Multi-Path TCP: revolutionizing connectivity, one path at a time
CloudFaire
JANUARY 3, 2025
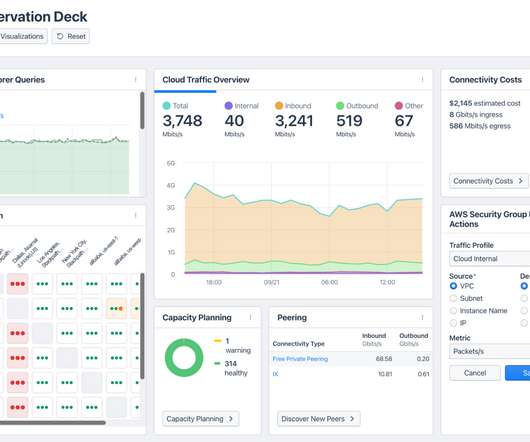
Typically, Linux is used on the server side, and iOS/macOS as the client. Linux as a server Conceptually, the MPTCP design is pretty sensible. After the initial TCP handshake, each peer may announce additional addresses (and ports) on which it can be reached. This can be managed on Linux by ip mptcp endpoint.



































Let's personalize your content