Unyielding Defense: Cisco Firewall Achieves AAA Rating From SE Labs
Cisco Wireless
MARCH 11, 2025
See how Cisco Secure Firewall excelled in the SE Labs test, blocking advanced attacks with innovative threat intelligence and encryption capabilities.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Cisco Wireless
MARCH 11, 2025
See how Cisco Secure Firewall excelled in the SE Labs test, blocking advanced attacks with innovative threat intelligence and encryption capabilities.

Cisco Wireless
FEBRUARY 26, 2025
While encryption enhances security by protecting data integrity and privacy, it also poses challenges. Cisco Secure Firewall helps keep encrypted traffic safe.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CloudFaire
APRIL 9, 2025
This is why the first thing that happens when you deploy a new secret to Cloudflare is encrypting the secret prior to storing it in our database. This is done by making use of DEKs (Data Encryption Keys) to encrypt your secrets and a separate KEK (Key Encryption Key) to encrypt the DEKs themselves.

Network Engineering
JULY 25, 2016
no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption !
CATO Networks
SEPTEMBER 22, 2022
A growing percentage of Internet traffic is protected by encryption. According to Google , approximately 95% of web browsing uses the encrypted HTTPS protocol. This trend toward traffic encryption has been driven by a few different factors. The move toward data encryption is a mixed blessing for cybersecurity.

The Network DNA
FEBRUARY 21, 2025
Driven by the Cisco Silicon One E100 ASIC, Cisco Smart Switches provide high speed connection, rich telemetry, line-rate encryption and power economy for contemporary data center operations. Cisco Hypershield will only support L4 stateful firewalling at launch. These Smart Switches with the AMD DPUs offer 800G service throughput.
CATO Networks
DECEMBER 14, 2017
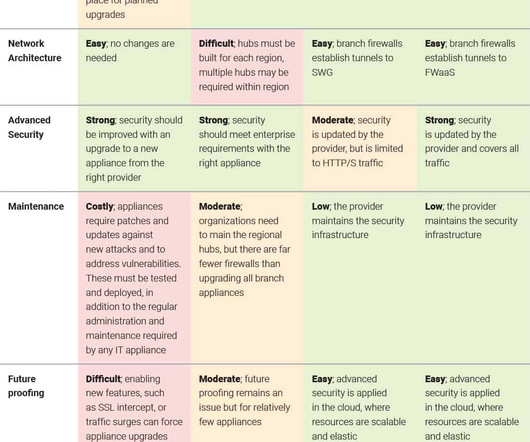
The growing amount of encrypted traffic coupled with the security appliances limited processing power is forcing enterprises to reevaluate their branch firewalls. The appliances simply lack the capacity to execute the wide range of security functions, such as next-generation firewall (NGFW) and IPS, needed to protect the branch.

CloudFaire
MARCH 24, 2025
Take control of public AI application security with Cloudflare's Firewall for AI Firewall for AI discovers and protects your public LLM-powered applications, and is seamlessly integrated with Cloudflare WAF. It explains how to do lattice-based encryption and authentication from scratch.

Akins IT
NOVEMBER 22, 2019
SECURING YOUR AZURE VIRTUAL NETWORK WITH A NEXT GENERATION FIREWALL PART 4: ROUTING, FIREWALL POLICIES, AND SECURITY PROFILES User Defined Routes (UDR) By default, Azure networks automatically generate system routes for connectivity between subnets within a VNET. A default route of 0.0.0.0/0

Packet Pushers
SEPTEMBER 23, 2022
Encrypted traffic poses a problem for enterprise policy enforcement. On today's Heavy Networking, we explore the notion of zero knowledge middleboxes, which use a variety of techniques to allow firewalls or other middleboxes to enforce policy without the need for decryption.

Akins IT
JULY 30, 2019
NEXT GENERATION FIREWALL MUST-HAVE FEATURES PART 2: SSL DECRYPTION In todays digital age, security has become tantamount to success in ensuring business continuity. DEEP-PACKET SSL INSPECTION Its now estimated that over 70% of traffic is now SSL encrypted. STAY TUNED NEXT WEEK FOR PART 3: MALWARE/IPS PREVENTION.

Packet Pushers
MARCH 9, 2020
Let's Encrypt revokes millions of digital certs, Microsoft proposes SMB over QUIC for file access without a VPN (and an easier way to get through firewalls), big vendors offer extended free trials of conferencing software for companies considering remote work, Microsoft pays hourly workers full salaries during work slowdowns, and more.

CATO Networks
JANUARY 28, 2025
Attacks targeting firewalls and critical infrastructure, as evidenced in the attacks against a U.S. Double extortion to exfiltrate data before encrypting target systems. university and French energy distribution company. Privilege escalation to root or admin levels.
CATO Networks
APRIL 15, 2018
Since the beginning of networks, the lynchpin of network security has been the firewall. The first network firewalls appeared in the late 1980s, and gained almost universal acceptance by the early 1990s. So what is a Firewall as a Service and why do you need it? FWaaS is a new type of a Next Generation Firewall.

Engineering at Meta
NOVEMBER 8, 2023
In addition to protecting personal messages with end-to-end encryption, WhatsApp empowers users to control their own privacy settings: from what you share, how you show up online, or who can reach out to you or add you to groups. In end-to-end encrypted messengers like WhatsApp, clients are the source of truth.
Akins IT
OCTOBER 17, 2017
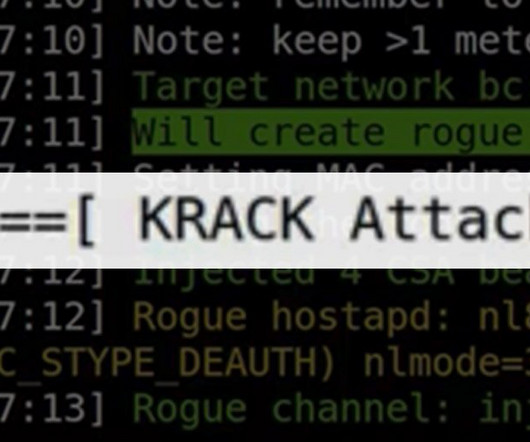
Its important to understand how this large scale wireless encryption exploit operates and how you can take preventative measures to protect your network from the KRACK exploit and future security compromises to come. WPA and WPA2, an otherwise ubiquitous wireless encryption standard was at the center of the exploit. Always use a VPN.

CloudFaire
DECEMBER 27, 2024
our privacy-preserving DNS resolver, and protect your devices network traffic via WARP by creating a private and encrypted tunnel to the resources youre accessing, preventing unwanted third parties or public Wi-Fi networks from snooping on your traffic. Thats a lot of acronyms, so let's make sure those are clear.
Network Engineering
JANUARY 1, 2025
Is there some other (easier) way to extract the SK_ei and SK_er keys from a running VM-Series firewall? 483): For encrypted key(len=57): 2025-01-01 02:33:50.039 -0800 debug: pan_cryptod_dump_buf(pan_cryptod_sysd_api.c:767): I still see lots of [DUMP] messages but I cannot make sense of them without the [DEBG] context. rcf_read start.

DoorDash Engineering
NOVEMBER 29, 2022
The data transfer between DoorDash and payment processors needs to be encrypted to protect customers’ privacy and sensitive data. Under the hood, the Site-to-Site VPN creates two security IPsec tunnels, where data can be encrypted and transmitted over the public Internet. This means the packet still fails the firewall rules.

Akins IT
FEBRUARY 13, 2023
Use encryption: Try using encrypted email services or install an encryption plugin for your email client to protect the content of your emails from being intercepted or read by unauthorized individuals. Sometimes these can be difficult to spot, so always take a close look at both the email and its source.
CATO Networks
JUNE 4, 2024
Security Settings Since Cato is a complete SASE solution, it includes such features as firewall-as-a-service, intrusion protection, anti-malware, and application control to name a few. Machine learning then uses this information to match different features of both harmless and malicious files.

CATO Networks
JANUARY 29, 2018
The Risk of Crypto Mining and What You Can Do Crypto mining is the validating of bitcoin (or other cryptocurrency) transactions and the adding of encrypted blocks to the blockchain. Preferably, this should be done using the deep packet inspection (DPI) engine in your firewalls. Cato Research Labs recommends blocking crypto mining.

CATO Networks
MAY 24, 2016
The private nature of MPLS allowed an organization to not encrypt MPLS traffic, a big benefit in terms of encryption key management and required CPE (customer premise equipment) capabilities. The immediate concern is encrypting the internet tunnel of the SD-WAN solution. However, SD-WAN or MPLS arent security solutions.
NW Kings
JANUARY 14, 2025
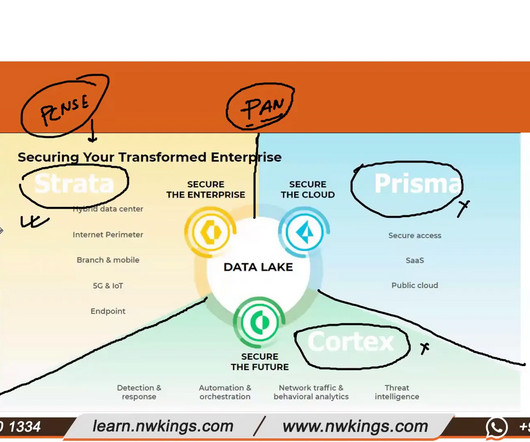
Strata Strata is the central firewall product of Palo Alto Networks. These firewalls are specifically designed for installation in different environments like data centers, hybrid cloud setups, and remote branches. Types of Licenses Base License: Provides essential firewall functionalities.

CATO Networks
SEPTEMBER 27, 2017
Any SD-WAN should build a virtual overlay of encrypted tunnels between locations. The SD-WAN make configuring this mesh of tunnels simple, managing the encryption keys, creating the tunnels, and automating their full mesh setup. The most common way to deliver threat protection at a branch is to deploy a local firewall or UTM appliance.
CATO Networks
DECEMBER 3, 2019
VPNs encapsulate data and encrypt the data using an algorithm contained within the transmission protocol. VPN traffic is encrypted and decrypted at the transmission and receiving ends of the connection. VPNs can also be set up using L2TP/IPsec protocols, which proves to have much stronger encryption than PPTP.
Kentik
MARCH 19, 2020
In many infrastructures, the inflection points are at the network edge, where VPN gateways authenticate and encrypt remote-access traffic. The richest data sources are from the VPN devices or firewalls. Kentik provides an easy way to see not only the entire network but also how it’s being used.

CATO Networks
OCTOBER 31, 2018
Convergence enables Cato to collapse multiple security solutions such as a next-generation firewall, secure web gateway, anti-malware, and IPS into a cloud service that enforces a unified policy across all corporate locations, users and data. Customers can selectively enable the services, configuring them to enforce corporate policies.
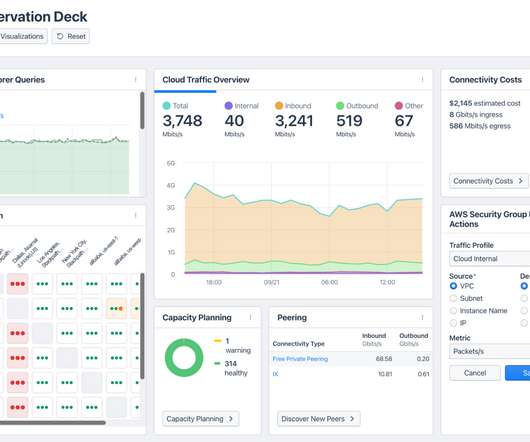
Kentik
FEBRUARY 8, 2023
Correlate the data with other information, such as firewall logs, threat intelligence feeds, and endpoint security data. Detect and alert on non-encrypted traffic. Your network observability solution can help you detect security incidents or malicious threats by analyzing network telemetry for unusual traffic spikes or patterns.
CATO Networks
OCTOBER 18, 2017
Build around secure hardware: If COGS permits, build security features such as secure and encrypted storage, or boot functionality based on Trusted Platform Module (TPM). The built-in next generation firewall (NGFW) and firewall as a service (FWaaS) protects mobile users and locations from external threats.
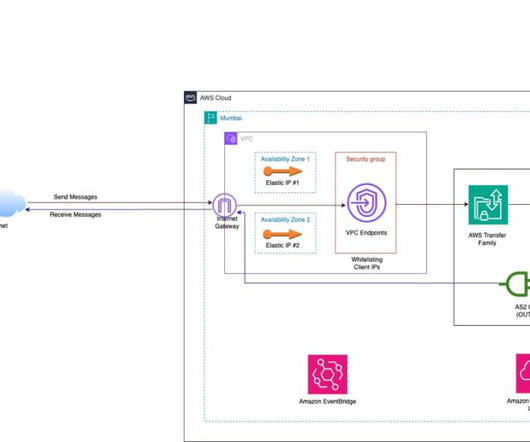
AWS Architecture
JANUARY 13, 2025
B2B integration over the AS2 protocol can be challenging, such as with trading partner onboarding, AS2 EDI integration, firewall configuration, certificate maintenance, and high licensing costs for commercial AS2 solutions. The EDI contains details like customer name, date, source location, destination location, and more.

CATO Networks
FEBRUARY 13, 2017
There is no native encryption with MPLS services; data is sent in the clear. Instead of WAN security they built a closed environment, protecting the WAN from the Internet with a perimeter firewall. Attackers can get past firewalls and, without segmentation, will spread from an obscure field office across the entire enterprise.

CATO Networks
NOVEMBER 1, 2019
One sticking point has always been the branch network stack: deploying, configuring, managing, and retrieving the router, firewall, WAN optimizer, etc., Cloud Stack Benefits the Enterprise: Freedom and Agility People want a lot out of their SD-WAN solution: routing, firewalling, and WAN optimization, for example. Please see figure 1.)

CATO Networks
SEPTEMBER 2, 2021
SASEs built-in SD-WAN functionality offers network optimization, while the integrated security stack including Next Generation Firewall (NGFW), Secure Web Gateway (SWG), Zero Trust Network Access (ZTNA), and more secures traffic over the corporate WAN. According to Gartner (that coined the term), SASE is the future of network security.

CATO Networks
MAY 24, 2022
Running virtual firewalls in Azure adds complexity and considerable expense, necessitating purchase of additional cloud compute resources and third-party licenses. Whats more, virtual firewalls are limited in capacity, requiring upgrades as traffic grows. First, how do you secure your Azure instance?

CATO Networks
SEPTEMBER 13, 2020
In their August 2019 report The Future of Network Security Is in the Cloud, they wrote: This market converges network (for example, software-defined WAN [SD-WAN]) and network security services (such as SWG, CASB and firewall as a service [FWaaS]). The firewall needs to know how to process the traffic based on numerous policies.
CATO Networks
NOVEMBER 21, 2017
At the core of NFV is the notion that network functions, such as SD-WAN , firewalling and secure web access, can be delivered as virtual appliances and run either on premises (vCPE) or at the carrier core data centers (hosted). These may be any network function, such as SD-WAN, firewalls, IPS/IDS, secure web gateways and routers.

CATO Networks
FEBRUARY 19, 2018
for Arlington Orthopedics , one of the largest orthopedic practices in North Texas, With our firewall, we would have only been able to block Netflix, and that was my knee-jerk reaction, but then whoever was watching Netflix would switch to another network. Decrypting and re-encrypting traffic has no impact on Cato Cloud performance.

CATO Networks
JULY 4, 2023
Earlier last month, we announced that Cato reached a new SASE throughput record , achieving 5 Gbps on a single encrypted tunnel with all security inspections fully enabled. Companies need encrypted, secure high throughput between their clouds or to the central data centers in their hybrid deployments.

CATO Networks
APRIL 28, 2022
Current security services include firewall-as-a-Service (FWaaS) , secure web gateway with URL filtering ( SWG ), standard and next-generation anti-malware (NGAM), IPS-as-a-Service (IPS), and Cloud Access Security Broker (CASB) , and a Managed Threat Detection and Response (MDR) service. How is sensitive data handled?

CATO Networks
MAY 15, 2017
Once installed, the ransomware encrypts the files on the machine. Disrupt WannaCrypt communications with the Internet Firewall. Figure 3: By configuring Catos Internet Firewall to block TOR traffic, IT managers disrupt communications back to C&C servers. Victims are asked to pay $300 to remove the infection (see Figure 1).

CATO Networks
JUNE 4, 2017
A combination of an encrypted software-defined overlay across all backbones, application-aware routing, and the gathering of latency and loss statistics from each backbone allows the UberNet to select the optimum route network any application at anytime. The competition among backbone suppliers and the nature of IP minimizes costs.

CATO Networks
JANUARY 11, 2021
With a VPN, all communication between the user and the VPN is encrypted. The encryption process takes time, and depending on the type of encryption used, this may add noticeable latency to Internet communications. Performance can be an issue.
CATO Networks
MARCH 19, 2018
Security in the context of SD-WAN was needed to encrypt the SD-WAN overlay tunnels over the Internet. Software and cloud must form the core of the network We live in a world of appliances routers, SD-WAN, WAN optimization, and next-generation firewalls to name a few. They had the vision and the track record.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content