Firewall as a Service: Uniting your Network and Security Again
CATO Networks
DECEMBER 7, 2016
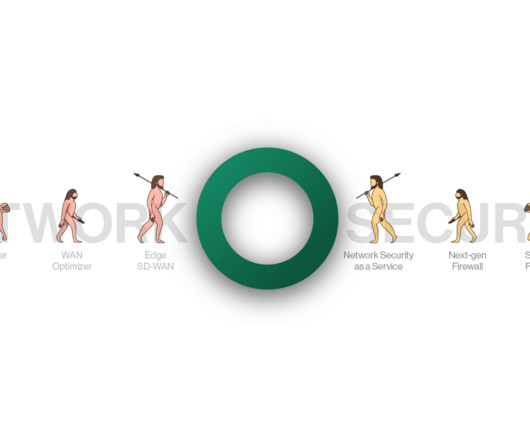
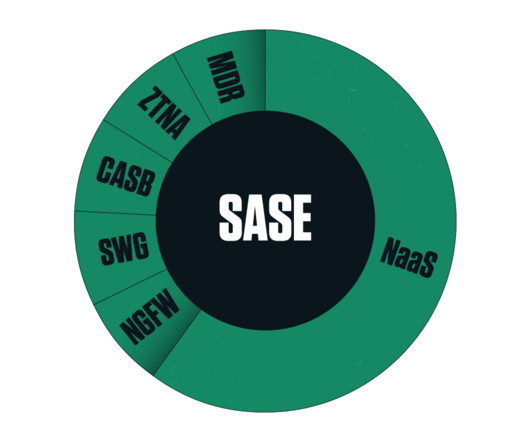
It really wasnt very long ago when installing a Firewall (FW) or Unified Threat Management (UTM) system at the perimeter was deemed secure enough to protect corporate networks. But those very networks have changed dramatically over the past decade. Compatibility and security policies for multiple cloud and IaaS services.

















Let's personalize your content