Gateways, Guardrails, and GenAI Models
Expedia Group Tech Blog
OCTOBER 24, 2024
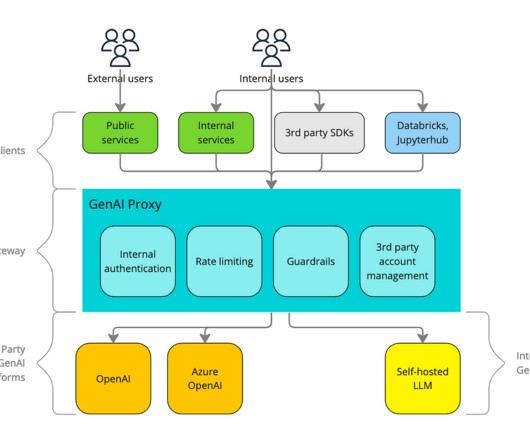
Request-response governance by filtering all requests and responses through an extensible list of guardrails. Their primary function is to ensure that every interaction involving generative AI models adheres to stringent security protocols and compliance standards.













Let's personalize your content