Enhancing the security of WhatsApp calls
Engineering at Meta
NOVEMBER 8, 2023
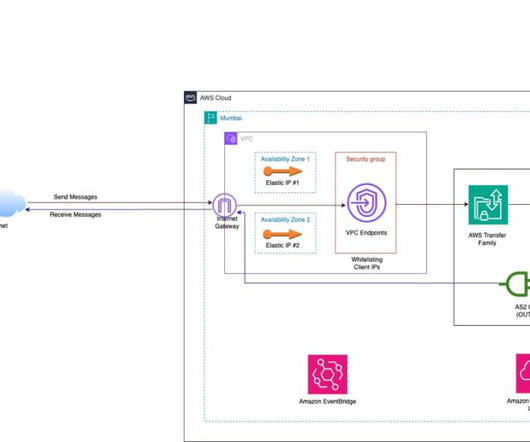
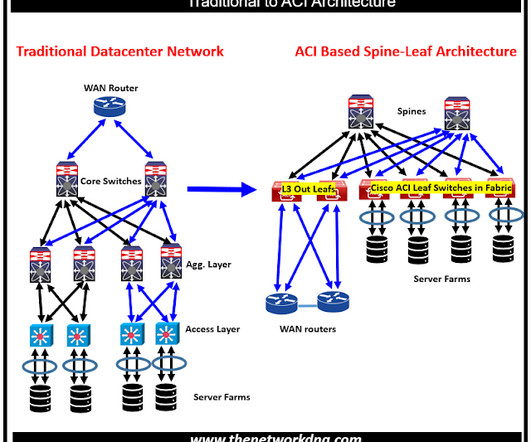
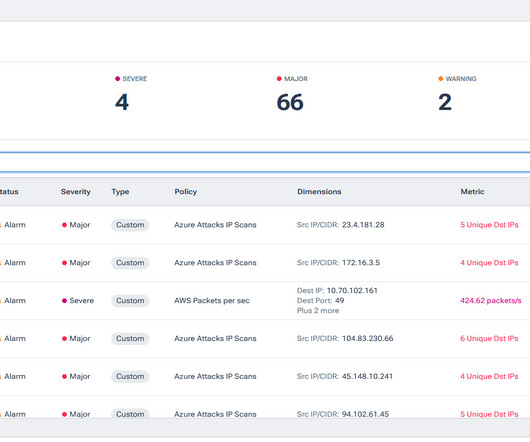
In addition to protecting personal messages with end-to-end encryption, WhatsApp empowers users to control their own privacy settings: from what you share, how you show up online, or who can reach out to you or add you to groups. Our implementation of silenced calls, with WhatsApp servers enforcing separation.





























Let's personalize your content