Training LLMs at Scale with AMD MI250 GPUs
databricks
OCTOBER 30, 2023
Introduction Four months ago, we shared how AMD had emerged as a capable platform for generative AI and demonstrated how to easily and.

databricks
OCTOBER 30, 2023
Introduction Four months ago, we shared how AMD had emerged as a capable platform for generative AI and demonstrated how to easily and.
InfoQ Articles
NOVEMBER 2, 2023
Taking sides in the debate of microservices v. monolith gets in the way of doing the right thing for our customers. Sometimes, we need microservices. Sometimes, we need a monolith. Most of the time we are better off somewhere between these extremes.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Confluent
NOVEMBER 3, 2023
Learn how AI-powered customer intelligence platform Dialpad modernized its data infrastructure and improved customer satisfaction rates with Confluent and Startree.

Dataversity
OCTOBER 30, 2023
In today’s rapidly evolving business landscape, decision-making has shifted from relying on gut instinct and the loudest voice in the room to data-driven approaches. In this article, we will explore five powerful ways to harness data for making informed decisions in the workplace, offer practical insights to boost productivity, and explain how to adapt to […] The post 5 Ways to Use Data to Make Workplace Decisions appeared first on DATAVERSITY.

databricks
OCTOBER 31, 2023
Today we're excited to announce MLflow 2.8 supports our LLM-as-a-judge metrics which can help save time and costs while providing an approximation of.

Engineering at Meta
OCTOBER 31, 2023
Meta’s Systematic Code and Asset Removal Framework (SCARF) has a subsystem for identifying and removing unused data types. SCARF scans production data systems to identify tables or assets that are unused and safely removes them. SCARF avoids tedious manual work and ensures that product data is correctly removed when a product is shut down. This is the third and final post in our series on Meta’s Systematic Code and Asset Removal Framework (SCARF).

DoorDash Engineering
OCTOBER 31, 2023
At DoorDash, the growth and development of our engineering talent is critical to our success and ability to continue innovating. Apprenticeship has had a long history of successfully cultivating new generations of talent across many different industries. Tech is no different. Designed to identify and foster exceptional engineering talent within the company, DoorDash’s Apprentice Engineering Manager Program prepares engineers to transition into a people management role effectively and autonomousl
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

databricks
NOVEMBER 1, 2023
Whether you’re an NFL fanatic, an alumnus rooting for your alma mater or a super fan just trying to catch a glimpse of T.

Mixpanel
NOVEMBER 2, 2023
What if I told you that most seed-stage startups—even those at the forefront of AI—are way behind on analytics? The reason is obvious: When you’re a small team, like we are at Consensus , you have a million things to prioritize, so it’s hard to find the time to invest in work that your users aren’t asking for. But there’s one big problem with this logic: User interviews, support tickets, and feature requests can only get you so far.

Confluent
OCTOBER 31, 2023
Empower your data analysts with real-time AI and data streaming so they can make better decisions, faster.

Dataversity
NOVEMBER 3, 2023
For the past year, we’ve heard about applications of generative artificial intelligence (AI) on the open web, achieving everything from writing articles and improving search to creating artwork and altering speech – some more successfully than others. But as the technology matures, we’re finally starting to see valuable enterprise use cases for generative and conversational […] The post Knowledge Management and AI: Putting Your Internal Data to Work appeared first on DATAVERSITY.

databricks
OCTOBER 30, 2023
Last year, we published the Big Book of MLOps, outlining guiding principles, design considerations, and reference architectures for Machine Learning Operations (MLOps). Since.
TDAN
OCTOBER 31, 2023
The concept of “walking the data factory” drew a great deal of interest during our recent DGPO webinar on data classification as part of a holistic governance program. We discussed ways to connect the stove-piped worlds of data governance and information governance under a common governance classification.

Confluent
NOVEMBER 1, 2023
Confluent’s data streaming expands through native integrations with technology partners and vector database providers.

Dataversity
OCTOBER 30, 2023
As Cybersecurity Awareness Month winds down, I am stunned at the feedback I have been receiving on my daily social media posts about cybersecurity and cyber storage resilience and recovery. An awakening is happening that serious changes are underway in the cyber threat landscape − just as there is a realization that too many enterprises have not […] The post New Cyberattack Trends Emerging: Are Enterprises Ready?

databricks
NOVEMBER 2, 2023
In this blog we will demonstrate with examples, how you can seamlessly upgrade your Hive metastore (HMS)* tables to Unity Catalog (UC) using.

Packet Pushers
NOVEMBER 3, 2023
The Future of Networking series continues with Brad Casemore, who survived multiple decades in the technology sector, including sixteen years as an analyst for IDC. He’s been a longtime observer of networking markets, technologies, and trends. Recently retired from the analyst business, we’ve invited Brad onto the show as a kind of exit interview to.

Confluent
NOVEMBER 3, 2023
With 5 million Kafka engineering hours invested and a 99.99% SLA, Confluent’s data streaming platform is helping new and existing financial services firms bring great experiences to customers.

Dataversity
NOVEMBER 2, 2023
The desire to leverage data as a strategic asset has led to the development of sophisticated systems and methodologies that go beyond basic data storage and retrieval. Among these advancements is modern data warehousing, a comprehensive approach that provides access to vast and disparate datasets. The concept of data warehousing emerged as organizations began to […] The post The Data Warehouse Development Lifecycle Explained appeared first on DATAVERSITY.

databricks
NOVEMBER 3, 2023
In this four-part blog series "Lessons learned from building Cybersecurity Lakehouses," we will discuss a number of challenges organizations face with data engineering.

Obkio
NOVEMBER 3, 2023
Learn how to identify network issues. Diagnose network issues & detect network problems by looking at common problems, causes, consequences & solutions.

Packet Pushers
NOVEMBER 2, 2023
DHCPv6 Prefix Delegation (DHCPv6-PD) is an IETF RFC that lets one router delegate a long-lived prefix, using DHCP, to a requesting router. What’s the need for this? As the RFC notes, some applications expect stable addresses. It also notes: It is appropriate for situations in which the delegating router does not have knowledge about the. Read more » DHCPv6 Prefix Delegation (DHCPv6-PD) is an IETF RFC that lets one router delegate a long-lived prefix, using DHCP, to a requesting router

Dataversity
NOVEMBER 1, 2023
In a time when technological advancements are accelerating, the fusion of blockchain and supply chain management has become an increasingly important topic. This article will examine the different dimensions of this fusion, focusing on its present applications and future possibilities. How Blockchain Revolutionizes Supply Chain Management Blockchain isn’t just a trendy term – it’s a […] The post The Intersection of Blockchain and Supply Chain Management appeared first on DATAVERSITY.

databricks
NOVEMBER 1, 2023
We are excited to announce the general availability (GA) of several key security features for Databricks on Google Cloud: Private connectivity with Private.
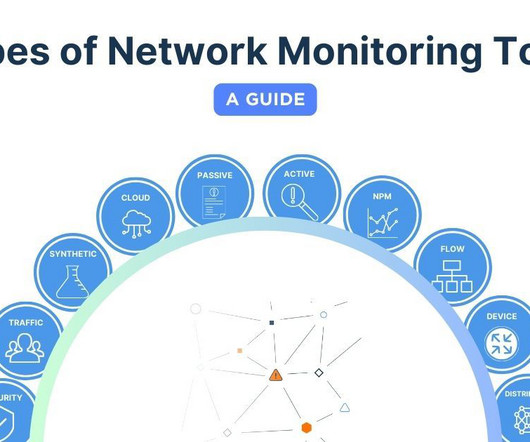
Obkio
NOVEMBER 2, 2023
Discover the superheroes of network monitoring tools in our comprehensive guide. Unveil the perfect type of network monitoring tool for your business.

CATO Networks
NOVEMBER 2, 2023
By Vadim Freger , Dolev Moshe Attiya , Shirley Baumgarten All secured webservers are alike; each vulnerable webserver running on a network appliance is vulnerable in its own way. On October 16th 2023 Cisco published a security advisory detailing an actively exploited vulnerability ( CVE-2023-20198 ) in its IOS XE operating system with a 10 CVSS score, allowing for unauthenticated privilege escalation and subsequent full administrative access (level 15 in Cisco terminology) to the vulnerable devi

Dataversity
OCTOBER 31, 2023
Within the digital marketplace, it is impossible for businesses and organizations to thrive without staying current with the latest technologies. As digitization grows, so does the tech-centric reliance from global enterprises in automating and adapting their workflows to expand their businesses more efficiently. One of the fastest-growing solutions for ensuring enterprise-wide efficiency across multiple systems […] The post Navigating Growth Challenges with Microservices appeared first on

Packet Pushers
NOVEMBER 1, 2023
AI and machine learning are being more widely used in IT and elsewhere. Today's episode opens the AI magic box to better understand what's inside, including software and hardware. We discuss essentials such as training models and parameters, software components, GPUs, networking, and storage. We also discuss using cloud-based AI platforms vs. building your own in-house, and what to consider when assembling your own AI infrastructure.

Obkio
NOVEMBER 1, 2023
Keep your business's network performance shining bright with Meraki Network Monitoring. Don't get left in the dark - learn more today!
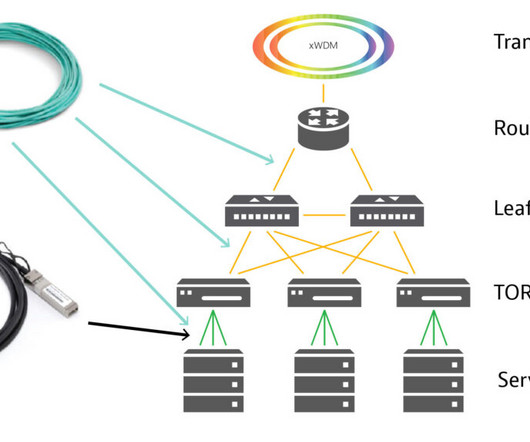
VIAVI Solutions
OCTOBER 31, 2023
In todays data-driven world, high-speed data transfers and reliable connectivity are critical to the success of every data center. As data rates continue to rise, it is vital to ensure the integrity of data transmission across networks. Essential components in that data transfer within a rack, from rack-to-rack, or from network-to-network are AOC/DAC/AEC cables (Active […] The post Getting The Most Out of 400G AOC/DAC Cables appeared first on VIAVI Perspectives.

TDAN
OCTOBER 31, 2023
Today’s data-driven economy relies heavily on AI and ML systems that can sift through mountains of information to find actionable insights and power crucial strategic choices. Standardized, freely available data is essential for the widespread use of AI and ML technologies. Data virtualization is appealing because it eliminates the need to store data physically.

Packet Pushers
OCTOBER 31, 2023
Two Wi-Fi engineers share their experiences automating wireless workflows, including the role of Python & tools like Postman. Two Wi-Fi engineers share their experiences automating wireless workflows, including the role of Python & tools like Postman.
Obkio
OCTOBER 30, 2023
Unveil the secrets to detecting & reducing network overload. Learn to prevent it & control your network capacity with the power of Obkio's monitoring tool.

CATO Networks
OCTOBER 30, 2023
Modern enterprise complexity is challenging cybersecurity programs. With the widespread adoption of cloud services and remote work, and the broadening distribution of applications and employees away from traditional corporate locations, organizations require a more flexible and scalable approach to network security. SASE technology can help address these issues, making SASE adoption a goal for many organizations worldwide.

TDAN
OCTOBER 31, 2023
In my tenure as a project manager in the ever-changing landscape of digital marketing, one element has persistently resonated as a cornerstone of success: data. However, it’s not merely the presence of data that matters, but its sanctity and reliability. Herein emerges the unsung heroes of our data-driven narratives: data stewards.

Packet Pushers
OCTOBER 30, 2023
Today's episode includes Cisco patching a critical vulnerability affecting IOS-XE gear, startup Prosimo releasing a cost calculator to help network engineers track their public cloud networking costs, and Juniper integrating its SD-WAN to the AWS cloud WAN. We also cover Cisco's investment in a quantum networking startup, growing DPU sales, and Intel divesting from pluggable optical modules.

Architect Elevator
OCTOBER 30, 2023
What better day to launch The Grim Wrapper than Halloween?
Let's personalize your content