How to Stop WannaCrypt Infections with the Cato Cloud
CATO Networks
MAY 15, 2017
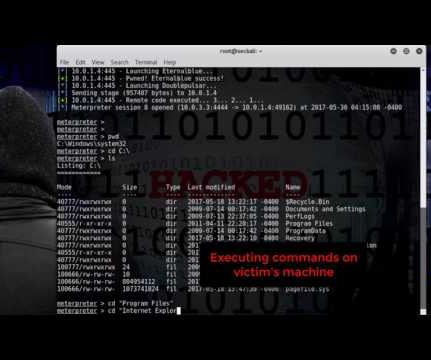
But what makes the attack so unusually virulent is how it exploits a vulnerability in the Windows SMB protocol. SMB is used by Windows machines for sharing files and the ransomware uses SMB to spread to other vulnerable devices on a network. Once installed, the ransomware encrypts the files on the machine.










Let's personalize your content