How to Monitor Traffic Through Transit Gateways
Kentik
JUNE 21, 2021
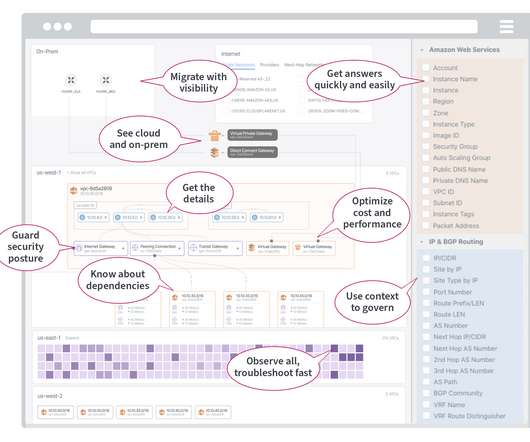
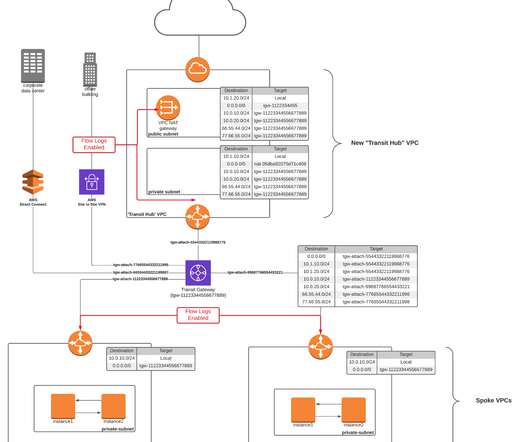
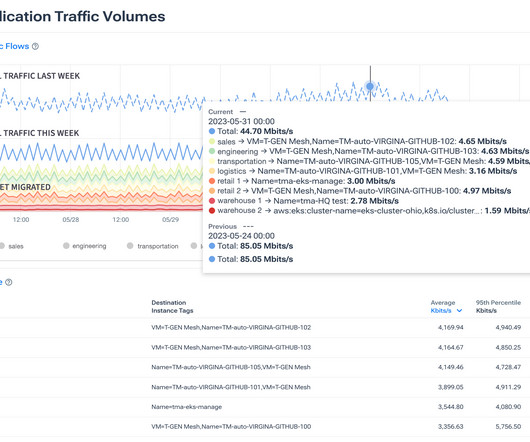
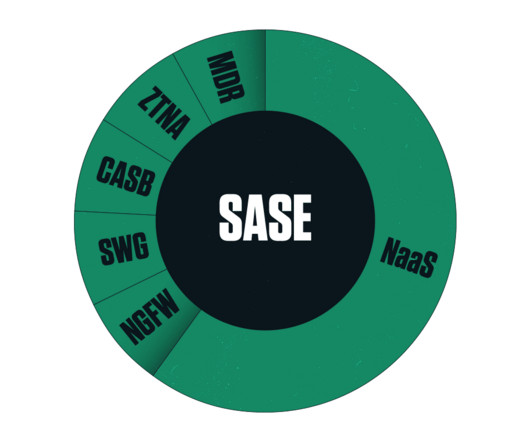
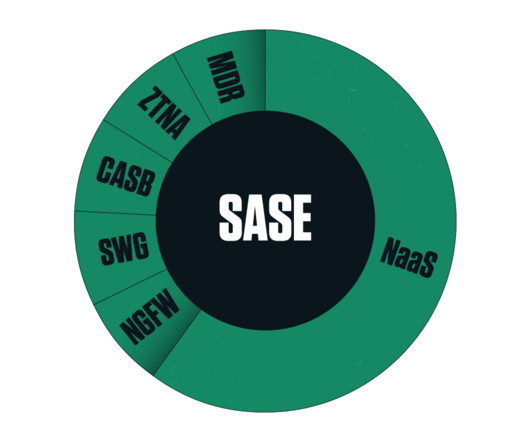
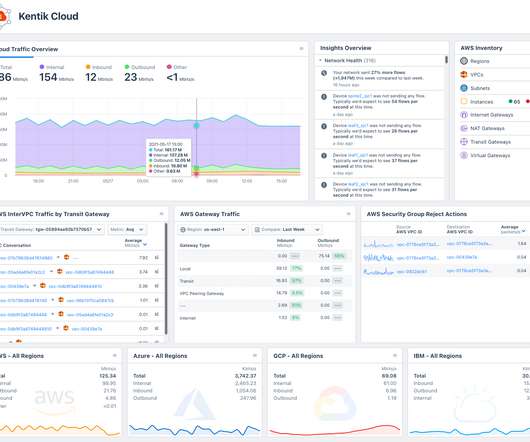
For AWS cloud networks, the Transit Gateway provides a way to route traffic to and from VPCs, regions, VPNs, Direct Connect, SD-WANs, etc. However, AWS offers no easy way to gain visibility into traffic that crosses these devices — unless you know how to monitor Transit Gateways. data centers, offices, branches, etc.).






































Let's personalize your content