Open sourcing h3i: a command line tool and library for low-level HTTP/3 testing and debugging
CloudFaire
DECEMBER 30, 2024
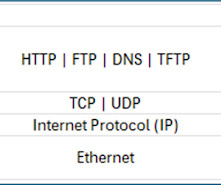
Internet protocol specifications are instructions designed for engineers to build things. Protocol designers take great care to ensure the documents they produce are clear. The Internet is central to everyone's lives, and we depend on these implementations. Any deviations from the specification can put us at risk.
















Let's personalize your content