Introducing Apache Kafka® 3.8
Confluent
JULY 29, 2024
Apache Kafka 3.8 adds 17 new KIPs (13 for Core, 3 for Streams & 1 for Connect). Highlights include 2 new Docker images, the ability to set task assignors, and more!

Confluent
JULY 29, 2024
Apache Kafka 3.8 adds 17 new KIPs (13 for Core, 3 for Streams & 1 for Connect). Highlights include 2 new Docker images, the ability to set task assignors, and more!
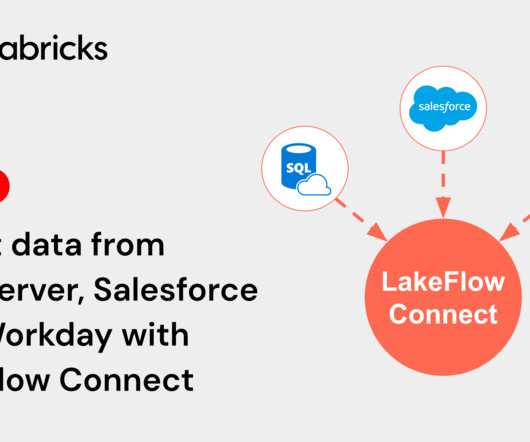
databricks
JULY 31, 2024
We’re excited to announce the Public Preview of LakeFlow Connect for SQL Server, Salesforce, and Workday. These ingestion connectors enable simple and efficient.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

InfoQ Articles
JULY 29, 2024
By explaining the roles of an architect and the concept of connecting levels, Gregor Hohpe delves into the importance of metaphors for making complex technical concepts more relatable and sketches for abstracting and capturing the essence of complex systems.
The Network DNA
JULY 31, 2024
CCNA: IP Routing (Communication between two different networks) In this article, we are going to talk about IP routing which is a process of communication between two different networks. This communication could be between two different VLANs in a switching environment. In one of the articles , we talk about layer 2 switching where switches build the MAC address table to decide where to forward frame based on the destination MAC address.

Confluent
JULY 30, 2024
Confluent Platform 7.
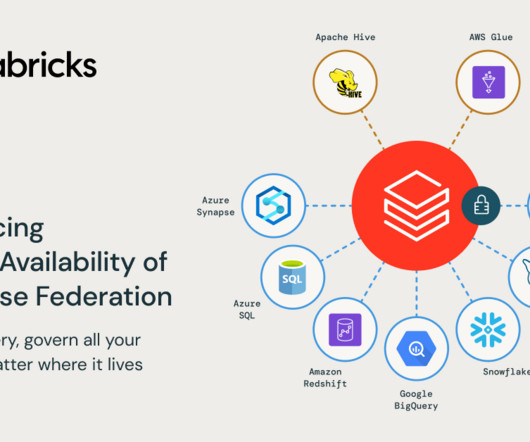
databricks
AUGUST 1, 2024
Today, we are excited to announce that Lakehouse Federation in Unity Catalog is now Generally Available (GA) across AWS, Azure, and GCP! Lakehouse.

CATO Networks
JULY 30, 2024
The Role of the CISO Post-Pandemic The world has evolved and the on-going momentum of Cloud and Work-From-Anywhere (WFA) has become unstoppable. CISOs have realized their traditional security architectures, specifically VPNs, are no longer adequate to ensure only authorized users have access to critical resources. This has made the role of CISO ever more important because we now have applications everywhere and people everywhere, leading to increased cyber threats everywhere.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

Confluent
AUGUST 2, 2024
BT Group's Smart Event Mesh - centralized event streaming with decentralized customer experience, automation, and a foundation—all built on Confluent.
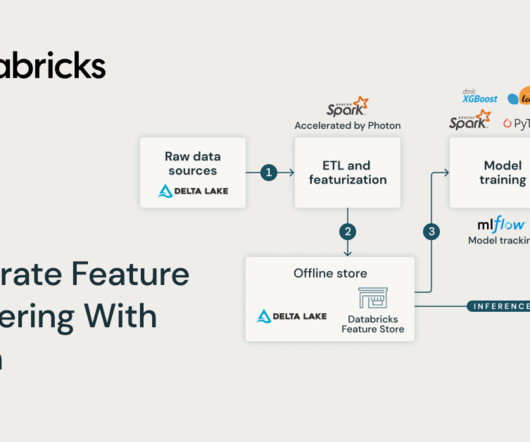
databricks
AUGUST 2, 2024
Training a high-quality machine learning model requires careful data and feature preparation. To fully utilize raw data stored as tables in Databricks, running.

Apium Hub
JULY 31, 2024
Apiumhub, a leading provider of software development services, today announced it has been named among the top IT services companies in 2024 by Techreviewer.co, a respected industry publication. This recognition is a testament to Apiumhub’s dedication to helping businesses achieve their digital transformation goals by delivering innovative, high-quality software solutions.

Packet Pushers
AUGUST 2, 2024
AI is making its way into network automation. Maybe the thought of a hallucinating ChatGPT getting its six-fingered hands on your network makes you want to run the other way. But the story of AI for IT operations is more nuanced than the hot takes we get about the confidently dumb results that Large Language. Read more » AI is making its way into network automation.

Confluent
JULY 29, 2024
Learn how to use Flink SQL on Confluent Cloud to invoke ML and GenAI endpoints to enrich streaming data
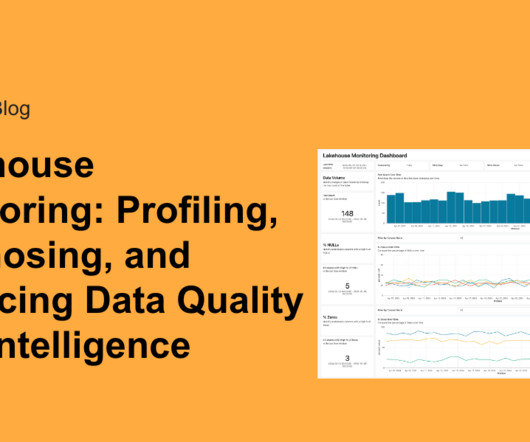
databricks
AUGUST 1, 2024
At Data and AI Summit, we announced the general availability of Databricks Lakehouse Monitoring. Our unified approach to monitoring data and AI.

Heroku
JULY 29, 2024
In todays fast-paced digital world, companies are looking for ways to securely expose their APIs and microservices to the internet. MuleSoft Anypoint Flex Gateway is a powerful solution that solves this problem. Let's walk through deploying the Anypoint Flex Gateway on Heroku in a few straightforward steps. You'll learn how to connect your private APIs and microservices on the Heroku platform through the Anypoint Flex Gateway and the Anypoint API Manager , without the hassle of managing infrastr

AWS Architecture
JULY 31, 2024
The design of cloud workloads can be a complex task, where a perfect and universal solution doesnt exist. We should balance all the different trade-offs and find an optimal solution based on our context. But how does it work in practice? Which guiding principles should we follow? Which are the most important areas we should focus on? In this blog, we will try to answer some of these questions by sharing a set of resources related to the AWS Well-Architected Framework.

Confluent
AUGUST 2, 2024
Apache Flink 1.
databricks
JULY 28, 2024
The transformative potential of artificial intelligence (AI) is undeniable. From productivity efficiency, to cost savings, and improved decision-making across all industries, AI is.

Rule 11
AUGUST 1, 2024
Looking at changes in the market in the last ten years, it certainly seems like vendors work less toward innovation and more towards locking customers in to revenue streams. Chris Emerick, Dave Taht, and Russ White decided it’s time to talk about. What’s wrong with vendors? And since everything can’t be wrong with vendors, where are they doing the right thing?

Dataversity
AUGUST 1, 2024
Welcome to the latest edition of Mind the Gap, a monthly column exploring practical approaches for improving data understanding and data utilization (and whatever else seems interesting enough to share). Last month, we explored the rise of the data product. This month, we’ll look at data quality vs. data fitness. Everybody likes a pithy definition. Marketers describe […] The post Mind the Gap: Data Quality Is Not “Fit for Purpose” appeared first on DATAVERSITY.

AWS Architecture
AUGUST 1, 2024
In Aotearoa New Zealand, we have been listening and learning to better understand Mori aspirations when using cloud technology. We have been learning from Mori customers, partners, and advisors who have helped us on this journey. A common theme was how to safeguard Mori data in a digital world. Together with a group of Mori advisers, we are excited to introduce the first iteration of a Mori Data Lens for the AWS Well-Architected Framework.

databricks
JULY 30, 2024
Introduction An organization adopting new technologies or on a modernization journey typically focuses on upcoming tools, their features and potential performance/cost improvements under.

Obkio
AUGUST 2, 2024
Learn to use network optimization and monitoring to optimize network performance, improve your end-user experience, and compare performance from the past.

Dataversity
JULY 29, 2024
The consumer privacy landscape is constantly evolving. Potential regulations like the American Data Privacy and Protection Act (ADPPA), which resemble current laws set forth by the General Data Protection Regulation (GDPR), are keeping marketers on their toes. Meanwhile, other major trends dictating how and when marketers interface with consumer data are on the horizon (such […] The post Data Privacy Compliance Is an Opportunity, Not a Burden appeared first on DATAVERSITY.

VIAVI Solutions
AUGUST 1, 2024
Bridges, tunnels, pipelines, telecom networks, electrical power transmission lines and other civil structures form the backbone of modern societies, facilitating essential services and connectivity. Ensuring the safety and integrity of these structures is of paramount importance. Thankfully, advancements in technology have led to innovative solutions for infrastructure monitoring, with fiber sensing technology emerging as a […] The post Enhancing Infrastructure Health & Security with

databricks
JULY 29, 2024
Financial Valuations & Comparative Analysis Financial institutions specialized in capital markets such as hedge funds, market makers and pension funds have long been.

Packet Pushers
JULY 31, 2024
Today, Lexie Cooper shares her journey from a NOC environment to networking engineering in the aerospace industry. Along the way, the discussion makes stops at the importance of medium skills, and the role of humor and relatability in attracting and educating younger professionals in networking. Finally, Lexie relates her challenges when working on the New.

Dataversity
JULY 29, 2024
Implementing a successful data governance program is essential for any organization that wants to manage its data effectively. However, these programs can sometimes fail, often due to issues related to key business drivers. In the pursuit of effective data management, many organizations overlook the practical realities and challenges that can significantly impact their success.

Slipstick
JULY 31, 2024
Questions and answers on Microsoft Outlook.com disabling basic authentication and requiring modern authentication. What will work after September 16 2024? The post Outlook.com and Modern Authentication Questions appeared first on Slipstick Systems.
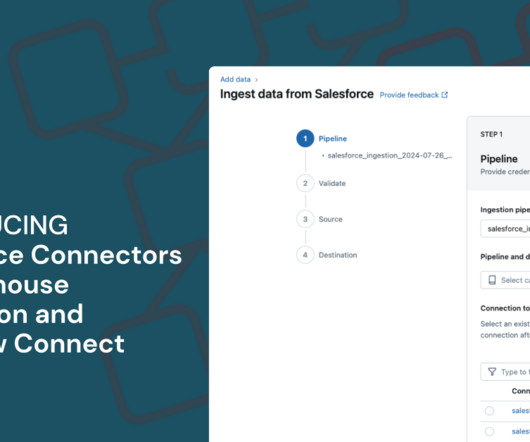
databricks
JULY 31, 2024
We are excited to announce a range of new integrations that will allow our customers to access and derive insights from their data.

Packet Pushers
JULY 30, 2024
When choosing vendors, what strategy should you employ: big rock, best-in-breed, or ecosystem? The big rock approach consolidates vendor relationships around a few strategic partners. Best-in-breed focuses on selecting top solutions from various vendors. The ecosystem model combines elements of both. Today’s conversation explores all three models and also highlights the importance of integration, the.

Dataversity
AUGUST 2, 2024
In today’s digital age, vast amounts of business data are gathered from different sources. Even when organizations strategically invest in analytics tools, they still face challenges in the form of data silos, unstructured data management, and failure of business-driven insights from tools. To combat these challenges, more businesses are revamping with data strategy to seamlessly […] The post A Deep Dive into Data Strategy: Accelerating AI Adoption for Businesses appeared first on DATAVERS

VIAVI Solutions
JULY 29, 2024
Observability is all about leveraging diverse data sources, including flow, packet data, and metrics, to better understand what is happening inside the network, and what is likely to happen in the future. Therefore, it would not be surprising if more monitoring tools equated to more data and enhanced network observability, but that is not always […] The post Redesigning the Observability Toolkit appeared first on VIAVI Perspectives.

Developer to Architect
JULY 28, 2024
In Lesson 190 I talked about the difference between a logical and physical architecture. In this lesson I demonstrate a technique for identifying initial core logical components called the Workflow approach. The workflow approach is useful when you have basic knowledge of the major paths a user might take though the system, allowing you to identify key actions, and from those actions identify the initial core logical components of the system.

Packet Pushers
JULY 30, 2024
In the wake of one of the largest global IT outages, resiliency is the theme of today’s show. We dig into the CrowdStrike debacle as well as an Azure outage that kinda flew under the radar. We also look at the Resiliency Planning Framework Playbook from CISA and other frameworks for building resilient infrastructure. We. Read more » In the wake of one of the largest global IT outages, resiliency is the theme of today’s show.

Dataversity
JULY 31, 2024
Today’s business landscape continues to become more data-driven. The fact is that the quality of enterprise data defines modern organizations. Business growth stems from proficient data management and analysis. For organizations to thrive, it’s critical for an efficient data archival solution to be in place to satisfy customer demands and attain company goals.

CATO Networks
JULY 28, 2024
A vision born from complexity Most security companies grow reactively, a continuous, complex cycle of funding and building point solutions to address emerging point problems. Cato Networks chose to revisit and address two decades of accumulated complexities in networking and security infrastructures, looking to finally solve and break the point problem, point solution cycle.

Rule 11
JULY 27, 2024
Recent events involving CrowdStrikes Falcon security software have underscored a critical lesson across the industry: the importance of having a robust, secure release process. My analysis of the event has a lot of similarities with my reflections on the Optus outage last year, the incident underscores the critical issue of resilience in IT infrastructure, particularly in systems that lack diversity.
Let's personalize your content