Cato Protects Against CVE-2023-23397 Exploits
CATO Networks
MARCH 22, 2023
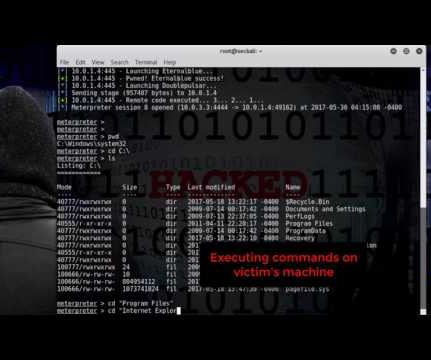
An attacker can craft a.MSG file as a e form of a calendar invite that triggers an authentication attempt over the SMB protocol to an attacker-controlled endpoint without any user interaction. (.MSG MSG is the file format used to represent Outlook elements, such email messages, appointments, contacts, and tasks.)











Let's personalize your content