Ukraine’s Wartime Internet from the Inside
Kentik
APRIL 10, 2023
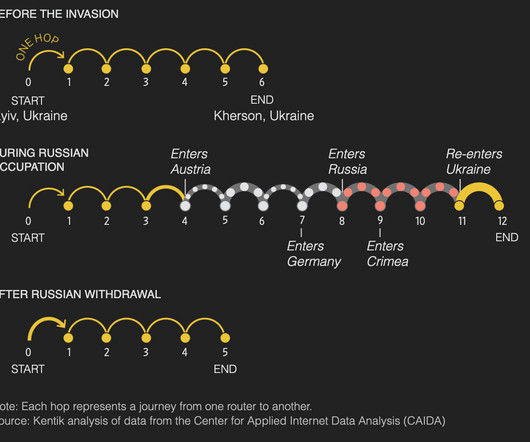
Ark consists of servers located around the world continuously performing traceroutes to randomly selected IP addresses. One of those Ark servers is located in Kyiv. CAIDA graciously provided the data generated from this server to Kentik for the following analysis. and many other Russian networks became unreachable.












Let's personalize your content