The Quantum Sky Is Falling! Understanding the Quantum Threat to Network Security
Cisco Wireless
MARCH 12, 2025
Demystify the potential threat that quantum computing poses to encryption and the security of the network.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Cisco Wireless
MARCH 12, 2025
Demystify the potential threat that quantum computing poses to encryption and the security of the network.

Juniper
JANUARY 10, 2025
Official Juniper Networks Blogs A new threat to network security has surfaced (and its not the quantum computer) The quantum computing era has officially arrived, which is a good thing. However, the bad news is that this new era also brings the ability to break current VPN encryption algorithms.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CATO Networks
NOVEMBER 19, 2024
Introduction In todays digital environment, encrypted traffic has become the norm, with over 90% of web communications now utilizing encryption. While this secures data in transit, it has become a blind spot for enterprises, enabling attackers to hide malware within encrypted channels.
CATO Networks
SEPTEMBER 22, 2022
A growing percentage of Internet traffic is protected by encryption. According to Google , approximately 95% of web browsing uses the encrypted HTTPS protocol. This trend toward traffic encryption has been driven by a few different factors. The move toward data encryption is a mixed blessing for cybersecurity.

CATO Networks
MAY 24, 2016
MPLS security is based on the fact that it is a private network vs. the public Internet. The private nature of MPLS allowed an organization to not encrypt MPLS traffic, a big benefit in terms of encryption key management and required CPE (customer premise equipment) capabilities. But does this address all WAN challenges?
CATO Networks
DECEMBER 8, 2022
I opened asking: Can I ask you a few questions about network security ? And CG answered: Sure, I would be happy to help with any questions you have about network security. Encryption : This is the process of encoding data so that it can be transmitted securely and only accessed by authorized users.
CATO Networks
SEPTEMBER 15, 2018
MPLS WANs were never designed with security, and specifically, threat protection, as a core feature. SD-WAN is forcing network architects to rethink their network security design in the post-MPLS era. The Internet Challenge for MPLS and Hybrid WAN Traditionally, MPLS was always considered a private network.

CATO Networks
APRIL 20, 2016
We now have an opportunity to create something truly new and exciting: Software-defined infrastructure – the integration of software-defined networking and software-defined network security. Lets start with the network. Imagine of a fully integrated control plan AND data plane all in software – a full SDN.

CATO Networks
MARCH 14, 2021
The way to shrink it back to a manageable size is with effective network security solutions, which in their own right require an evolution from legacy security appliances to a secure access service edge (SASE) architecture. The security inspection tools see everything on the network, not just logs.

CATO Networks
SEPTEMBER 27, 2017
These drivers, though, also come with baggage: the reassessment of todays corporate security model. Traditionally, Wide Area Networks (WANs) and network security were loosely coupled entities. Instead, we must bring networking and security disciplines closer together.

CATO Networks
JULY 22, 2015
A paralegal opened up a phishing email attachment and her, anti-virus protected, PC disk was maliciously encrypted by Cryptowall malware. The ransomware has to connect to its C2 (Command and Control) server to get the encryption key pair generated and the public key delivered to the machine. What is common to all of these capabilities?

Akins IT
OCTOBER 5, 2017
Security is at the forefront of every business owner and IT department. For as little as 25 cents a day, your organization can dramatically increase your networks security. Purchase and Implement Microsoft Enterprise Mobility and Security (about $0.25/user/day). Who doesnt love FREE? Train your end users (FREE).

Effective Software Design
JANUARY 8, 2025
MISP's data model is versatile and can represent a range of contextual objects, including those related to financial fraud, network security, and counter-terrorism. It implements role-based access and encryption to safely share sensitive data within trusted circles. Users can classify, tag, and develop custom taxonomies.
CATO Networks
OCTOBER 11, 2015
Applications spawned multiple security disciplines from two-factor authentication to secure app development, vulnerability scanning and web application firewalls. Databases introduced encryption and activity monitoring – and to manage all these capabilities we now have Security Information Event Management (SIEM) platforms.

CATO Networks
SEPTEMBER 13, 2020
In their August 2019 report The Future of Network Security Is in the Cloud, they wrote: This market converges network (for example, software-defined WAN [SD-WAN]) and network security services (such as SWG, CASB and firewall as a service [FWaaS]). The keyword in the original description of SASE is converges.

CATO Networks
OCTOBER 18, 2020
In its August 2019 report, The Future of Network Security Is in the Cloud, Gartner saw SASE (Secure Access Service Edge) as creating a single network for the complete enterprise, connecting and securing all edges everywhere. This adds unnecessary latency to the network.

CATO Networks
MAY 23, 2024
Researchers have labeled this technique ‘decloaking’ as while the VPN tunnel remains connected, it allows attackers to trick many VPN clients into sending traffic via a side channel and not through the encrypted tunnel. The attack requires introducing a rogue DHCP server to the local network.

CATO Networks
JUNE 19, 2018
Integrated Network Security SD-WAN edge solutions can provide direct Internet access at the branch. However, they typically do not include a full network security stack and require customers either to deploy additional security solutions at every location, backhaul traffic to a datacenter, or use cloud-based security services.

CATO Networks
OCTOBER 9, 2017
Previous recognition included Gartner Cool Vendor 2017 , a finalist as a RSA Innovation Sandbox 2017 , and CRN for 25 Coolest network Security Vendors. With all WAN and Internet traffic consolidated in the cloud, Cato applies a set of security services to protect all traffic at all times.

CATO Networks
JANUARY 27, 2022
A remote access virtual private network (VPN) is a solution designed to securely connect a remote user to the enterprise network. A remote access VPN creates an encrypted tunnel between a remote worker and the enterprise network. VPNs in general are designed to create an encrypted tunnel between two points.

CATO Networks
MARCH 8, 2017
But with Internet offload youll have another consideration — remote office network security. So we created a secured Internet access point for the company, backhauled Internet-bound traffic from offices across the WAN to that Internet hub, and minimized the need for branch security.

CATO Networks
JULY 4, 2023
(Were also getting our taste for speed through o ur partnership with the TAG Heuer Porsche Formula E Team , where Catos services ensure that Porsche has a fast, reliable, and secure network thats imperative for its on-track success.) This tops our previous milestone of up to 3 Gbps per tunnel.

CATO Networks
OCTOBER 1, 2024
In today’s digital age, where work from anywhere and hybrid cloud adoption are the norm, traditional network security perimeters have crumbled. IT organizations are using hybrid cloud strategies to combine the scalable, cost-effective public cloud with the secure, compliant private cloud.

CATO Networks
OCTOBER 31, 2018
All PoPs are interconnected using fully-meshed, encrypted tunnels to protect traffic once it is on the network. At the Edge Customers connect to Cato through encrypted tunnels established by appliance devices (called Cato Sockets); IPsec-enabled devices such as firewalls; or client software (for mobile users).
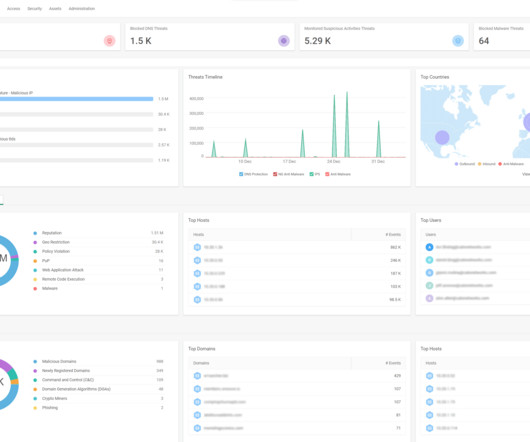
CATO Networks
APRIL 15, 2018
Since the beginning of networks, the lynchpin of network security has been the firewall. The first network firewalls appeared in the late 1980s, and gained almost universal acceptance by the early 1990s. FWaaS eliminates those issues by uniformly applying the security policy on all traffic, for all locations and users.

CATO Networks
JULY 24, 2017
This webinar will look at a range of issues including: Where SD-WAN can truly help network performance How to best use insertion and service chaining The security issues for any SD-WAN even with traffic being encrypted To sign up now, click here.

CATO Networks
JANUARY 11, 2021
With a VPN, all communication between the user and the VPN is encrypted. The encryption process takes time, and depending on the type of encryption used, this may add noticeable latency to Internet communications. This granular-level security is part of the identity-driven approach to network access that SASE demands.
CATO Networks
MARCH 19, 2018
For the past two years, Cato Networks has led a revolution in enterprise networking: the convergence of software-defined wide area networks ( SD-WAN ) and network security delivered as a single cloud service. For decades, networking and security evolved as silos, creating separate point products in each category.
CATO Networks
AUGUST 2, 2021
Understanding the 2021 Strategic Roadmap for SASE Convergence In July 2019, Gartner coined the term Secure Access Service Edge (SASE) to define the next generation of network security technology. SASE solutions acknowledge that modern networks and security challenges are very different from the past.

CATO Networks
MARCH 20, 2018
Security Encryption and segmentation are basic, must-have security features for any SD-WAN. To enhance network security, some providers offer security service insertion from a 3 rd party vendor. To enhance network security, some providers offer security service insertion from a 3 rd party vendor.

CATO Networks
NOVEMBER 30, 2021
IPS (Intrusion Prevention System) is a technology for securing networks by scanning and blocking malicious network traffic. By identifying suspicious activities and dropping packets, an IPS can help reduce the attack surface of an enterprise network. Read more about it in our ZTNA hub ).

CATO Networks
SEPTEMBER 2, 2021
SASEs built-in SD-WAN functionality offers network optimization, while the integrated security stack including Next Generation Firewall (NGFW), Secure Web Gateway (SWG), Zero Trust Network Access (ZTNA), and more secures traffic over the corporate WAN. SSL Secure Sockets Layer (SSL) is a predecessor to TLS.

CATO Networks
APRIL 2, 2025
Because advanced threat prevention still relies on an organizations existing security stack, this can create detection gaps and inconsistent enforcement for zero trust traffic. Its native capabilities work and evolve seamlessly together to provide a consistent and secure user experiencedelivering advanced zero trust security.
CATO Networks
NOVEMBER 14, 2022
Enhancing Your Enterprise Network Security Strategy | Webinar Legacy Firewall Security Solutions Cant Keep Up Zero-day threat detection is essential for protecting against modern cyber threats, but it is also resource-intensive.

CATO Networks
JANUARY 18, 2023
Employees need to be able to access corporate networks, resources, and data without fear of eavesdropping or other cyber threats. Historically, many organizations have relied upon VPNs to provide secure remote access. The problem is, however, that VPNs dont meet the business needs of the modern enterprise.

CATO Networks
DECEMBER 21, 2021
Encrypt Data, Not Just the Tunnel Most remote access solutions create an encrypted point-to-point tunnel to carry the communications payload. The data payload itself must also be encrypted for strong security. Security is still a considerable concern when VPNs are used. This is good, but not good enough.

CATO Networks
NOVEMBER 13, 2024
Success 1: Network Security Many machines, systems, and devices in use by manufacturers are vulnerable to cyberattack. Greater visibility, stronger security, and a leaner, more connected operation across the entire value chain. Key Challenges Standing Between Manufacturers and Industry 4.0

CATO Networks
APRIL 12, 2018
The encryption problem : Most enterprise traffic today is encrypted and data compression and deduplication are ineffective on encrypted traffic. Encrypted data cannot be compressed or deduplicated as it is already scrambled for security reasons.

CATO Networks
APRIL 28, 2022
the security side, Cato Security as a Service is a fully managed suite of enterprise-grade and agile network security capabilities, directly built into the Cato Global Private Backbone. Enterprises manage and monitor networking, security, and access through a single application. Is the integration seamless?

CATO Networks
AUGUST 4, 2016
While Nolles application refers to any business or infrastructure capability, I will use his principles to discuss what I believe is needed to deliver cloud-based network security as a service (NSaaS). NSaaS is making a network security stack available everywhere (i.e., Migration is one way to address process-to-need.

CATO Networks
MAY 5, 2016
MPLS isnt encrypted by default: MPLS relies on the carrier private network for security because the data doesnt flow on the public Internet. Generally speaking, no 3 rd party can be assumed to be 100% safe these days, so encryption should always be used for data in motion.
CATO Networks
DECEMBER 14, 2021
But in the new Management Application, weve enabled customization of the top-level view, enabling you to decide how much detail to show across all edges sites, remote users, and cloud assets connected to and are secured by Cato SASE Cloud (see Figure 1). Currently, Cato regulatory compliance verification includes HIPAA, PCI, and SOC 1-3.

CATO Networks
MAY 19, 2022
SD-WAN Receive a thorough exploration of a proposed vendors SD-WAN offering, covering link management, traffic routing and QoS, voice and latency-sensitive traffic, throughput and edge devices, monitoring and reporting, site provisioning, gradual deployment / co-existence with legacy MPLS networks.

CATO Networks
AUGUST 22, 2023
We optimized the service to set a record for SASE throughput from a single location at 5 Gbps with full encryption/decryption and security inspection. We had deployed massive global enterprises with the most demanding real-time and mission-critical workloads with sustained optimal performance and security posture.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content