Basic configurations on Cisco ASA Firewall - Part 2
The Network DNA
NOVEMBER 26, 2024
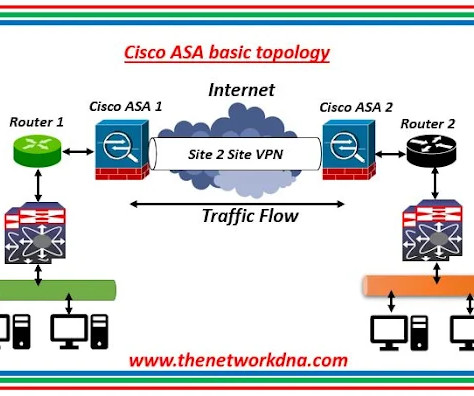
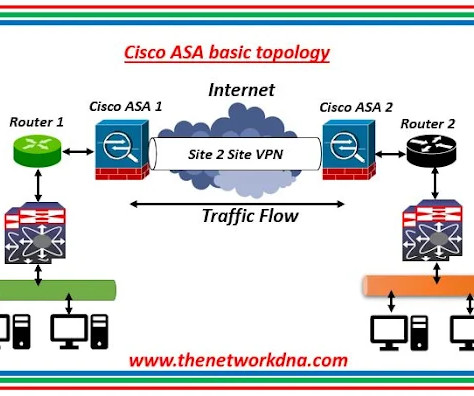
Basic configurations on Cisco ASA Firewall - Part 2 As a part of the understanding on the basics of Cisco ASA firewalls, these are some of the commands used to configure Cisco ASA firewall in real scenario. Cisco ASA in a Network Configuring DHCP, AAA, and SSH NDNA-ASA(config)# dhcpd address 10.10.10.3-10.10.10.100 255.255.255.0




























Let's personalize your content