Navigating the Digital Operational Resilience Act
Cloudera Blog
APRIL 18, 2024
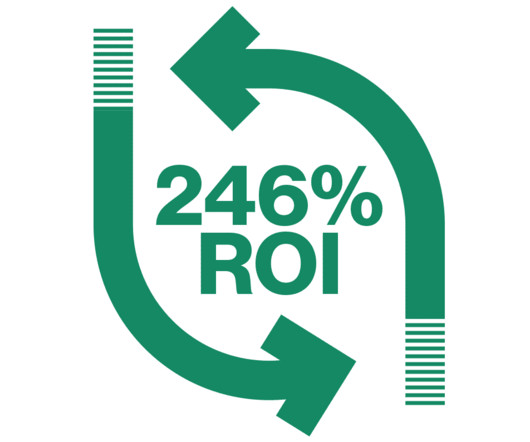
In the financial sector, regulations are essential for financial institutions to maintain stability by preventing excessive risk-taking, ensuring adequate capitalization and reducing the likelihood of failures or financial crises. What is DORA?


















Let's personalize your content