Reinforcing Networks: Advancing Resiliency and Redundancy Techniques
Kentik
MARCH 29, 2023
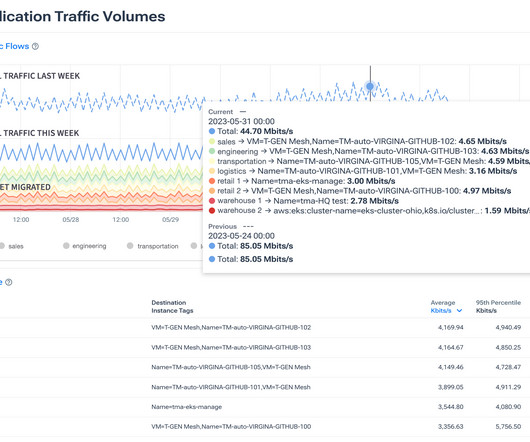
Routing protocols and their impact on network resilience: The roles of IGP and BGP Let’s first dive into how routing protocols, particularly Interior Gateway Protocols (IGP) and Border Gateway Protocol (BGP) , can influence network resilience and help reduce the need for complete redundancy.













Let's personalize your content