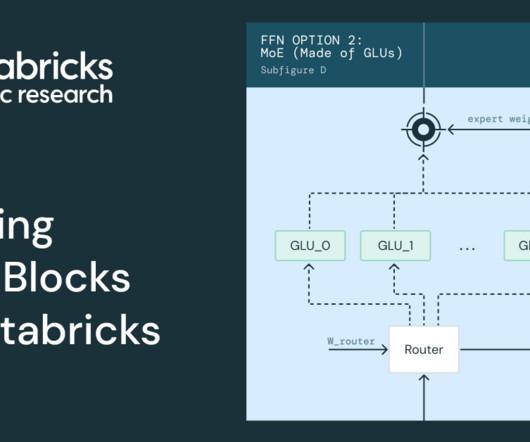
Bringing MegaBlocks to Databricks
databricks
APRIL 9, 2024
At Databricks, we’re committed to building the most efficient and performant training tools for large-scale AI models. With the recent release of DBRX.
databricks
APRIL 9, 2024
At Databricks, we’re committed to building the most efficient and performant training tools for large-scale AI models. With the recent release of DBRX.
InfoQ Articles
APRIL 9, 2024
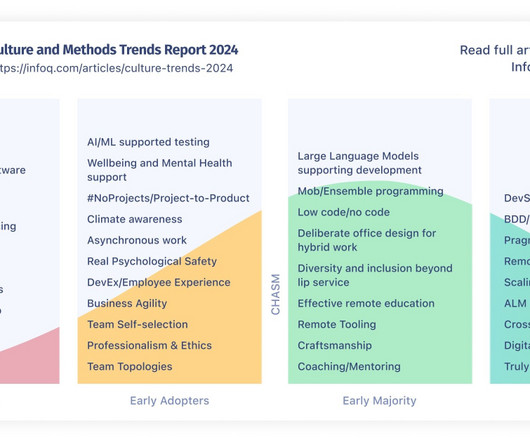
The Culture and Methods trends report discusses evolving roles within teams, the way the staff plus roles are able to add value, the use and misuse of DevEx metrics, how remote work continues to evolve, a lack of diversity is still a challenge, and the need to move from climate change awareness to climate conscious software engineering By Shane Hastie, Jutta Eckstein, Ben Linders, Susan McIntosh, Rafiq Gemmail, Craig Smith
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dataversity
APRIL 9, 2024
Kryder’s Law, named after Mark Kryder – the former SVP of research at Seagate Technology – is an observation comparable to Moore’s Law but specifically related to the area of magnetic disk storage. It posits that the density of information stored on magnetic disks is increasing exponentially, doubling approximately every 18 months. Kryder’s Law, much like Moore’s […] The post Why the Slowdown of Kryder’s Law Spells Urgency for Sustainable Archival Storage appeared first on DATAVERSITY.

Packet Pushers
APRIL 9, 2024
If your approach to firmware is that you dont bother it as long as it doesnt bother you, you might want to listen to this episode. Concerns about supply chain vulnerabilities are on the rise and for good reason: Attackers are targeting firmware because compromising this software can allow attackers to persist on systems after. Read more » If your approach to firmware is that you dont bother it as long as it doesnt bother you, you might want to listen to this episode.

Obkio
APRIL 9, 2024
Learn how to perform a network audit (network performance audit) to uncover issues before they cause havoc. Uncover Obkio's Network Audit Tool.

Noction
APRIL 9, 2024
Understanding BGP states is essential to grasp how BGP operates. Similar to interior gateway protocols (IGPs) like EIGRP, OSPF, or ISIS, BGP establishes peering with other routers before exchanging routing information.

Packet Pushers
APRIL 9, 2024
In todays episode Greg and Johna spar over how, when, and why to regulate AI. Does early regulation lead to bad regulation? Does late regulation lead to a situation beyond democratic control? Comparing nascent regulation efforts in the EU, UK, and US, they analyze socio-legal principles like privacy and distributed liability. Most importantly, Johna drives.
Let's personalize your content