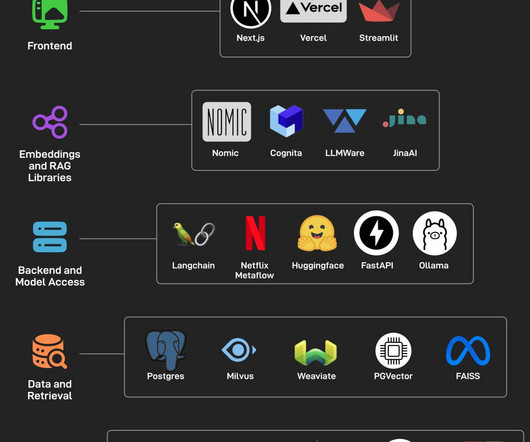
EP146: The Open Source AI Stack
ByteByteGo
JANUARY 18, 2025
This week’s system design refresher: API Vs SDK! What's the difference? (Youtube video) The Open Source AI Stack Cookies Vs Sessions Vs JWT Vs PASETO Algorithms you should know before taking System Design Interviews Top 6 Load Balancing Algorithms How TikTok Manages a 200K File Frontend MonoRepo? SPONSOR US API Vs SDK! What's the difference? The Open Source AI Stack You don’t need to spend a fortune to build an AI application.



































Let's personalize your content