Migrating to the Cloud: SMB Edition
Cisco Wireless
FEBRUARY 18, 2025
The sheer amount of digital assets it takes to run a company today is dizzying. Accounting for every application, word doc, presentation, or piece of internal data, even small and medium-sized businesses can rack up assets in the tens of thousands.


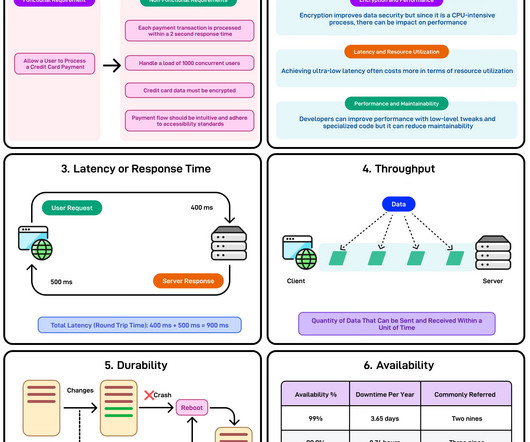




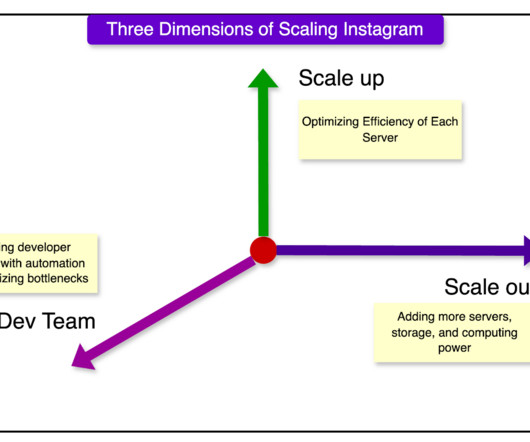

























Let's personalize your content