Announcing the General Availability of Azure Private Link and Azure Storage firewall support for Databricks SQL Serverless
databricks
FEBRUARY 21, 2024
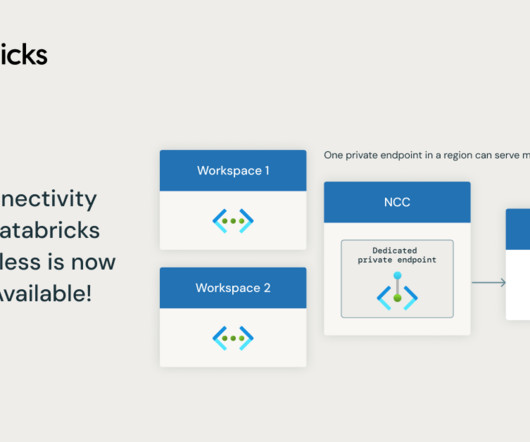
We are excited to announce the upcoming general availability of Azure Private Link support for Databricks SQL (DBSQL) Serverless, planned in April 2024.








































Let's personalize your content