What are VPN Tunnels and How do They Work
CATO Networks
DECEMBER 3, 2019
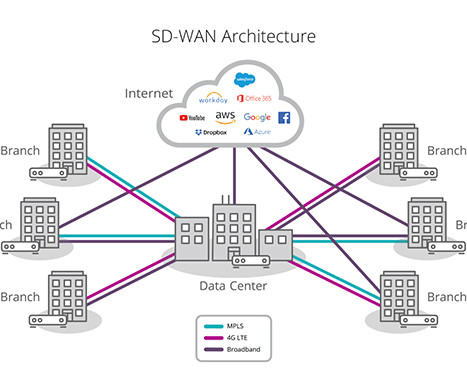
Virtual Private Networks (VPNs) have become one of the cornerstones of secure communications over the internet. However, there has been a lot of confusion around what VPNs can and cannot do. That confusion has led many technologists to choose a VPN solution that may not be well suited for their particular environment.






































Let's personalize your content