Enhancing LLM-as-a-Judge with Grading Notes
databricks
JULY 22, 2024
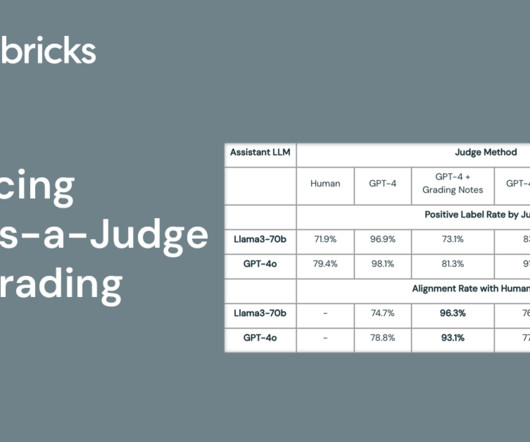
Evaluating long-form LLM outputs quickly and accurately is critical for rapid AI development. As a result, many developers wish to deploy LLM-as-judge methods.
databricks
JULY 22, 2024
Evaluating long-form LLM outputs quickly and accurately is critical for rapid AI development. As a result, many developers wish to deploy LLM-as-judge methods.

Dataversity
JULY 22, 2024
Discerning businesses are ensuring each area of their organizations has access to performance metrics. Armed with data, their teams can accelerate decision-making, respond to client and marketplace demands, and mitigate risks. The issue is many organizations have segregated data environments. Each department often has its own data management platform that may not integrate with other […] The post Data Concierge: Driving Business Intelligence Collaboration appeared first on DATAVERSITY.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
databricks
JULY 22, 2024
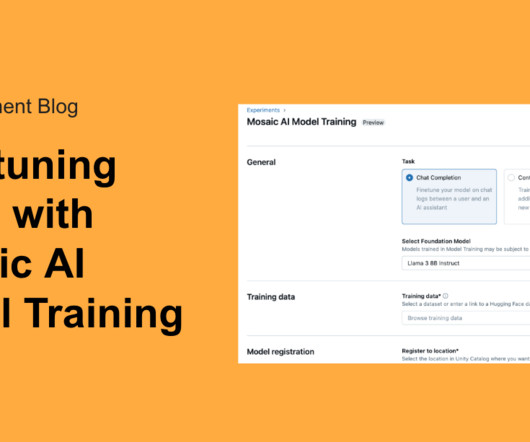
Today, we're thrilled to announce that Mosaic AI Model Training's support for fine-tuning GenAI models is now available in Public Preview. At Databricks.
InfoQ Articles
JULY 22, 2024
The main objective of this article is to delve into the technical complexities and strategic adjustments undertaken by Trainline. By examining challenges such as managing peak transaction volumes and orchestrating microservice architectures, we aim to uncover the valuable lessons learned and insights gained from Trainline's journey through the dynamic landscape of digital transportation platforms.

Speaker: Ben Epstein, Stealth Founder & CTO | Tony Karrer, Founder & CTO, Aggregage
When tasked with building a fundamentally new product line with deeper insights than previously achievable for a high-value client, Ben Epstein and his team faced a significant challenge: how to harness LLMs to produce consistent, high-accuracy outputs at scale. In this new session, Ben will share how he and his team engineered a system (based on proven software engineering approaches) that employs reproducible test variations (via temperature 0 and fixed seeds), and enables non-LLM evaluation m

databricks
JULY 22, 2024
Written in collaboration with Navin Sharma and Joe Pindell, Stardog Across industries, the impact of post-delivery failure costs (recalls, warranty claims, lost goodwill.

Obkio
JULY 22, 2024
Unravel the mystery of packet reordering! Learn its impact on network performance & discover tools like Obkio for detection and optimization.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

Dataversity
JULY 22, 2024
The increase in the prevalence and complexity of data breaches points to one conclusion – traditional cybersecurity measures are no longer enough to keep our valuable data safe. According to a recent report, data breaches exposed a staggering 35 billion records in the first four months of 2024. To deal with this escalating crisis, a new solution […] The post The Rise of Cybersecurity Data Lakes: Shielding the Future of Data appeared first on DATAVERSITY.

VIAVI Solutions
JULY 22, 2024
Observability is defined in mathematical terms as the ability to measure the internal state of a system based on only external information. On the other hand, monitoring is defined as a passive data collection process used to measure performance against predefined standards. In other words, network observability practices tend to be proactive, while monitoring tends […] The post Getting to the Heart of Observability appeared first on VIAVI Perspectives.

CATO Networks
JULY 22, 2024
The Paris Olympics are coming up, arousing excitement and anticipation around the globe. As the worlds greatest athletes prepare to compete on this renowned stage, lets shift our focus to a few of the earliest Olympics competitors – the Greek Gods. These deities, myth says, competed in the ancient Olympics, and later on, the Games were held in their honor.

Packet Pushers
JULY 22, 2024
Take a Network Break! This week we cover the CrowdStrike/Microsoft patch debacle, why SolarWinds isn’t entirely out of trouble following a judge’s dismissal of most–but not all–of an SEC lawsuit, and why an AT&T breach revelation highlights third-party risk. Juniper announces an AI infrastructure testing lab and enhancements to its capabilities to operate AI infrastructure, Read more » Take a Network Break!

Speaker: Anindo Banerjea, CTO at Civio & Tony Karrer, CTO at Aggregage
When developing a Gen AI application, one of the most significant challenges is improving accuracy. This can be especially difficult when working with a large data corpus, and as the complexity of the task increases. The number of use cases/corner cases that the system is expected to handle essentially explodes. 💥 Anindo Banerjea is here to showcase his significant experience building AI/ML SaaS applications as he walks us through the current problems his company, Civio, is solving.

Packet Pushers
JULY 22, 2024
Today on the Tech Bytes podcast we discuss vulnerability management for IoT and OTT devices with sponsor Palo Alto Networks. These devicesthink video cameras, sensors, medical equipment, industrial control systems, and so onpresent unique challenges when it comes to finding, prioritizing, and managing software vulnerabilities. Palo Alto Networks’ machine learning-based solutions offer visibility, risk prioritization, Read more » Today on the Tech Bytes podcast we discuss vulnerability
Let's personalize your content