The 4 Values of SD-WAN
CATO Networks
JULY 29, 2018
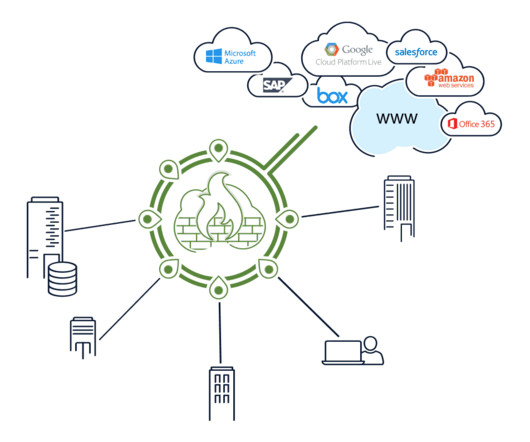
The network perimeter has dissolved with IaaS, SaaS, and mobile users breaking that barrier and shifting more traffic to the Internet. MPLS was not designed for this new reality. Point-of-sale (POS) traffic went across the IPsec VPN to firewalls in the companys Singapore datacenter housing its POS servers.












Let's personalize your content