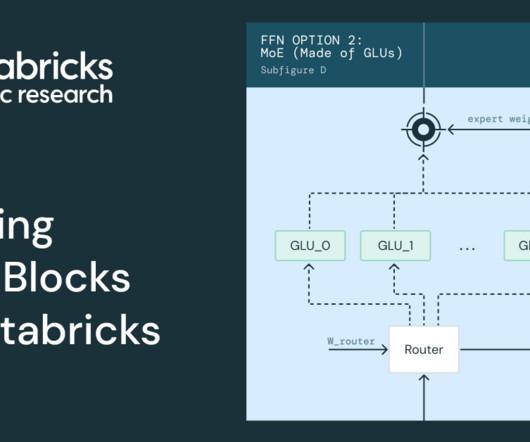
Bringing MegaBlocks to Databricks
databricks
APRIL 9, 2024
At Databricks, we’re committed to building the most efficient and performant training tools for large-scale AI models. With the recent release of DBRX.
databricks
APRIL 9, 2024
At Databricks, we’re committed to building the most efficient and performant training tools for large-scale AI models. With the recent release of DBRX.

InfoQ Articles
APRIL 10, 2024
This article focuses on the increasing adoption of data-driven testing in Java enterprise applications and sheds light on the Data and NoSQL Jakarta specifications. It highlights the significance of modern testing libraries such as JUnit Jupiter and AssertJ and emphasizes the importance of container-based frameworks like Testcontainers in enhancing testing practices.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cloudera Blog
APRIL 11, 2024
Businesses around the world rely on an extensive network of partnerships to deliver quality customer experiences—and it’s no different here at Cloudera. Cloudera is building a robust partner ecosystem to meet the unique needs of its customers, working to provide exceptional and fulfilling experiences that help make Cloudera a leader in the multi-cloud data platform space.

Engineering at Meta
APRIL 10, 2024
We are sharing details of our next generation chip in our Meta Training and Inference Accelerator (MTIA) family. MTIA is a long-term bet to provide the most efficient architecture for Meta’s unique workloads.

databricks
APRIL 8, 2024
We're excited to announce that Databricks has been honored with the 2024 Google Cloud Technology Partner of the Year award for Data -.
InfoQ Articles
APRIL 9, 2024
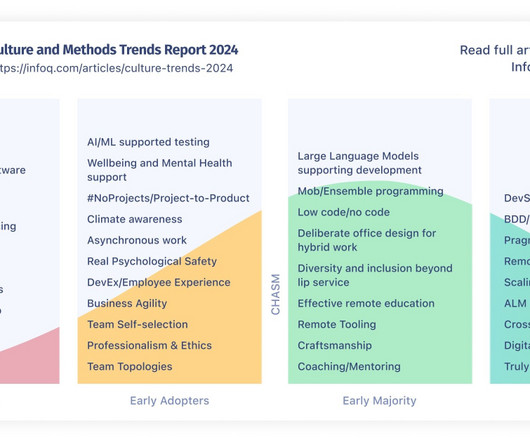
The Culture and Methods trends report discusses evolving roles within teams, the way the staff plus roles are able to add value, the use and misuse of DevEx metrics, how remote work continues to evolve, a lack of diversity is still a challenge, and the need to move from climate change awareness to climate conscious software engineering By Shane Hastie, Jutta Eckstein, Ben Linders, Susan McIntosh, Rafiq Gemmail, Craig Smith

Confluent
APRIL 10, 2024
Learn what happens behind the scenes in Apache Kafka producer and consumer clients when communicating with Schema Registry and serializing/deserializing messages.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.
databricks
APRIL 8, 2024
Large language models (LLMs) have generated interest in effective human-AI interaction through optimizing prompting techniques. “Prompt engineering” is a growing methodology for tailoring.

InfoQ Articles
APRIL 8, 2024
InfoQ encourages software practitioners and domain experts to submit full-length technical educational articles.

Dataversity
APRIL 12, 2024
In the contemporary landscape of data-driven decision-making, enterprises are increasingly turning to predictive analytics to gain valuable insights into future trends and behaviors. Predictive analytics involves extracting patterns from historical data to forecast future outcomes, enabling organizations to make proactive decisions and optimize their operations.

Engineering at Meta
APRIL 11, 2024
An engineer shares how his team is building the foundation for AI infrastructure at Meta, from physical data centers to training AI models.
databricks
APRIL 8, 2024
Fostering a paradigm shift towards a smarter, cleaner & reliable energy system Electricity is the new oil. Sources of energy are becoming more.

Packet Pushers
APRIL 12, 2024
With The Cathedral and the Bazaar as his guide, Srivats launched Ostinato, his open source project, in 2010. He needed an affordable network traffic generator at his day job, he was passionate enough to build one during his nights and weekends, and end users loved it it has been downloaded hundreds of thousands of times. Read more » With The Cathedral and the Bazaar as his guide, Srivats launched Ostinato, his open source project, in 2010.

Dataversity
APRIL 10, 2024
Have we ever seen something get adopted so quickly as generative AI (GenAI) compared to the past? Think about it: ChatGPT launched in 2022 and gained 100 million users in two months. In comparison, we have been hearing about AI for a few years, but the adoption rates of AI have varied from 25% to […] The post Maximizing Business Value with Generative AI appeared first on DATAVERSITY.

VIAVI Solutions
APRIL 12, 2024
The pace of innovation in telecommunications is accelerating, with the rollout of 5G technology underscoring an ever-present need: synchronization precision across networks. This is the first in a three-part series of articles that will delve into the criticality of 5G synchronization across three layers: transport, radio and resilience. Throughout the series, we will unravel why […] The post 5G Synchronization: Mastering Transport Layer Dynamics appeared first on VIAVI Perspectives.

databricks
APRIL 10, 2024
Image-generating technologies offer significant benefits for retail and consumer goods companies. By using generative models that produce both stylized and photo-realistic images from.
R&A
APRIL 12, 2024
Microsoft researchers published a very informative paper on their pretty smart way to let GenAI do 'bad' things (i.e. 'jailbreaking'). They actually set two aspects of the fundamental operation of these models against each other.

Dataversity
APRIL 12, 2024
The latest installment in our Q&A series with women leaders in data features Dr. Christina Sandema-Sombe, chief data steward of Nike, Inc. (Read our previous Q&A here.) Dr. Christina Sandema-Sombe first learned the joys – and challenges – of working with data as the global impact measurement lead at a humanitarian aid organization. Over a decade […] The post Women in Data: Meet Christina Sandema-Sombe appeared first on DATAVERSITY.

Obkio
APRIL 12, 2024
Network monitoring vs. management? We simplify your choice! Learn key differences & make the right choice to optimize your network & business operations.

Mixpanel
APRIL 12, 2024
You are a builder. And what makes you a builder is not just your ability to code, sketch an illustration, or write copy for a marketing campaign; it’s that you handle everything involved in taking an idea to a finished product. It’s agonizing over moving targets, considering new data, and even changing your mind on what you think is good. Building is decision-making.

CATO Networks
APRIL 11, 2024
For International Womens Day (March 8, 2024), the German language, software news site, entwickler.de , interviewed Cato product manager Shay Rubio about her journey in high tech. Heres an English translation of that interview : When did you become interested in technology and what first got you interested in tech? Im a curious person by nature and I was always intrigued by understanding how things work.

Dataversity
APRIL 11, 2024
At some point in your life, you’ve probably joined a gym. In doing so, you had to decide what type of membership was right for your fitness goals and at the right price point for your budget. Maybe it was an all-access pass, billed monthly or annually, with unlimited use of the facility, including the […] The post Managing Software Entitlements and Billing: How Usage Data Supports Streamlined Processes appeared first on DATAVERSITY.

Packet Pushers
APRIL 10, 2024
You cant just drop a knife on fish and expect there to be sushi. Jack Lindamood joins us today to share his metaphors and thoughts on picking the right IT tools and processes as outlined in his popular article, (Almost) Every Infrastructure Decision I Endorse or Regret after 4 Years Running Infrastructure at a Startup.. Read more » You cant just drop a knife on fish and expect there to be sushi.

Obkio
APRIL 10, 2024
Learn how the hostname of a traceroute hops can provide information about the real path from the source to the destination. Try Obkios Live Traceroute now!
CATO Networks
APRIL 10, 2024
Every year, Bonnaroo , the popular music and arts festival, takes over a 700-acre farm in the southern U.S. for four days. While the festival is known for its diverse lineup of music, it also offers a unique and immersive festival experience filled with art, comedy, cinema, and more. For the networking nerds among us, though, the festival might be even more attractive as a stress test of sorts.

Dataversity
APRIL 9, 2024
Kryder’s Law, named after Mark Kryder – the former SVP of research at Seagate Technology – is an observation comparable to Moore’s Law but specifically related to the area of magnetic disk storage. It posits that the density of information stored on magnetic disks is increasing exponentially, doubling approximately every 18 months. Kryder’s Law, much like Moore’s […] The post Why the Slowdown of Kryder’s Law Spells Urgency for Sustainable Archival Storage appeared first on DATAVERSITY.

Packet Pushers
APRIL 9, 2024
If your approach to firmware is that you dont bother it as long as it doesnt bother you, you might want to listen to this episode. Concerns about supply chain vulnerabilities are on the rise and for good reason: Attackers are targeting firmware because compromising this software can allow attackers to persist on systems after. Read more » If your approach to firmware is that you dont bother it as long as it doesnt bother you, you might want to listen to this episode.

Obkio
APRIL 9, 2024
Learn how to perform a network audit (network performance audit) to uncover issues before they cause havoc. Uncover Obkio's Network Audit Tool.

Noction
APRIL 9, 2024
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like EIGRP, OSPF, or ISIS, BGP establishes peering with other routers before exchanging routing information.

Dataversity
APRIL 8, 2024
Reusing data is a fundamental part of artificial intelligence and machine learning. Yet, when we collect data for one purpose, and use it for other purposes, we could be crossing both legal and ethical boundaries. How can we address the ethics of reusing data? Understand Your Data Before we address the issue of reuse, we […] The post Ask a Data Ethicist: How Can We Address the Ethics of Reusing Data?

Packet Pushers
APRIL 8, 2024
Take a Network Break! This week we start with some FU on Juniper’s Mist AI, the ConnectWise vulnerability, and the 25th anniversary of the Cisco Cat6. The US Cybersecurity & Infrastructure Security Agency (CISA) has proposed new rules that require organizations to report security incidents within 72 hours and ransomware payments within 24 hours.

Obkio
APRIL 8, 2024
Embrace a network monitoring with our thrilling list of the top 29 Auvik alternatives for 2025. From open-source to enterprise & performance monitoring.

Noction
APRIL 7, 2024
In networking, ACK and NACK mechanisms play crucial roles in ensuring reliable data transmission. Dive into this insightful article to understand how these mechanisms work and their significance in maintaining network integrity.

R&A
APRIL 6, 2024
The third 'fragmentation wave' of the IT-revolution is upon us, it seems. Fragmentation/encapsulation is a repeated pattern in the IT-revolution for managing complexity. First as object oriented programming (for code) and later as agile (for IT landscape change). Now, it is the organisations turn to fragment. How strong is your mission, your why? You might soon find out, thanks to IT.

Engineering at Meta
APRIL 11, 2024
A Meta systems engineer shares how building and scaling our next generation MTIA chip will enable the future of AI.

Packet Pushers
APRIL 9, 2024
In todays episode Greg and Johna spar over how, when, and why to regulate AI. Does early regulation lead to bad regulation? Does late regulation lead to a situation beyond democratic control? Comparing nascent regulation efforts in the EU, UK, and US, they analyze socio-legal principles like privacy and distributed liability. Most importantly, Johna drives.

Engineering at Meta
APRIL 11, 2024
An engineer shares how his team is building the foundation for AI infrastructure at Meta, from physical data centers to training AI models.
Let's personalize your content