Recognizing Women Driving Innovation
Cisco Wireless
AUGUST 26, 2024
The progress and pioneers we celebrate today are a testament to the resilience, innovation, and determination of countless women who have paved the way.

Cisco Wireless
AUGUST 26, 2024
The progress and pioneers we celebrate today are a testament to the resilience, innovation, and determination of countless women who have paved the way.
databricks
AUGUST 26, 2024
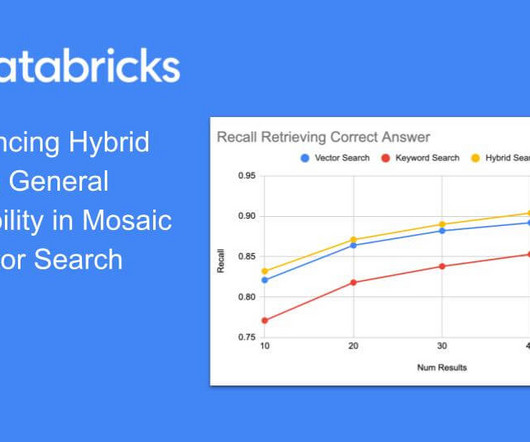
We're excited to announce the general availability of hybrid search in Mosaic AI Vector Search. Hybrid search is a powerful feature that combines.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cisco Wireless
AUGUST 26, 2024
Cisco announces a significant step in securing the AI-driven enterprise with intent to acquire Robust Intelligence, Inc., a trailblazing company at the forefront of AI security solutions.

Network Engineering
AUGUST 26, 2024
I have a avocent acs32 and and a juniper qfx10002-36q, i want to connect my qfx1k console port to avocent acs32 to be able to manage it as out of band, should i use normal ethernet cable to connect them or should i use crossover cable?

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

Cisco Wireless
AUGUST 26, 2024
As we celebrate Women's Equality Day on August 26th, it's important to consider and reflect upon the incredible potential that lies within each woman when given the right tools and opportunities.

Dataversity
AUGUST 26, 2024
As artificial intelligence (AI) integrates with the Internet of Things (IoT), a trillion-dollar question emerges: Is it better to process device data at the edge or in the cloud? This decision carries significant implications for privacy, performance, and the future of smart devices. So, let’s explore the growth of autonomous smart devices, examine the key […] The post Edge vs.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

Packet Pushers
AUGUST 26, 2024
On todays episode we delve into OSPF filtering. That is, how to filter routes from a devices routing table in an OSPF environment. This is a tricky business, because OSPF requires an identical database on every device in an OSPF area. That means you cant stop announcing a route from one OSPF router because you. Read more » On todays episode we delve into OSPF filtering.

Obkio
AUGUST 26, 2024
Learn the difference between latency and jitter, their impact on network performance, and how to measure and reduce them with the best tools.

Confluent
AUGUST 26, 2024
In our latest Confluent Champion post, Janis Hom, staff security GRC program manager, highlights how Confluent fosters a culture that helps her stay motivated.
databricks
AUGUST 26, 2024
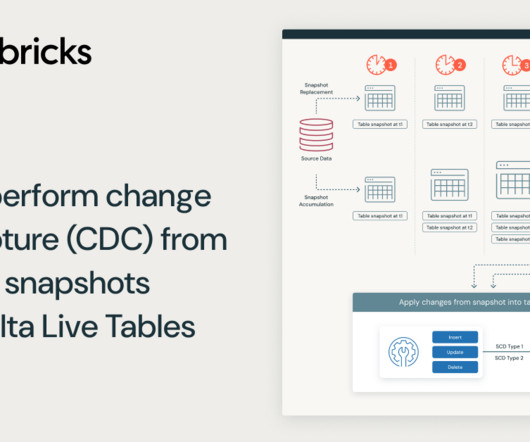
Learn more about processing snapshots using Delta Live Tables and how you can use the new Apply changes from Snapshshot statement in DLT to build SCD Type 1 or SCD Type 2 target tables delivering incremental data and insights that would typically take months of effort on legacy platforms.

Speaker: Anindo Banerjea, CTO at Civio & Tony Karrer, CTO at Aggregage
When developing a Gen AI application, one of the most significant challenges is improving accuracy. This can be especially difficult when working with a large data corpus, and as the complexity of the task increases. The number of use cases/corner cases that the system is expected to handle essentially explodes. 💥 Anindo Banerjea is here to showcase his significant experience building AI/ML SaaS applications as he walks us through the current problems his company, Civio, is solving.

Dataversity
AUGUST 26, 2024
Data privacy is the practice of handling personal information with care and respect, ensuring it is only accessed, processed, and stored in ways that align with legal requirements and individual consent. It protects personal data from unauthorized access and misuse. This includes securing data both at rest and in transit, applying best practices for encryption, […] The post 5 Technologies You Need to Protect Data Privacy appeared first on DATAVERSITY.

Rule 11
AUGUST 26, 2024
I’ve been working on new material over at Rule 11 Academy. This month’s posts are: BGP Route Reflector Lab The Clos Fabric (history) The Default Free Zone Network Addresses BGP Policy Entrance Selection (2) Interview Rubric Sample BGP Policy Entrance Select (1) Interviewing Background This brings us up to a total of 39 lessons. Each lesson should be about 15 minutes, so about 10 hours of material so far.

CATO Networks
AUGUST 26, 2024
Executive Summary To further raise awareness on threat actor activity in the dark web and hacking communities, today we are introducing the Cato CTRL Threat Actor Profile. This will be a blog series that profiles various threat actors and documents notable activity that we are observing. Our inaugural Cato CTRL Threat Actor Profile is on Yashechka. Yashechka is a Russian threat actor, who is a highly active participant across various underground hacking forums focused on data breaches, malware d

Cockroach Labs
AUGUST 26, 2024
User-defined functions (UDFs) and stored procedures (SPs) allow users to define a set of queries that can be executed at the database by providing only the function or procedure name and any relevant parameters. They provide building blocks for users to compose complex queries, which makes applications less error prone since users dont need to repeatedly provide the complex query.

Speaker: Christophe Louvion, Chief Product & Technology Officer of NRC Health and Tony Karrer, CTO at Aggregage
Christophe Louvion, Chief Product & Technology Officer of NRC Health, is here to take us through how he guided his company's recent experience of getting from concept to launch and sales of products within 90 days. In this exclusive webinar, Christophe will cover key aspects of his journey, including: LLM Development & Quick Wins 🤖 Understand how LLMs differ from traditional software, identifying opportunities for rapid development and deployment.

Packet Pushers
AUGUST 26, 2024
Today on the Tech Bytes podcast we talk cloud storage. More specifically, wedive into why its time for NFS to sail off into the sunset,particularly for cloud datasets. Our guest is Tom Lyon, an industrylegend who has delivered a talk entitled NFS Must Die. We talk withTom about the strengths and weaknesses of NFS, the. Read more » Today on the Tech Bytes podcast we talk cloud storage.

Packet Pushers
AUGUST 26, 2024
Take a Network Break! A US appeals court will let a privacy lawsuit against Google go forward, striking telecom workers are a reminder to test your resiliency planning, and AMD spends nearly $5 billion to acquire systems engineering talent from ZT Systems. Juniper Networks offers deep discounts and other enticements to get network engineers to. Read more » Take a Network Break!
Let's personalize your content