Data Security in the Age of Cloud Computing
TDAN
JULY 3, 2024
Once reliant on the limitations of physical hardware, businesses today have the ability to access and expand a virtual pool of cloud-based network services as needed.

TDAN
JULY 3, 2024
Once reliant on the limitations of physical hardware, businesses today have the ability to access and expand a virtual pool of cloud-based network services as needed.

InfoQ Articles
JULY 3, 2024
Large language models have significantly transformed the field of artificial intelligence. The fundamental innovation behind this change is surprisingly straightforward: make the models a lot bigger. With each new iteration, the capabilities of these models expand, prompting a critical question: Are we moving toward a black box era where AI is controlled by a few tech monopolies?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dataversity
JULY 3, 2024
It is crucial to stress the need to protect data in customer relationship management (CRM) systems because data breaches and cyber threats are becoming more sophisticated. The security measures are inadequate now; companies must constantly seek creative ways to address changing threats. One cannot stress how urgently improved security measures are required.

Packet Pushers
JULY 3, 2024
Service Level Objectives (SLOs) are a set of reliability measurements for customer or user expectations of services; in other words, are people having a good experience with your application or service? Todays Day Two Cloud explores SLOs, the relevant metrics, and how to measure them. We also talk about how SLOs are a cross-discipline objective. Read more » Service Level Objectives (SLOs) are a set of reliability measurements for customer or user expectations of services; in other words, ar
Indeed Engineering
JULY 3, 2024
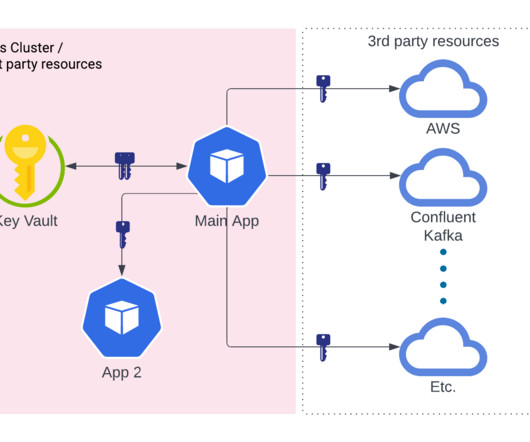
Goal This blog is for engineering teams, architects, and leaders responsible for defining and implementing a workload identity platform and access controls rooted in Zero Trust principles to mitigate the risks from compromised services. It is relevant for companies using Kubernetes to manage workloads, using Istio for service mesh, and aiming to define identities in a way that aligns with internal standards, free from platform-specific constraints.

CATO Networks
JULY 3, 2024
SASE is all about strategically solving business problems. The systematic removal of technology barriers standing in the way of business outcomes. It is a brand new how (platform) for a well-known what (features). When we started Cato Networks in 2015, we were immersed in skepticism. Can you actually build a cloud network that will replace MPLS circuits with decades of proven reliability?
Architect Elevator
JULY 3, 2024
Or: why do IT architects seem have more fun?
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

TDAN
JULY 3, 2024
Technics Publications has started publishing a line of Data-Driven AI books, and one of the first books in this series is “AI Governance” by Dr. Darryl J Carlton.

TDAN
JULY 3, 2024
In my work with the EDM Council’s Data Management Capability Assessment Model (DCAM) 3.0 development group, we are adding a capability that has remained under the radar in our industry, that is, the responsibility of the Data Management Program to determine concept and knowledge gaps within its staff resources.
TDAN
JULY 3, 2024
Terms like artificial intelligence (AI) and augmented intelligence are often used interchangeably. However, they represent fundamentally different approaches to utilizing technology, especially when it comes to data governance. Understanding these differences is crucial for organizations looking to implement non-invasive and effective data governance frameworks.
Let's personalize your content