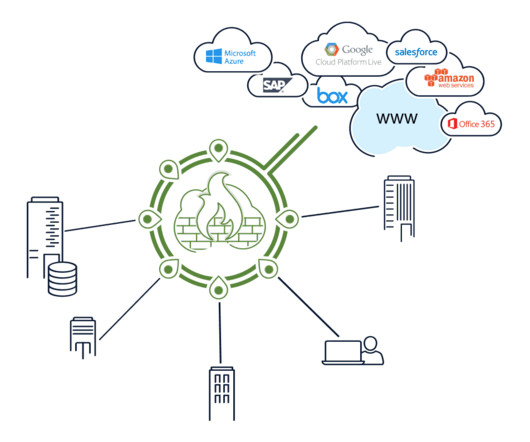
CATO Networks
APRIL 2, 2019
In 2014, Gartner analysts wrote a Foundational Report (G00260732, Communication Hubs Improve WAN Performance) providing guidance to customers on deploying communication hubs, or cloud-based network hubs, outside the enterprise data center. This helps deliver predictable network performance. What is a communication hub?

CATO Networks
SEPTEMBER 11, 2023
Of course, organizations must also protect against East-West threats, to prevent malicious actors from moving within their networks. It is built on a cloud-native architecture, secures traffic to all edges and provides full network visibility and control. See Figure 1 below. You can also enable tracking (ie.
Kentik
MARCH 19, 2020
When more of the workforce shifts to working remotely, it puts new and different strains on the infrastructure across different parts of the network, especially where VPN gateways connect to the network edge. This could mean the users are saturating the internet connectivity or that they’ve saturated the LAN (or maybe WAN).

Packet Pushers
NOVEMBER 27, 2020
On today's Heavy Networking, sponsored by Fortinet, we dive into a variety of topics including a multiplicity of edges that require connectivity and security (WAN edge, LAN edge, cloud edge, remote edge, etc.), Our guest is John Maddison, EVP of Products.

How Funky
OCTOBER 15, 2019
I am going to focus on the Aruba SD-Branch solution (their combination of SD-WAN -LAN and Cloud making it SD-Branch) presentation that is only a portion of the overall presentation that Aruba gave at Network Field Day 21. So, what was most compelling about SD-Branch and specifically the SD-WAN portion?

Kentik
FEBRUARY 27, 2020
Today we announced an evolutionary leap forward for network operations (NetOps), solving for today’s biggest network challenge: effectively managing hybrid complexity and scale, at speed. From the very beginning, the Kentik Platform was designed to collect the most granular data from terabit-scale networks.
Network Engineering
JULY 17, 2024
I need help on finalizing the Network Scheme for a Warehouse. They are always connected to same WiFi Network. I tried reading for SD-WAN but not sure if it's a good idea. Current System has 2 different ISP with total 6 wifi access point for 3 each since it's large Warehouse Each ISP has 3 WiFi access points for connectivity.

CATO Networks
APRIL 6, 2023
Rather, these firewalls are also used for securing WAN access, datacenter LAN segmentation and ensuring reliability and high availability to network traffic. This is done by analyzing and protecting all internet-bound traffic, including remote user traffic, based on rules IT sets between network entities.

Kentik
MARCH 7, 2021
When I onboarded here at Kentik, they said we had a cool new product coming out to help uncover network-related latency. Was it network or application or OS related? Kentik Synthetics was built from lots of feedback from our network-savvy community, and it has proven useful for these network-specialist teams.

CATO Networks
MAY 10, 2022
In the past, most of an organizations employee and IT resources were located on the enterprise LAN. As a result, enterprise security models were focused on defending the perimeter of the corporate network against external threats. This mix of on-prem and cloud-based infrastructure complicates the corporate WAN.
Akins IT
NOVEMBER 1, 2019
SECURING YOUR AZURE VIRTUAL NETWORK WITH A NG FIREWALL PART 3: DEPLOYING A NGFW VIRTUAL APPLIANCE Before virtual security appliances were available in the Azure Marketpl ace, securing your Azure environment required the use of NSGs (Network Security Group). FILL OUT THE FORM.

CATO Networks
SEPTEMBER 15, 2022
However, network firewalls are still a relevant and vital security solution in the era of the cloud. The interconnection between on-prem and cloud environments and between applications within cloud deployments makes network security vital to cloud security.

The Network DNA
JULY 5, 2024
Introduction to VXLAN MP-BGP EVPN Route Types Before we start with the route types lets talk about the EVPN, EVPN (Ethernet Virtual Private Network), enables virtualized Ethernet communication between various network devices. It operates by using IP plus UDP to travel over the physical network.
CATO Networks
SEPTEMBER 8, 2022
IT technologies have changed rapidly, and corporate networks are quickly becoming more distributed and complex. Attempting to make evolving IT infrastructure work with these existing security deployments is a losing battle, as these solutions were designed for networks that are rapidly becoming a thing of the past.
CATO Networks
MAY 31, 2021
VPNs are difficult to scale for a few different reasons, and this forces companies to make tradeoffs between network performance and security. As a result, companies commonly use VPNs to backhaul remote workers traffic through the corporate LAN for security inspection before sending it on to its destination.

CATO Networks
MARCH 14, 2021
Attack surface noun: The attack surface of an enterprise network environment is the sum of the different points (the attack vectors) where an unauthorized user can try to enter the network to execute a malicious intent, such as stealing data or disrupting operations. This has necessitated a rethink of the WAN architecture.

Kentik
APRIL 3, 2018
In our last blog post, At The Turning Point: FinServ Data Networks , we discussed the challenges faced by financial services organizations when it comes to managing modern networks. Networking teams no longer need to be limited by unresponsive tools, aggregated stats, and data deadends.

Kentik
SEPTEMBER 26, 2016
On May 27 of this year, Gartner Research Director Sanjit Ganguli released a research note titled “Network Performance Monitoring Tools Leave Gaps in Cloud Monitoring.” You’d put a few others — I emphasize “few” because these appliances were and are not cheap — at other major choke points in and out of the network.

Kentik
JUNE 13, 2016
According to 2015 research reports published by Ponemon, Mandiant, and others, the median pre-detection dwell time for an intruder in a target network ranges at around 200 days. Reducing a network's intruder dwell time is mostly about detection. Over 95% of IT security attacks traverse some aspect of a network to execute.
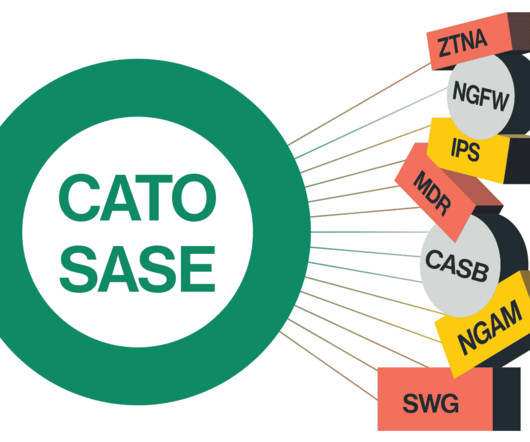
CATO Networks
SEPTEMBER 28, 2022
Corporate IT networks are rapidly changing. The Corporate WAN is Rapidly Changing In the past, the majority of an organizations IT assets were located on-prem. The company managed its own data centers, and employees were primarily connected directly to the corporate LAN.

Network Engineering
AUGUST 19, 2020
The problem is that when ESXi is down it takes down all the network with it, so I have to boot up another router to log in to it. WAN > OPNsense (in ESXi)> switch (C3560G) OPNsense is DHCP server Thing is that i would like the switch to deal with the DHCP, to avoid being naked when ESXi needs maintenance. 255.255.255.0

CATO Networks
DECEMBER 1, 2022
To do their jobs, employees need high-performance, secure access to corporate networks and IT assets. As remote and hybrid work schedules become more common, companies are deploying secure remote access solutions, such as virtual private networks (VPNs) to support them.

Kentik
JULY 28, 2021
Here’s a list of utilities and techniques that many of us are still using today to detect and isolate network packet loss: Ping : Using ping on the command prompt to measure packet loss is generally done to verify connectivity of a host, but “request timed out” could indicate if there is any packet loss.

CATO Networks
FEBRUARY 5, 2018
These guys are on the frontline of network architecture and working to educate the world about the changing landscape of enterprise network technology. Andrew Lerner (Gartner) ( @fast_lerner ) Andrew is a Gartner guru specializing in enterprise networking. Andrew also specializes in the challenges of Open Networking.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content