Announcing Complete Azure Observability for Kentik Cloud
Kentik
JUNE 27, 2023
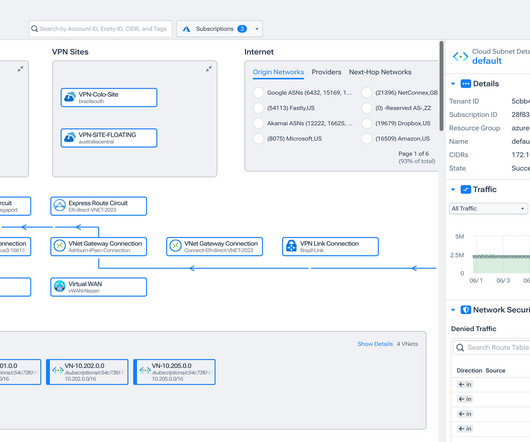
It includes rich metrics for understanding the volume, path, business context, and performance of flows traveling through Azure network infrastructure. To that end, we’re excited to announce major updates to Kentik Cloud that will make your teams more efficient (and happier) in multi-cloud.












Let's personalize your content