CCNA: IP Routing
The Network DNA
JULY 31, 2024
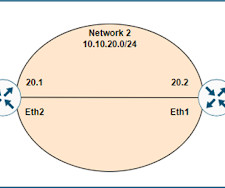
This address is called the layer 3 address or IP address. A process to analyze the layer 3 header and taking the forwarding decision based on the destination address is called the routing. Routing is performed by routers, firewalls, multi-layer switches and gateways.



























Let's personalize your content