Cisco advances embedded cyber resilience in industrial routers
Cisco Wireless
SEPTEMBER 12, 2024
Discover how embedded cyber resilience in Cisco’s industrial routers securely connects distributed operations at scale.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Network Engineering
JANUARY 23, 2025
I have a router that uses a SIM card for connectivity, and I create a socket connection. After the connection is disrupted, when I attempt to send a packet from the server using the previously established socket, the router responds with a RST (reset) packet. I have checked the firewall of the router but it seems to be deactivated.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Network DNA
NOVEMBER 26, 2024
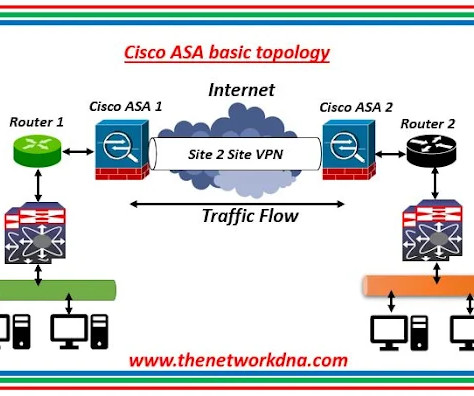
Basic configurations on Cisco ASA Firewall - Part 1 As a part of the understanding on the basics of Cisco ASA firewalls, these are some of the commands used to configure Cisco ASA firewall in real scenario. Cisco ASA Firewall in a Network What is Cisco ASA Firewall? 255.255.255.0 inside Continue Reading.
The Network DNA
NOVEMBER 26, 2024
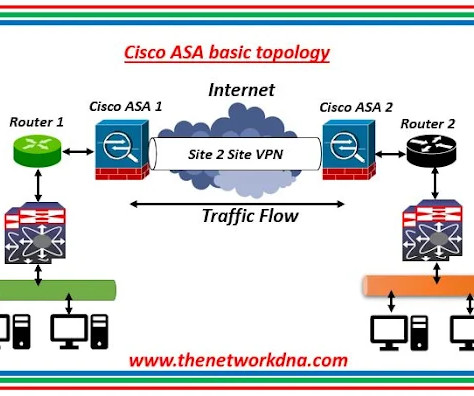
Basic configurations on Cisco ASA Firewall - Part 2 As a part of the understanding on the basics of Cisco ASA firewalls, these are some of the commands used to configure Cisco ASA firewall in real scenario. Cisco ASA in a Network Configuring DHCP, AAA, and SSH NDNA-ASA(config)# dhcpd address 10.10.10.3-10.10.10.100 255.255.255.0

CATO Networks
JUNE 19, 2017
In a 2016 Hype Cycle for Infrastructure Protection report , Gartner Analyst Jeremy DHoinne initiated the emerging category of Firewall as a Service (FWaaS). This is the first time an established firewall vendor that had built its business on selling appliances is offering its core platform as a cloud service.
The Network DNA
JULY 31, 2024
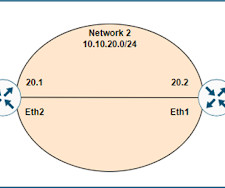
Here well see how a layer 3 switch or a router transmit packets between different networks using the layer 3 destination address. Routing is performed by routers, firewalls, multi-layer switches and gateways. Any host that is not part of the source device network can be reached through the default router or gateway.

Kentik
JANUARY 6, 2021
Traditional WAN : WAN access switches, integrated services routers, cloud access routers. Service provider backbone : Edge and core routers, transport switches, optical switches, DC interconnects. Wireless access points and controller.

Packet Pushers
JUNE 20, 2022
The same FortiGate NGFW appliance includes networking capabilities including a router, SD-WAN, ZTNA, and a LAN controller. The same FortiGate NGFW appliance includes networking capabilities including a router, SD-WAN, ZTNA, and a LAN controller.

DoorDash Engineering
NOVEMBER 29, 2022
Vendor’s data centers have private links to their own routers which are set up in AWS Direct Connect Locations. Direct Connect Location: a high-speed AWS network traffic exchange center that contains both AWS Direct Connect routers and vendor’s routers. The VGW is a VPC edge router for exposing internal traffic.
Network Engineering
JANUARY 1, 2025
Objectives Install FreeRADIUS on CentOS(steam 9) to perform Cisco device authentication Perform dot1x authentication on all ports of the switch Perform authentication by connecting a laptop to the switch CentOS(203.230.7.2) - Cisco 2960 Switch(203.230.7.254) - Cisco 2800 Series Router(gig0/0 : 203.230.7.1, 255.255.255.0 255.255.255.0

ByteByteGo
NOVEMBER 23, 2024
share one router with a single public IP address. When a device wants to access the internet, it sends a request to your router. The router’s NAT process replaces the private IP with the router’s public IP. NAT acts as a basic firewall that hides internal IP addresses.

Kentik
MARCH 13, 2023
We still need to connect our infrastructure to the public internet, so the enterprise WAN is still about routers, circuit IDs, and perimeter firewalls. But today, those routers are likely a centrally managed SD-WAN, and those perimeter firewalls could be a CASB or other cloud-based firewall service.

Packet Pushers
MAY 4, 2021
This feature builds a real-time model of your production network by collecting information from switches, routers, firewalls, and other network devices. This feature builds a real-time model of your production network by collecting information from switches, routers, firewalls, and other network devices.

CATO Networks
APRIL 25, 2017
Service insertion refers to the adding of networking services, such as firewalls or load balancers, into the forwarding path of traffic. If wed like to insert a local firewall for a group of stations, for example, we can group those stations into a separate VLAN. 1 in this case) and a VRF on the other side of the router (VRF #2). .#1

Obkio
APRIL 4, 2023
Learn about Network Device Monitoring to easily monitor performance of firewalls, routers & switches to identify problems like high CPU & bandwidth usage.
Obkio
MAY 1, 2023
Learn about what SNMP monitoring is & how to use it to monitor performance of networking devices like firewalls, routers, switches and wifi access points.

Packet Pushers
JANUARY 22, 2021
Network Functions Virtualization (NFV) transforms routers, load balancers, firewalls and other network devices into virtual instances that can be service-chained, spun up and down as needed, and are cloud-friendly. But if you're a hardware hugger or have been been burned by virtualization in the past, should you avoid NFV?

CATO Networks
SEPTEMBER 28, 2017
With stacks of appliances, including firewalls, WAN optimizers, and routers, comes complexity and breeding ground for problems. The sites ended up with dual routers running HSRP (the Hot Standby Router Protocol) to load balance traffic between them. Finally, managing the MPLS and security infrastructure was painful.

NW Kings
JANUARY 7, 2025
In this blog, we will explore what static routes are, how they differ from dynamic routes, and how to configure them on routers like Cisco devices. This characteristic makes them efficient for routers with limited processing capabilities. NOTE : Join our Network Specialist Master’s Program today!
Network Engineering
NOVEMBER 28, 2016
I understand that firewall needs to be able to allow for ping on 10.0.3.0 SITE B Secondly, I'm going to be connecting up a VOIP/SIP network onto this router for Site B. Although I cannot access a single service, VMConsole, or anything else on the 10.0.3.0 Do I need to create a VLAN for the Phones? network?
Network Engineering
JANUARY 4, 2025
[I'm unsure whether this should be posted on Network Engineering, Server Faults or Android Enthusiasts] We have a hotspot service that connects into MikroTik routers, using the built-in hotspot facility. From a networking point of view, DNS is functional and there are no firewall entries that can restrict the traffic.

Kentik
MARCH 3, 2020
switches, routers, firewalls), hence the licensing we use is lower for the data center devices. However, our data center pricing is much lower and has fewer features, such as full BGP support, which edge devices require. The challenge is that within the data center you have many more devices (e.g.,

Kentik
JANUARY 24, 2022
Back in the 1990s, NetFlow was introduced on Cisco routers as a means to collect information about IP network traffic as it enters or exits an interface. It’s pretty much impossible to block HTTP and HTTPS ports at the firewall. At most companies, there are multiple DNS servers to collect from and hundreds of routers.
Kentik
APRIL 3, 2023
For example, to determine latency using traffic generated from probes or by analyzing packets, that traffic would likely pass through routers, firewalls, security appliances, load balancers, etc. Second, in a busy network, devices such as routers, switches, and firewalls may be very busy operating at a relatively high CPU.

CATO Networks
OCTOBER 30, 2017
The spread of massive ransomware outbreaks, such as NotPetya , made firewalling particularly important. Routers at every store directed point-of-sale (POS) traffic across the IPsec VPN to firewalls in the company’s Singapore datacenter housing its POS servers.

CATO Networks
NOVEMBER 15, 2018
When the same solution can replace the router, firewall, and WAN optimizer, change management gets easier, and the need to do network functional regression testing decreases. Loss or absence of a team member no longer carries the risk of a vital skill set going missing.

CATO Networks
NOVEMBER 1, 2019
One sticking point has always been the branch network stack: deploying, configuring, managing, and retrieving the router, firewall, WAN optimizer, etc., Cloud Stack Benefits the Enterprise: Freedom and Agility People want a lot out of their SD-WAN solution: routing, firewalling, and WAN optimization, for example.

CATO Networks
JUNE 23, 2019
The infamous malware that crippled global DNS provider Dyn, French Web host OVH and security journalist Brain Krebs Web site with botnets of infected home routers, baby monitors and other IoT devices is now infecting enterprise network equipment, according to a recent Palo Alto Networks blog and Network Computing article.

CATO Networks
APRIL 23, 2019
Thus, despite the industry hype, NFV will largely look like the managed or hosted firewalls and other devices of the past, with some incremental benefits from using virtual instead of physical appliances. These may be any network function, such as SD-WAN, firewalls, IPS/IDS, secure web gateways and routers.
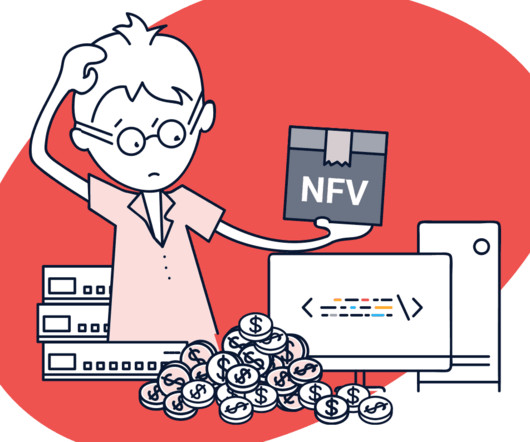
CATO Networks
NOVEMBER 21, 2017
At the core of NFV is the notion that network functions, such as SD-WAN , firewalling and secure web access, can be delivered as virtual appliances and run either on premises (vCPE) or at the carrier core data centers (hosted). Some VNFs, such as routers and SD-WAN, consume relatively few resources.
Kentik
FEBRUARY 8, 2023
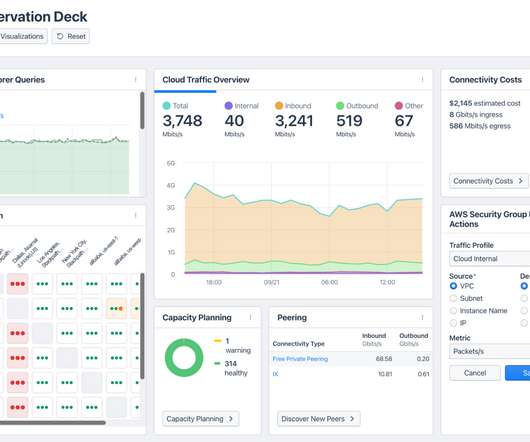
Port mirroring Another method for gathering traffic telemetry is port mirroring, which replicates (mirrors) the network traffic on a switch or router to a monitoring device. Correlate the data with other information, such as firewall logs, threat intelligence feeds, and endpoint security data.
CATO Networks
OCTOBER 30, 2019
Routers forward these packets from source to destination and data encapsulation enables the data to traverse the TCP/IP stack. However, since many firewalls block ICMP (Internet Control Message Protocol) and it has a low priority, ping isnt always enough. Common causes of packet loss include: Routers with heavy CPU load.

CATO Networks
SEPTEMBER 13, 2018
One option is to run standalone virtual services as individual virtual CPE (vCPEs) on physical appliances, such as routers or servers. Routing functions tend to run in, well, routers, firewall functions tend to run in firewalls. The other option? Run them as shared, multi-tenant, cloud-resident services.

CATO Networks
MARCH 9, 2022
The routers are stateless and control plane intelligence is limited, which means routing decisions arent based on application requirements or current network levels. When designing the SD-WAN middle mile, organizations need to find a solution that provides the same capabilities. Instead, providers commercial preferences often take priority.

CATO Networks
MARCH 21, 2019
Its expensive and time-consuming for an engineer to visit branch locations around the globe to install firewalls and routers. Conceptually, putting a WAN optimizer or a router on some sort of white box server sounds great. Administrators need to worry about firewall rule sets, configuration updates, and software updates.
CATO Networks
APRIL 4, 2018
However, MPLS traffic from the service provider to the on-premises routers is notoriously expensive. Internet VPNs also require physical appliances, such as routers and firewalls, to be installed and maintained at each location in the enterprise network. And provisioning with the provider can take 3-6 months.
CATO Networks
SEPTEMBER 13, 2017
None of this was easy to manage and generations of network professionals had to manually configure and reconfigure routers and WAN optimizers to manage this complex environment. Enter SD-WAN. However, this creates a new attack surface for the organization that must be secured. Edge SD-WAN does not address security requirements.

Router-switch
OCTOBER 9, 2024
GrowingDemand for Robust Networking… The post How Cisco Secures and Connects NFL Events Around the World first appeared on Router Switch Blog.

Kentik
MAY 8, 2023
It is used to maintain network connectivity by helping routers find the best path for traffic to travel through. BGP also helps to create network resilience by allowing routers to quickly detect and respond to outages or changes in the network topology.

CATO Networks
APRIL 14, 2022
Traffic processing engines are at the core of many networking and security products including routers, SD-WAN devices, next generation firewalls, secure web gateways, IPS , CASB/DLP, and ZTNA products. The answer is: core capabilities should be built once and be leveraged to address multiple functional requirements.
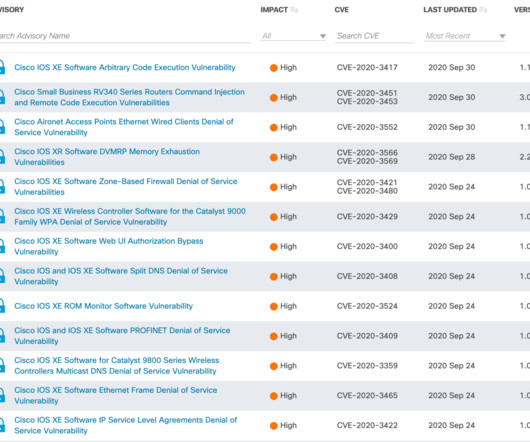
CATO Networks
OCTOBER 5, 2020
All Cisco products running IOS were impacted, including IOS XR Software, NX-OS Software, and RV160 VPN Router. More specifically, Cisco advisory notes that these vulnerabilities could allow an unauthenticated, remote attacker to cause the device to reload or stop forwarding traffic through the firewall.
Kentik
MARCH 19, 2020
The richest data sources are from the VPN devices or firewalls. If the VPN gateways cannot generate flow or Syslog with traffic, the next richest data comes from the edge routers or switches near the VPN devices. Kentik provides an easy way to see not only the entire network but also how it’s being used.
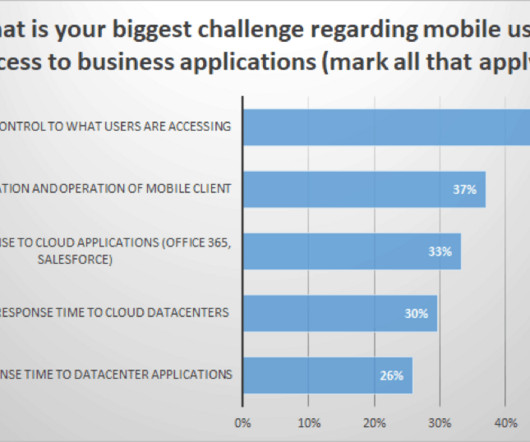
CATO Networks
NOVEMBER 27, 2017
Thats because SD-WAN appliances were designed to replace routers, WAN optimizers and the rest of the networking stack needed for site-to-site connectivity not mobile connectivity. With SD-WAN appliances, mobile users are still left establishing VPNs back to on-premises firewalls (or concentrators).
CATO Networks
MARCH 19, 2018
Our CEO, Shlomo Kramer , created the first commercial firewall as the co-founder of Check Point Software, the first Web Application Firewall at Imperva, and was a founding investor at Palo Alto Networks that built the first next-generation firewall. They had the vision and the track record.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content