Simplifying Zero Trust Security for the Modern Workplace
Cisco Wireless
JANUARY 22, 2025
Ciscos User Protection Suite now includes Identity Services Engine (ISE), enabling organizations to achieve zero trust for the workplace.

Cisco Wireless
JANUARY 22, 2025
Ciscos User Protection Suite now includes Identity Services Engine (ISE), enabling organizations to achieve zero trust for the workplace.

PubNub
JANUARY 22, 2025
The Real-time Communication API Blog: best practices across in-app chat, push notifications, location tracking and more.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cisco Wireless
JANUARY 22, 2025
Introduction: Overcoming GPU Management Challenges In Part 1 of this blog series, we explored the challenges of hosting large language models (LLMs) on CPU-based workloads within an EKS cluster. We discussed the inefficiencies associated with using CPUs for such tasks, primarily due to the large model sizes and slower inference speeds.

databricks
JANUARY 22, 2025
Databricks has been recognized as one of the winners of the annual Glassdoor Employees Choice Awards, a list of the Best Places to.

Cisco Wireless
JANUARY 22, 2025
Join us at AFCEA West at Booth #1033 to explore Cisco's pioneering technologies and expert insights that are reshaping the future of naval data communications and security.

Network Engineering
JANUARY 22, 2025
What I understand as facts : MAC address are globally unique. It has 48 bits (6 bytes). First 3 bytes are uniquely assigned to manufacturers by IEEE (aka Organizationally Unique Identifier). For example Apple's OUI is bcd074. Last 3 bytes are assigned by manufacturers to every NICs they produce. Each NIC the company produce must have a unique NIC. This makes every single NIC (regardless of manufacturer) in the whole world globally unique.

Cisco Wireless
JANUARY 22, 2025
On March 31, 2025 the new PCI 4.0 requirements go into effect. These requirements were future dated to enable organizations the ability to prepare for the adoption.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.
Network Engineering
JANUARY 22, 2025
Current best networking architecture used by major hyperscaler datacenters? I'm particularly talking about the hyperscalers that are optimized for huge distributed ai training using more than 50,000 gpus or so. Is Spine and leaf architecture the best architecture for datacenter with huge east-west traffic? How do they connect 50K or even 100K+ gpus (recently in XAI's datacenter by elon musk and his team) on a single network?

Cisco Wireless
JANUARY 22, 2025
Introduction: Overcoming GPU Management Challenges In Part 1 of this blog series, we explored the challenges of hosting large language models (LLMs) on CPU-based workloads within an EKS cluster. We discussed the inefficiencies associated with using CPUs for such tasks, primarily due to the large model sizes and slower inference speeds.
Codecentric Blog
JANUARY 22, 2025
Feature-Sliced Design und was wir fr eine gute Frontend-Architektur brauchen Whrend zum Thema Softwarearchitektur im Backend schon viel publiziert wurde und es gut erprobte Best-Practices gibt, is dieses Thema fr Frontend-Anwendungen weniger prsent.
Network Engineering
JANUARY 22, 2025
What is the difference between service password encryption and key config-key password encrypt ? Both of them is password encryption right ?

Juniper
JANUARY 22, 2025
Official Juniper Networks Blogs Juniper Networks Global Higher Education Summit ITAI 2 ITIT IT Wi-Fi Wi-Fi HVACCisco AI 100Reddit Juniper Mist Marvis Marvis Mist Cloud Juniper Networks Global Higher Education SummitIT The post appeared first on Official Juniper Networks Blogs.
4sysops
JANUARY 22, 2025
China ahead in AI – DeepSeek R1 Fully Tested – Insane Performance China appears to be already ahead in AI. 4sysops members can now test this reasoning model in their profiles. I’ve also included Windows Server 2025 AI in the user profile.

Network Engineering
JANUARY 22, 2025
What I understand as facts : MAC address are globally unique. It has 48 bits (6 bytes). First 3 bytes are uniquely assigned to manufacturers by IEEE (aka Organizationally Unique Identifier). For example Apple's OUI is bcd074. Last 3 bytes are assigned by manufacturers to every NICs they produce. Each NIC the company produce must have a unique NIC. This makes every single NIC (regardless of manufacturer) in the whole world globally unique.
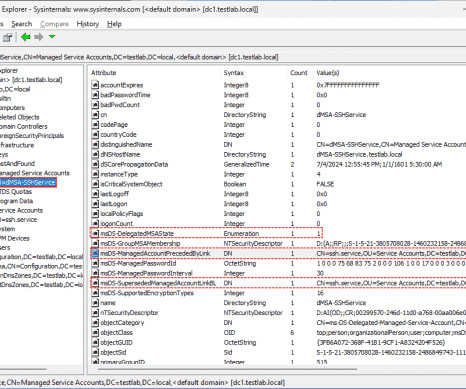
4sysops
JANUARY 22, 2025
In that case, you will not be able to undo or reset the service account migration if/when needed. The original service account is needed to reverse the changes.

EA Voices
JANUARY 22, 2025
From The Digital Transformation Blog Reading Time: 11 min
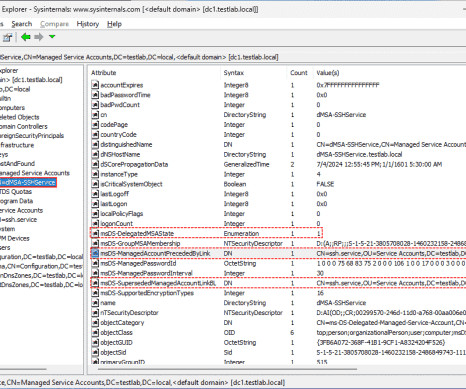
4sysops
JANUARY 22, 2025
No action is needed on your end once you complete the AD service account migration. It automatically unlinks and disables the old service accounts, so you can leave them disabled.

VIAVI Solutions
JANUARY 22, 2025
Like explorers in a dry spell, many organizations recognize that two (or more) clouds can be better than one. Network architecture incorporating multiple public cloud vendors can increase capacity and efficiency while providing the freedom to hand-pick capabilities based on business needs. These benefits have led to a boom in multi-cloud deployments, with 79% of […] The post Weathering The Storms of Multi-Cloud Network Management appeared first on VIAVI Perspectives.

4sysops
JANUARY 22, 2025
Here are more details behind ‘Stargate Project,’ the $500 billion AI infrastructure investment
Network Engineering
JANUARY 22, 2025
In Palo alto official document. For the decryption policy, the document state that SSL/TLS traffic requires a certificate but SSH doesn't. SSH use symmetric key for encryption while SSL/TLS use certificate with public key in it If SSH use public key-based authentication, why and how do firewall not needing anything to decrypt it. "The key used for SSH decryption is automatically generated when the firewall boots up " How do firewall know and generate the key ?
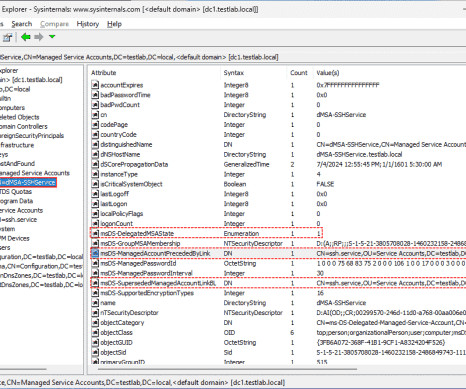
4sysops
JANUARY 22, 2025
question… “Microsoft recommends retaining the original service account in Active Directory even after it has been disabled during dMSA migration as a precaution.” What happens if you delete the original service account?
Network Engineering
JANUARY 22, 2025
First off, sorry if my question is trivial and uses the wrong terminology. Here is my problem: I have multiple network sharing the same networking space (10.10.10.0 / 255.255.255.0) all configured with static IP addresses. All these network share some identical IP addresses that, sadly, can't be reassigned. Therefore, connecting these networks together will create conflicts and is not desirable.

4sysops
JANUARY 22, 2025
Inside Anthropic’s Race to Build a Smarter Claude and Human-Level AI | WSJ

Cockroach Labs
JANUARY 22, 2025
As businesses increasingly demand scalability, resilience, and flexibility, transitioning from traditional centralized systems to distributed architectures has become a critical strategic move.

4sysops
JANUARY 22, 2025
OpenAI Unveils Project Stargate – $500 BILLION AI Mega Factories!

Docker Blog
JANUARY 22, 2025
Nearly half (45%) of developers say they dont have enough time for learning and development, according to a developer experience research study by Harness and Wakefield Research. Additionally, developer onboarding is a slow and painful process, with 71% of executive buyers saying that onboarding new developers takes at least two months. To accelerate innovation and bring products to market faster, organizations must empower developers with robust support and intuitive guardrails, enabling them t

4sysops
JANUARY 22, 2025
With Windows 11, Microsoft has not only changed the appearance of the Start menu but also its technical underpinnings. However, the Group Policy settings for configuring Start have not been updated. While it remains possible to add icons using Group Policy Objects (GPO), you must accept some limitations.

AWS Architecture
JANUARY 22, 2025
In this post, we will share how you can use multi-Region as an architectural approach to achieve higher resilience on Amazon Web Services (AWS). This approach relies on first operating a workload across multiple Availability Zones within an AWS Region, before expanding to achieve even higher resilience by using multiple Regions. This is because within a Region there are multiple Availability Zones, which are physically separated by many miles but still close enough together (60 miles or less) to

4sysops
JANUARY 22, 2025
Microsoft CEO Satya Nadella: AI simultaneously reduces the floor & raises the ceiling for all of us

Cisco Wireless
JANUARY 22, 2025
Learn about telemetry-first design in this latest blog from Kunal Hatode. At its core, telemetry design refers to the automated collection, transmission, and analysis of data from systems, devices, or applications. In the context of security operations, telemetry includes logs, metrics, and events generated by networks, infrastructure and applications.

4sysops
JANUARY 22, 2025
Salesforce CEO Marc Benioff: Don’t think Microsoft will use OpenAI in the future

DCNN Magazine
JANUARY 22, 2025
e& Carrier & Wholesale, a leading carrier which operates multiple geo-redundant SmartHub data centres across the Middle East – providing cutting-edge SmartHub IX services within these state-of-the-art facilities – has partnered with DE-CIX , a provider of premium interconnection services and an operator of carrier and data centre-neutral Internet Exchanges (IX).

4sysops
JANUARY 22, 2025
Windows 11/10 package manager UniGetUI gets major download and install improvements – Neowin The utility previously known as WingetUI has undergone a recent pre-release update, enhancing its functionality for package downloading and installation. This update, which follows a significant redesign and renaming to “UniGetUI,” introduces features such as multiple simultaneous downloads and the ability to initiate downloads directly through right-click options on packages.

DCNN Magazine
JANUARY 22, 2025
Planning permission has been granted in London for the worlds biggest living wall. Pure Data Centres , backed by funds managed by Oaktree Capital Management, will be integrating the wall into the second building on its campus in Brent Cross, North London. Pure DCs living wall, being installed by specialist firm Viritopia, will cover an area of 7,400 square metres, making it the largest in the world.
4sysops
JANUARY 22, 2025
Windows 11 Update DecisionMicrosofts Bold Security Move Windows 11 is set to enhance account security significantly with a new feature known as Administrator Protection, enabling better protection without compromising usability. This update comes as a relief amid ongoing concerns about security vulnerabilities and hacking attempts. Instead of needing two separate accountsone for administrative tasks and another for regular useusers can now manage elevated privileges from within the Windows Secur
Codecentric Blog
JANUARY 22, 2025
Stellt euch eine Insel namens "Alistair Island" vor. Diese Insel ist ein lebendiger Ort mit Husern, fruchtbaren Bden und einer eingespielten Gemeinschaft von Bewohnern, die nach klaren Ablufen leben. Jedes Geschehen auf der Insel ist von Bedeutung.
4sysops
JANUARY 22, 2025
Apple Intelligence turned on by default in upcoming macOS Sequoia 15.3, iOS 18.3 Generative AI assistants and productivity tools are becoming increasingly prevalent as software vendors integrate them by default. Apple plans to enable its AI features, known as Apple Intelligence, automatically in the upcoming macOS Sequoia 15.3 and iOS/iPadOS 18.3 updates for compatible devices.
Let's personalize your content