Cato CTRL Threat Research: Unmasking Hellcat – Not Your Average Ransomware Gang
CATO Networks
JANUARY 28, 2025
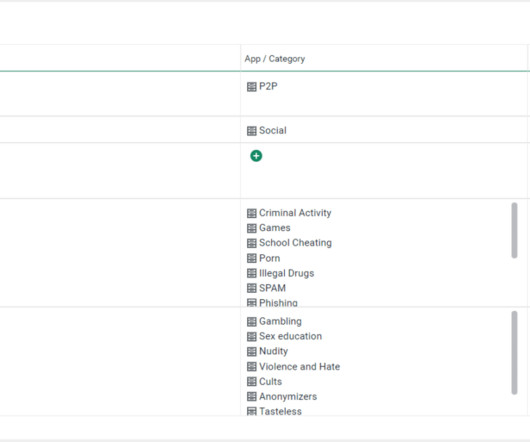
Executive Summary Theres a new ransomware gang targeting critical infrastructure, government organizations, educational institutions, and energy sectors. Iraq City Government (December 1, 2024) Figure 5. This was not the first time the Iraqi government had been targeted. Their name? But who exactly are they?



















Let's personalize your content