The Top 4 Industry 4.0 Challenges and How SASE Helps Manufacturers Overcome Them
CATO Networks
NOVEMBER 13, 2024
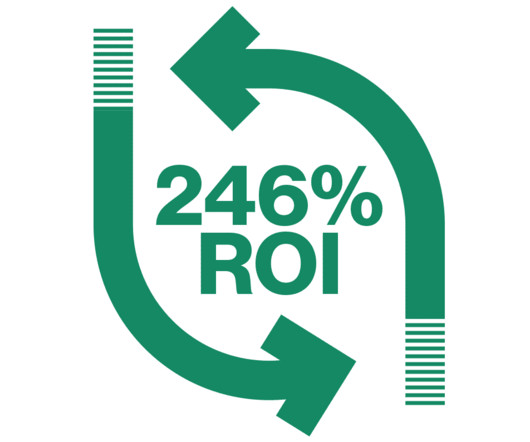
This blog post highlights four of the most prominent onesbased on real experiences from Catos manufacturing customersand how SASE helps tackle them head-on. 3: High Operational Costs Disparate network and security point solutions create a financial and operational burden. Cato is the leader in single-vendor SASE. investments.












Let's personalize your content