Internet of Things (IoT) and Event Streaming at Scale with Apache Kafka and MQTT
Confluent
OCTOBER 10, 2019
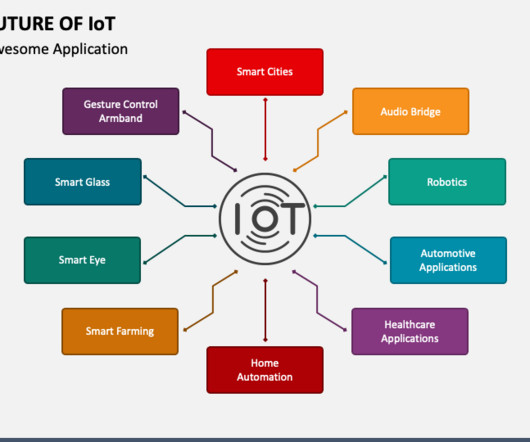
The Internet of Things (IoT) is getting more and more traction as valuable use cases come to light. Machines provide a large number of usually closed and incompatible protocols in a proprietary format. OPC UA: this is an open and cross-platform, machine-to-machine communication protocol for industrial automation.






















Let's personalize your content