Announcing Complete Azure Observability for Kentik Cloud
Kentik
JUNE 27, 2023
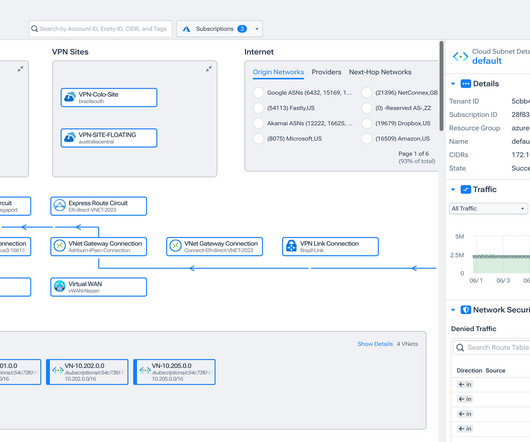
Live traffic flow arrows demonstrate how Azure Express Routes, Firewalls, Load Balancers, Application Gateways, and VWANs connect in the Kentik Map, which updates dynamically as topology changes for effortless architecture reference. Kentik Map for Azure makes denied traffic easily discoverable from each subnet visualized.












Let's personalize your content