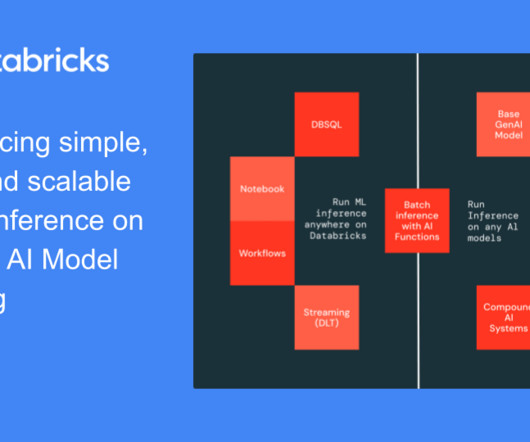
Introducing Simple, Fast, and Scalable Batch LLM Inference on Mosaic AI Model Serving
databricks
OCTOBER 22, 2024
Over the years, organizations have amassed a vast amount of unstructured text data—documents, reports, and emails—but extracting meaningful insights has remained a challenge.

















Let's personalize your content