WannaCry II: How to Stop NotPetya Infections with the Cato Cloud
CATO Networks
JUNE 29, 2017
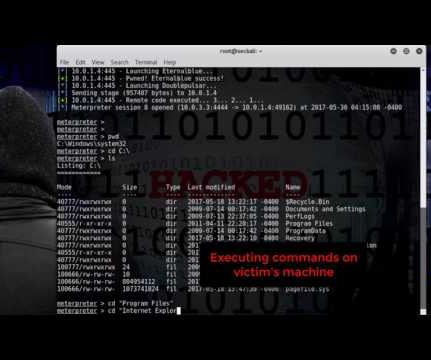
Like WannaCry, NotPetya leverages the SMB protocol to move laterally across the network, an EternalBlue exploit attributed to the National Security Agency (NSA) and leaked by the Shadow Brokers hacking group last April. The machine is then forced to reboot, encrypting the files and locking the computer. A total of 3.8









Let's personalize your content