EP144: The 9 Algorithms That Dominate Our World
ByteByteGo
JANUARY 4, 2025
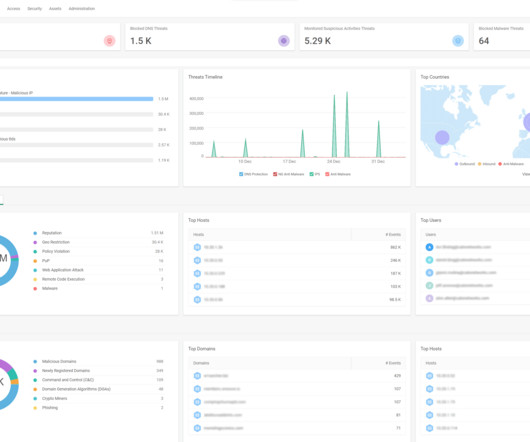
This week’s system design refresher: The 9 Algorithms That Dominate Our World What does API gateway do? They are used in internet search engines, social networks, WiFi, cell phones, and even satellites. What does API gateway do? Step 1 - The client sends an HTTP request to the API gateway. How does gRPC work?











































Let's personalize your content