Eye-Opening Results from Forrester’s Cato SASE Total Economic Impact Report
CATO Networks
MARCH 10, 2022
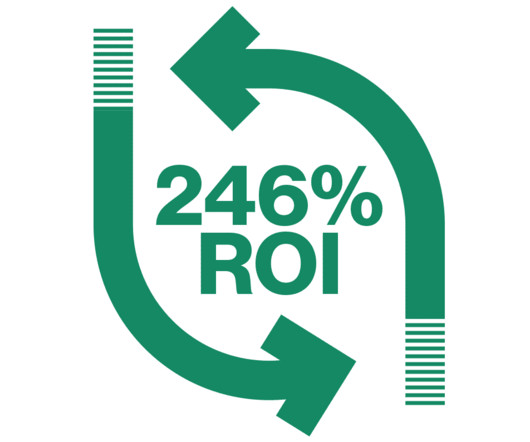
We decided it was time to quantify Cato SASEs real-world financial benefit with a recognized, well-structured methodology, so we commissioned a Total Economic Impact (TEI) study with the consulting arm of the leading analyst firm Forrester. Overall, respondents describe a transformative, before/after experience. with 40 sites across the U.S.,











Let's personalize your content