Firewall as a Service: Uniting your Network and Security Again
CATO Networks
DECEMBER 7, 2016
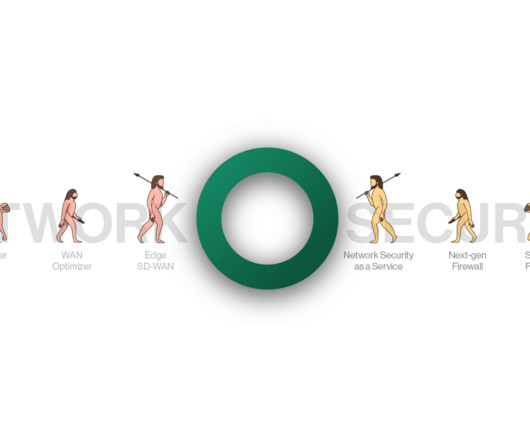
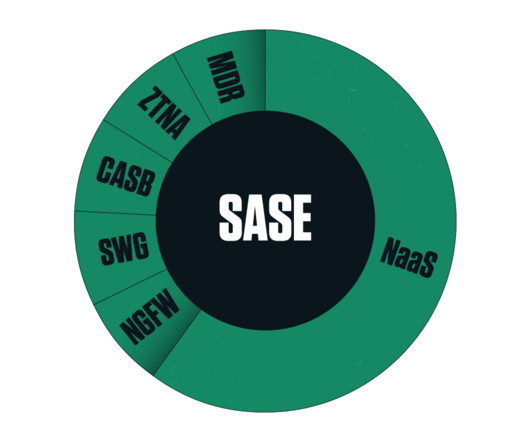
Today, you need to manage: Connectivity and security for your remote locations with multiple perimeter-based FW or UTM appliances. Compatibility and security policies for multiple cloud and IaaS services. How Firewall as a Service can address these challenges, and what are the required capabilities.




















Let's personalize your content