Optimizing Databricks LLM Pipelines with DSPy
databricks
MAY 22, 2024
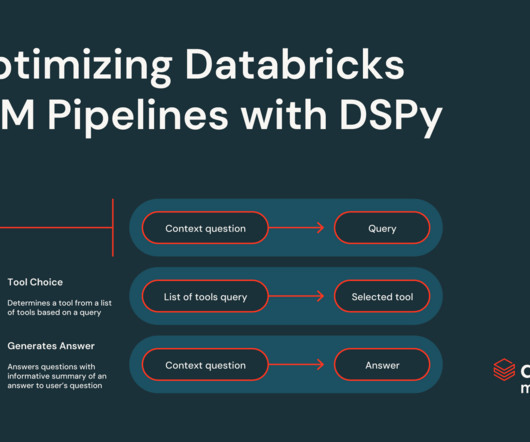
If you’ve been following the world of industry-grade LLM technology for the last year, you’ve likely observed a plethora of frameworks and tools.
databricks
MAY 22, 2024
If you’ve been following the world of industry-grade LLM technology for the last year, you’ve likely observed a plethora of frameworks and tools.

Engineering at Meta
MAY 22, 2024
Today, the internet (like most digital infrastructure in general) relies heavily on the security offered by public-key cryptosystems such as RSA, Diffie-Hellman (DH), and elliptic curve cryptography (ECC). But the advent of quantum computers has raised real questions about the long-term privacy of data exchanged over the internet. In the future, significant advances in quantum computing will make it possible for adversaries to decrypt stored data that was encrypted using today’s cryptosystems.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

InfoQ Articles
MAY 21, 2024
This article describes an experiment that sought to determine if no-cost LLM-based code generation tools can improve developer productivity. The experiment evaluated several LLMs by generating unit tests for some open-source code and measuring the code coverage as well as the manual rework necessary to make the tests work.

Confluent
MAY 21, 2024
Confluent’s OpenSearch Sink Connector lets you easily send events to AWS OpenSearch and others—enabling fraud detection, log analytics, social media monitoring & GenAI w/RAG.

databricks
MAY 22, 2024
We’re excited to announce the General Availability of Delta Lake Liquid Clustering in the Databricks Data Intelligence Platform. Liquid Clustering is an innovative.

Engineering at Meta
MAY 22, 2024
In recent years, Meta’s data management systems have evolved into a composable architecture that creates interoperability, promotes reusability, and improves engineering efficiency. We’re sharing how we’ve achieved this, in part, by leveraging Velox , Meta’s open source execution engine, as well as work ahead as we continue to rethink our data management systems.

InfoQ Articles
MAY 20, 2024
Platform engineering is not just a technical problem to solve nor an end in itself. In this article, I will share key lessons I have learned while building and delivering three platforms over the last two decades from VMware and Stripe to Apollo GraphQL, including where we got stuck, how we unblocked ourselves, and what ultimately led to the right outcomes for our users and the business.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.
databricks
MAY 19, 2024
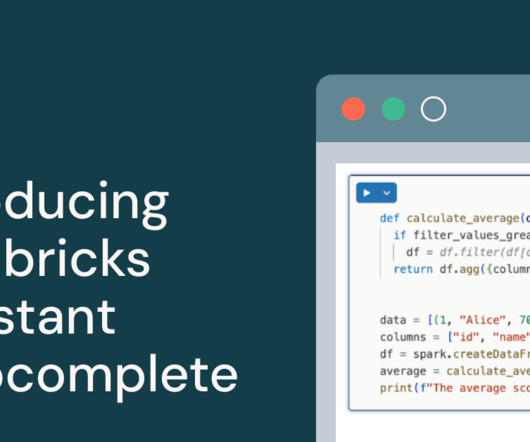
We are excited to introduce Databricks Assistant Autocomplete now in Public Preview. This feature brings the AI-powered assistant to you in real-time, providing.

Dataversity
MAY 24, 2024
With the rapid development of artificial intelligence (AI) and large language models (LLMs), companies are rushing to incorporate automated technology into their networks and applications. However, as the age of automation persists, organizations must reassess the data on which their automated platforms are being trained. To maximize the potential of AI using sensitive data, we […] The post Maximizing AI’s Potential: High-Value Data Produces High-Quality Results appeared first on DATAVERSI

InfoQ Articles
MAY 22, 2024
Carta harnesses the power of a small group of senior engineers called navigators to bridge the gap between global strategy and local decision-making, using a written engineering strategy. Navigators replace a need for consensus and boost velocity by combining technical context, domain context, strategic alignment, and judgment to make engineering decisions quickly.

Confluent
MAY 22, 2024
Scaling Kafka clusters up and down to meet changing demands is challenging. In this blog, learn how elastic autoscaling Enterprise clusters save you time and money.
databricks
MAY 21, 2024
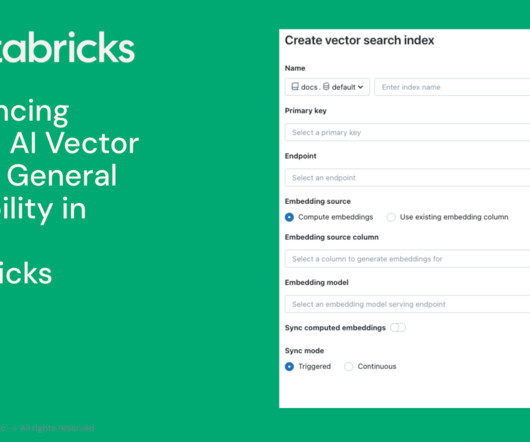
Following the announcement we made around a suite of tools for Retrieval Augmented Generation, today we are thrilled to announce the general availability.

Dataversity
MAY 23, 2024
As a cognitive scientist, I’ve been immersed in AI for more than 30 years – specifically in speech and natural language understanding, as well as machine-based learning and rule-based decision-making. Progress in our field is always uneven, unfolding in fits and starts. Those of us in the AI field have witnessed multiple “AI winters” over the […] The post How a Neuro-Symbolic AI Approach Can Improve Trust in AI Apps appeared first on DATAVERSITY.

Packet Pushers
MAY 24, 2024
The variety and number of OT devices continue to grow at such a pace that network engineers really need to think through how to manage them as part of their broader network. Dan Massameno joins the show to talk about how hes collaborating with his facilities department and using SD-Access to manage the OT virtual. Read more » The variety and number of OT devices continue to grow at such a pace that network engineers really need to think through how to manage them as part of their broader ne

Confluent
MAY 23, 2024
Discover how Confluent leads data dissemination in DISA's Thunderdome, revolutionizing DoD's security architecture with zero trust principles.

databricks
MAY 21, 2024
We’re excited to announce the Databricks AI Fund, showcasing our commitment to supporting a new generation of founders and startups.

Dataversity
MAY 22, 2024
One of the most pervasive cybersecurity challenges is “access creep” – the gradual, often unnoticed accumulation of access privileges by employees beyond what their current role requires. This phenomenon occurs when initial access rights granted for specific roles are not revoked as employees change positions or their job duties evolve. Over time, this unchecked accrual […] The post Taming Access Creep: Strategies to Rein in Unnecessary Privileges appeared first on DATAVERSITY.
The Network DNA
MAY 24, 2024
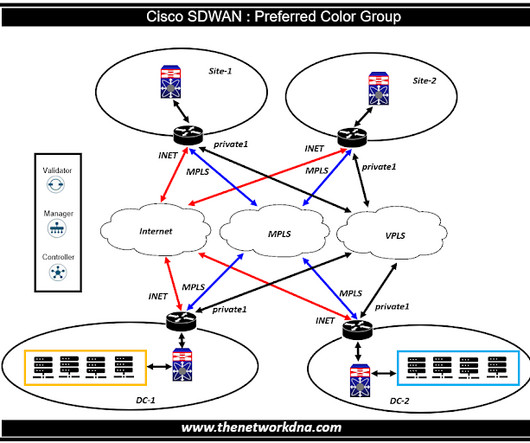
Cisco SDWAN : Preferred color group We are going to talk about the feature in cisco sdwan called as "Preferred color group". The term color in Cisco SD-WAN refers to a classification of transport circuits or paths that traffic can take, which helps in differentiating the types of connectivity (like MPLS, internet, 3G/4G, etc.). This feature adds support for ranking of Application Aware Routing (AAR) or Data Policy preferred over a primary color and followed by backup preferred colors.
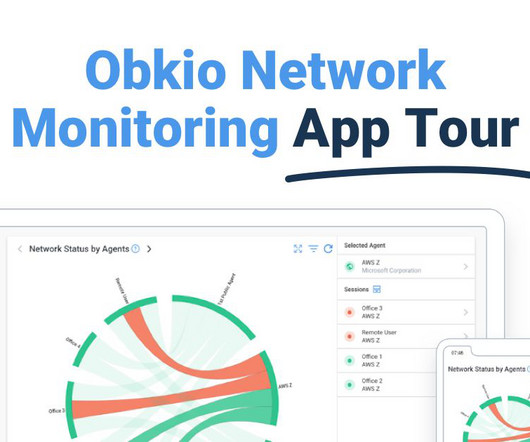
Obkio
MAY 24, 2024
Be guided through how to identify and troubleshoot network problems with Obkios Network Monitoring app tour and features through screenshots.

databricks
MAY 23, 2024
The Data Team Awards annually recognize the indispensable roles of enterprise data teams across industries, celebrating their resilience and innovation from around the.

Dataversity
MAY 21, 2024
Technology audit processes have become increasingly important, as they tie directly to adherence to an ever-growing list of compliance frameworks and mandates such as NIST, CIS, SOC 2 ISO 27001, and others. A component of all these regulations pertains to the integrity of enterprise technology management and requires an up-to-date and accurate inventory of all […] The post Technology Audit Processes Are Broken, but Attention and Automation Can Fix Them appeared first on DATAVERSITY.

The Network DNA
MAY 23, 2024
Impact of Unauthenticated API Vulnerabilities: Cisco CUCM Vulnerability : CVE-2023-20259 An unauthenticated, remote attacker may be able to induce significant CPU use through a vulnerability in an API endpoint of several Cisco Unified Communications Products. This could affect the ability to access the web-based management interface and result in delays when processing calls.

VIAVI Solutions
MAY 23, 2024
VIAVI has spent decades testing Ethernet as a service, fueling its leadership position in testing modules, cables, and Ethernet ICs at the PHY layer. We also have products that cover the full stack to L7, offering breadth and depth of coverage. A few years ago, we determined current products on the market for high-scale Ethernet […] The post Lab and live Ethernet testing at scale – 800G and beyond appeared first on VIAVI Perspectives.

databricks
MAY 22, 2024
Generative AI (GenAI) is moving incredibly fast. So much so, that in less than two years, GenAI has emerged as one of the.

Dataversity
MAY 20, 2024
As your data projects evolve, you will face new challenges. For new technology like generative AI, some challenges may just be variations on traditional IT projects like considering availability or distributed computing deployment problems. However, generative AI projects are also going through what Donald Rumsfeld once called the “unknown unknowns” phase, where we are discovering […] The post Running Generative AI in Production – What Issues Will You Find?

CATO Networks
MAY 23, 2024
On May 6 th , 2024, researchers from the Leviathan Security Group published an article detailing a technique to bypass most VPN applications, assigned as CVE-2024-3661 with a High CVSS score of 7.6. Researchers have labeled this technique ‘decloaking’ as while the VPN tunnel remains connected, it allows attackers to trick many VPN clients into sending traffic via a side channel and not through the encrypted tunnel.
Mixpanel
MAY 23, 2024
When you’re releasing a new product or feature, the step that gets the most attention is usually the beta testing phase. But getting a feature to a market-ready state is a long process involving months of work before you get to beta testing. Sometimes, features don’t even make it to the beta stage—and that’s often not a bad thing when you consider the alternative is overspending time and resources to force a feature that isn’t worth it.

databricks
MAY 24, 2024
In today's digital landscape, secure data sharing is critical to operational efficiency and innovation. Databricks and the Linux Foundation developed Delta Sharing as.

Dataversity
MAY 20, 2024
Today, more than ever, people are concerned about data privacy. Reflecting this, countries all over the world have introduced privacy laws – GDPR and CCPA being the biggest examples. These laws govern how businesses should collect, manage, and maintain data. This has prompted businesses to reevaluate their data collection operations. But to keep data private and secure businesses […] The post Data Privacy Through Robust Data Governance: Strategies and Best Practices appeared first on DATAV

Packet Pushers
MAY 22, 2024
There are about 1.4 million Kubernetes clusters just sitting out there on the public internet as we speak. That is 1.4 million lateral-movement rich, highly privileged environments. The bearer of this anxiety-provoking news is todays guest, Lee Briggs. Lee explains why major cloud providers make this the default option ease of use. The good news. Read more » There are about 1.4 million Kubernetes clusters just sitting out there on the public internet as we speak.

Obkio
MAY 22, 2024
Uncover what causes jitter in your network and how you can troubleshoot. Learn to solve jitter issues & achieve optimal performance.

databricks
MAY 24, 2024
The annual Data Team Awards showcase the remarkable efforts of top global enterprise data teams committed to tackling some of today's toughest business.

Dataversity
MAY 24, 2024
Data extraction is a cornerstone in data analytics, enabling organizations to extract valuable insights from raw data. While basic extraction techniques are fundamental, understanding advanced strategies is crucial for maximizing efficiency and accuracy. This article will explore advanced tips for effective data extraction, shedding light on automation tools, leveraging APIs and web scraping techniques, enhancing […] The post Beyond the Basics: Advanced Tips for Effective Data Extraction a

Packet Pushers
MAY 21, 2024
Dont call it remote work. Today Johna and Greg dive into distributed work the future where there is no office vs. remote, there are just asynchronistic workers and their computer screens. Leaders have to move beyond management by walking around or onboarding by shadowing. They need to carefully select their ecosystem of tools (and tools. Read more » Dont call it remote work.

Networking Nerd
MAY 21, 2024
I once heard a quote that said, “The hardest part of being a butcher is knowing where to cut.” If you’ve ever eaten a cut of meat you know that the difference between a tender steak and a piece of meat that needs hours of tenderizing is just inches apart. Butchers train for years to be able to make the right cuts in the right pieces of meat with speed and precision.
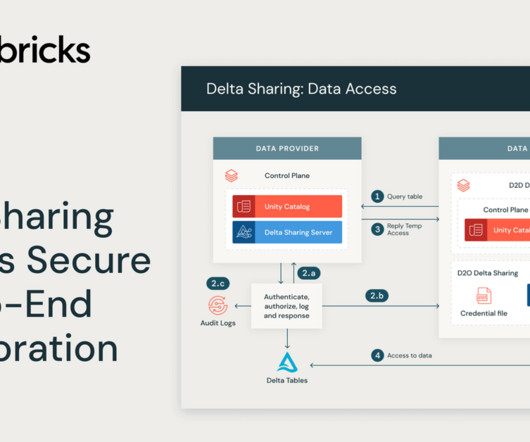
databricks
MAY 24, 2024
In today's digital landscape, secure data sharing is critical to operational efficiency and innovation. Databricks and the Linux Foundation developed Delta Sharing as.

Mixpanel
MAY 21, 2024
Too many companies manage their data in silos. Marketing data stays with the marketing team, product data is confined to product teams, and leadership is focused on revenue and growth metrics. When this happens, no one gets the complete picture, and everyone misses out on valuable insights. Business analytics are tools and processes that allow companies to track and measure events across product data, marketing data, and revenue data, pulling everything into a single place.
Let's personalize your content