A New Standard in Open Source AI: Meta Llama 3.1 on Databricks
databricks
JULY 23, 2024
We are excited to partner with Meta to release the Llama 3.1 series of models on Databricks, further advancing the standard of powerful.

databricks
JULY 23, 2024
We are excited to partner with Meta to release the Llama 3.1 series of models on Databricks, further advancing the standard of powerful.

Dataversity
JULY 22, 2024
Discerning businesses are ensuring each area of their organizations has access to performance metrics. Armed with data, their teams can accelerate decision-making, respond to client and marketplace demands, and mitigate risks. The issue is many organizations have segregated data environments. Each department often has its own data management platform that may not integrate with other […] The post Data Concierge: Driving Business Intelligence Collaboration appeared first on DATAVERSITY.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Packet Pushers
JULY 26, 2024
On todays show we talk about designing a network to support hybrid cloud deployments. That is, building and operating a network to interconnect the Big Three US public clouds (GCP, AWS, and Azure) as well as on-prem infrastructure to support a variety of applications and workloads. The network design had to meet several requirements, including. Read more » On todays show we talk about designing a network to support hybrid cloud deployments.

Obkio
JULY 22, 2024
Unravel the mystery of packet reordering! Learn its impact on network performance & discover tools like Obkio for detection and optimization.

databricks
JULY 23, 2024
In this blog, we are excited to share Databricks's journey in migrating to Unity Catalog for enhanced data governance. We'll discuss our high-level strategy and the tools we developed to facilitate the migration. Our goal is to highlight the benefits of Unity Catalog and make you feel confident about transitioning to it.

Dataversity
JULY 26, 2024
When it comes to solving business problems, data scientists understand how crucial it is to formulate the right business question. While it’s easy to get sidetracked by intriguing data trails, the most effective questions are those that align closely with organizational priorities, provide actionable insights, and guide strategic decisions. Here are the key principles for crafting high-impact […] The post How to Ask Great Questions with a Data Science Lens appeared first on DATAVERSITY.

Rule 11
JULY 26, 2024
Eyvonne and Russ catch up with Greg Ferro one last time to talk about the permissionless Internet–a thing of the past–vendor lock in, and many other random topics on this episode of the Hedge. Greg–here’s to a grand time in the future. We’ll miss you. [link] download Eyvonne and Russ catch up with Greg Ferro one last time to talk about the permissionless Internet--a thing of the past--vendor lock in, and many other random topics on this episode of the Hedge.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.
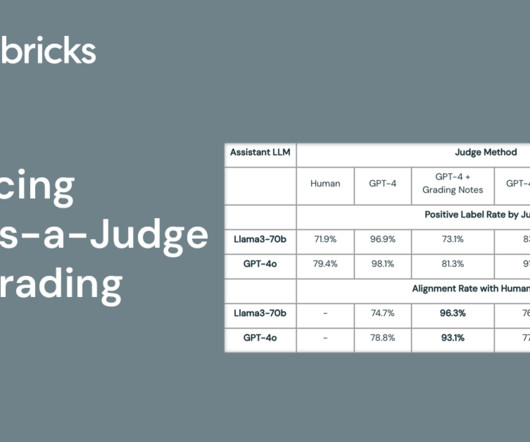
databricks
JULY 22, 2024
Evaluating long-form LLM outputs quickly and accurately is critical for rapid AI development. As a result, many developers wish to deploy LLM-as-judge methods.

R&A
JULY 20, 2024
What happens when your organisation suddenly loses all of its IT? There are enough realistic ways for that to happen. Think: a really successful ransomware attack. As it turns out, first turning ourselves into 'digital organisations', and then requiring a speedy recovery from 'digital armageddon' creates a weapons grade challenge.

Cloudera Blog
JULY 22, 2024
Late last week, the tech world witnessed a significant disruption caused by a faulty update from CrowdStrike, a cybersecurity software company that focuses on protecting endpoints, cloud workloads, identity, and data. This update led to global IT outages, severely affecting various sectors such as banking, airlines, and healthcare. Many organizations found their systems rendered inoperative, highlighting the critical importance of system resilience and reliability.

Confluent
JULY 23, 2024
CC 2024 Q2 adds Flink Private Networking (AWS), Flink SQL Interactive Tables; Enterprise:Connect w/Confluent, Connector Custom Offsets; SI: Build w/Confluent, etc.
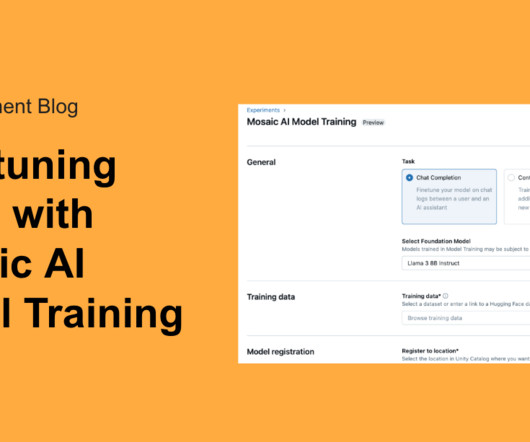
databricks
JULY 22, 2024
Today, we're thrilled to announce that Mosaic AI Model Training's support for fine-tuning GenAI models is now available in Public Preview. At Databricks.

Dataversity
JULY 23, 2024
Generative AI has huge potential, but it also faces problems. If generative AI creates information that is not factually accurate in response to a user request – resulting in so-called hallucinations – it can have a big impact on users. Relying on large language model (LLM) training data on its own is not enough to prevent […] The post Generative AI and Data: Using Knowledge Graphs and RAG Together appeared first on DATAVERSITY.

Cloudera Blog
JULY 24, 2024
Cloudera recently unveiled the latest version of Cloudera Private Cloud Base with the Zero Downtime Upgrade (ZDU) feature to enhance your user experience. The goal of ZDU is to make upgrades simpler for you and your stakeholders by increasing the availability of Cloudera’s services. How Do You Keep IT Infrastructure (and Buses) Running and Avoid Downtime?

Networking Nerd
JULY 26, 2024
Recently at Networking Field Day , one of the presenters for cPacket had a wonderful line that stuck with me: There’s no compression algorithm for experience. Like, floored. Because it hits at the heart of a couple of different things that are going on in the IT industry right now that showcase why it feels like everything is on the verge of falling apart and what we can do to help that.
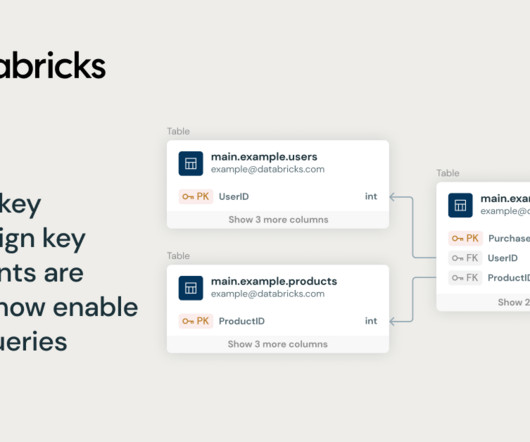
databricks
JULY 24, 2024
Dataricks is thrilled to announce the General Availability (GA) of Primary Key (PK) and Foreign Key (FK) constraints, starting in Databricks Runtime 15.2.

Dataversity
JULY 22, 2024
The increase in the prevalence and complexity of data breaches points to one conclusion – traditional cybersecurity measures are no longer enough to keep our valuable data safe. According to a recent report, data breaches exposed a staggering 35 billion records in the first four months of 2024. To deal with this escalating crisis, a new solution […] The post The Rise of Cybersecurity Data Lakes: Shielding the Future of Data appeared first on DATAVERSITY.
CATO Networks
JULY 24, 2024
Healthcare and pharma companies are at the forefront of our most important need as humans: saving lives. To succeed, they require highly skilled staff members, medical equipment, drugs and resources. On top of these, there is another equally crucial component that will determine their ability to perform their jobs: their network. A secure, reliable and high performing network will ensure patient safety, data integrity and operational efficiency.
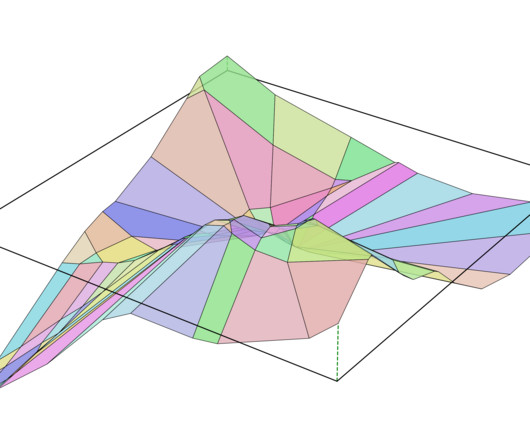
Jane Street
JULY 21, 2024
Neural networks are often thought of as opaque, black-box function approximators, but theoretical tools let us describe and visualize their behavior. In particular, lets study piecewise-linearity, a property many neural networks share. This property has been studied before , but well try to visualize it in more detail than has been previously done.
databricks
JULY 26, 2024
Introduction Time series forecasting serves as the foundation for inventory and demand management in most enterprises. Using data from past periods along with.

Dataversity
JULY 25, 2024
Over the past few years, the industry has increasingly recognized the need to adopt a data lakehouse architecture because of the inherent benefits. This approach improves data infrastructure costs and reduces time-to-insight by consolidating more data workloads into a single source of truth on the organization’s data lake. This is made possible by data lakehouse table […] The post Taking the Chill Out of Selecting the Appropriate Iceberg Data Catalog appeared first on DATAVERSITY.

Packet Pushers
JULY 25, 2024
This first episode of Technically Leadership explores distinctions and commonalities between the management track and the staff engineer track with guests Nick Silkey and Martin Smith. Our guests share their stories from both perspectives and offer advice for those considering similar paths in technical leadership. Episode Guests: Nick Silkey and Martin Smith Nick Silkey, Senior.
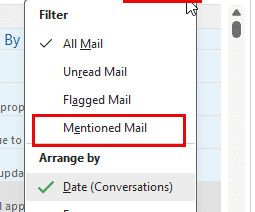
Slipstick
JULY 25, 2024
A user wanted to know how to create a rule to add a category to messages he was @mentioned on. I'll show you how to use a run a script rule or an ItemAdd macro to set a category on a message you were @mentioned on in classic Outlook. The post Categorize @Mentioned Messages appeared first on Slipstick Systems.

databricks
JULY 23, 2024
The communications industry is experiencing immense change due to rapid technological advancements and evolving market trends. Communications service providers (CSP) build various solutions.

Dataversity
JULY 26, 2024
Today’s modern business landscape is fiercely competitive, and companies are wielding cloud computing as a strategic weapon to gain an edge. Cloud computing has revolutionized how businesses operate, offering on-demand access to a vast pool of IT resources – storage, servers, databases, networking, and software – all securely delivered over the internet.

Packet Pushers
JULY 25, 2024
RFC 9099 addresses security considerations for operating IPv6 networks, including issues such as address allocation and architecture, security considerations for DHCPv6 and DNS64, and more. Two of the RFC’s co-authors, Merike Kaeo and Eric Vyncke, join the IPv6 Buzz team to talk about the motivations for and challenges of creating RFC 9099. Episode Guests: Merike.
How Funky
JULY 24, 2024
If you are actively looking to build out AI network infrastructure and want to utilize white box, cost effective switching, one of the challenges you have is what software you will use to design, deploy, operate and manage those network switches, because doing that by hand via a CLI will not be fun. Hedgehog wants to be the software you use to solve this problem, along with a few more use cases.

databricks
JULY 22, 2024
Written in collaboration with Navin Sharma and Joe Pindell, Stardog Across industries, the impact of post-delivery failure costs (recalls, warranty claims, lost goodwill.

CATO Networks
JULY 24, 2024
Build Partner Trust. Avoid Partner Fatigue Trust takes years to build, seconds to break, and forever to repair. The road to becoming a trusted partner to your customers has no shortcuts. As you review your portfolio, filled with various network and IT security solutions youve accumulated over the years, you believe each fulfills the needs of your customers.

Packet Pushers
JULY 24, 2024
Guests Ashish and Shilpi from the Cloud Security Podcast converse with Ned and Kyler on how humor and relatability can foster an engaging and collaborative environment in DevOps. The conversation also covers the importance of foundational knowledge in technology, the impact of AI on careers, and the value of just being human and learning from. Read more » Guests Ashish and Shilpi from the Cloud Security Podcast converse with Ned and Kyler on how humor and relatability can foster an engaging

Dataversity
JULY 24, 2024
As AI matures and becomes more integrated into clinical trial operations, generative AI (GenAI) technology is ushering in a new era for clinical research and drug development, redefining the clinical trial landscape and offering a quantum leap in efficiency and precision. This innovative technology streamlines every phase, transforming traditionally time-consuming processes into swift, automated workflows. […] The post From Complexity to Clarity: GenAI Decodes Clinical Trial Data appeared

VIAVI Solutions
JULY 22, 2024
Observability is defined in mathematical terms as the ability to measure the internal state of a system based on only external information. On the other hand, monitoring is defined as a passive data collection process used to measure performance against predefined standards. In other words, network observability practices tend to be proactive, while monitoring tends […] The post Getting to the Heart of Observability appeared first on VIAVI Perspectives.

CATO Networks
JULY 22, 2024
The Paris Olympics are coming up, arousing excitement and anticipation around the globe. As the worlds greatest athletes prepare to compete on this renowned stage, lets shift our focus to a few of the earliest Olympics competitors – the Greek Gods. These deities, myth says, competed in the ancient Olympics, and later on, the Games were held in their honor.

Packet Pushers
JULY 23, 2024
Should enterprises ditch Microsoft because of security concerns? Microsoft’s numerous vulnerabilities and questionable responses make it a significant risk for continued use. At the same time, Microsoft’s strong integration and utility in enterprise environments make it attractive for continued use. Johna Till Johnson and John Burke debate.

Scott's Weblog
JULY 26, 2024
Welcome to Technology Short Take #180! It’s hard to believe that July is almost over, and that 2024 is flying past us. It’s probably time that you, my readers, took some time to slow down and read more technical blogs. To help with that, I just happen to have a little collection of links to share. Enjoy! Networking Read this article to better understand why native VLANs exist.

Rule 11
JULY 20, 2024
On the other hand, these same minimal overheads imply that DNS over UDP cannot perform prompt detection of packet loss and cannot efficiently defend itself against various approaches to tampering with the DNS, such as source address spoofing, payload alteration and third-party packet injection. Perhaps most importantly, the way UDP handles large payloads is a problem.

Packet Pushers
JULY 23, 2024
From an SSID confusion exploit to a RADIUS attack to a critical vulnerability in a Windows Wi-Fi driver, the past several months have seen multiple attacks and exploits targeting the wireless realm. On todays Packet Protector podcast we talk with Wi-Fi security expert Stephen Orr to get his take on the severity of these issues, Read more » From an SSID confusion exploit to a RADIUS attack to a critical vulnerability in a Windows Wi-Fi driver, the past several months have seen multiple attac
Let's personalize your content