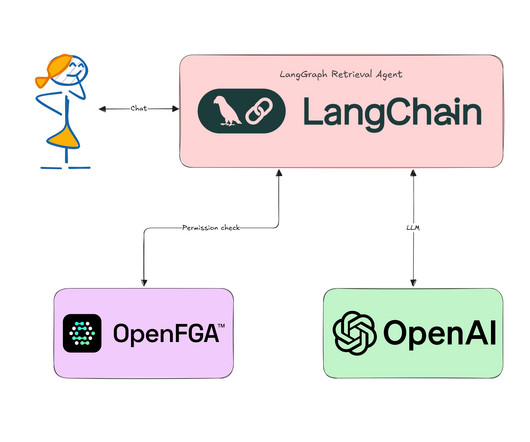
Build Secure LangChain RAG Agent Using Okta FGA and LangGraph
auth0
JANUARY 29, 2025
Learn how to use Okta FGA to secure your LangChain-based RAG agent.
auth0
JANUARY 29, 2025
Learn how to use Okta FGA to secure your LangChain-based RAG agent.

InfoQ Articles
JANUARY 29, 2025
A shift left approach to data processing relies on data products that form the basis of data communication across the business. This addresses many flaws in traditional data processing and makes data more relevant, complete, and trustworthy.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Cisco Wireless
JANUARY 29, 2025
Learn how IPv6 is finally gaining momentum, offering fresh opportunities as we move beyond the limits of IPv4.
Codecentric Blog
JANUARY 29, 2025
In todays rapidly evolving, data-driven world, organisations face an increasingly complex challenge: how to design, implement, and manage data interfaces that meet both immediate operational demands and long-term strategic business objectives. A data.

Geek Flare
JANUARY 29, 2025
In-depth Pipedrive CRM review where we coverits strengths, weaknesses, and best use cases to help you decide if it's the right CRM for your business. The post Pipedrive CRM Review: Features, Pricing, Cons & More appeared first on Geekflare.
4sysops
JANUARY 29, 2025
DeepSeek and distillation: Why the AI race will never be the same

Obkio
JANUARY 29, 2025
Learn what Monitoring Agents are and how to deploy and configure them in Obkios Network Performance Monitoring App.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

Obkio
JANUARY 29, 2025
Explore Obkios Network Performance Monitoring features through the "Network Performance" tab. Learn how to optimize your network, identify issues, and improve performance.
4sysops
JANUARY 29, 2025
Since DeepSeeks R1 model is built for efficiency during training and inference, I wanted to test how one of the distilled R1 models with fewer parameters performs on Ollama on my MacBook. Of course, you can also experiment with DeepSeek R1 on your Windows PC.

DCNN Magazine
JANUARY 29, 2025
Portus Data Centers has announced a strategic partnership with Megaport , a Network as a Service (NaaS) provider based in Luxembourg. Megaport, which is actively seeking to expand across Europe, has deployed a point of presence (PoP) at Portus Data Centers Munich, allowing joint customers to benefit from wider reach and enhanced connectivity capabilities in Central Europe.

4sysops
JANUARY 29, 2025
Unveiling the Reality of the Microsoft 365 promo Email – Office Watch Microsoft announced new features for its Microsoft 365 subscription, specifically highlighting the introduction of Copilot. However, the promotional email did not mention the significant price increase, with subscriptions for individuals rising by 30% to over 40%. In the U.S., the cost of the Microsoft 365 Family plan has increased from $99.99 to $129.99, equating to a $30 hike while Microsoft characterizes it as merely

DCNN Magazine
JANUARY 29, 2025
atNorth , the Nordic colocation, high-performance computing, and artificial intelligence service provider, has become a signatory of the United Nations Global Compact as part of its ongoing commitment to business sustainability. The UN Global Compact is a voluntary initiative that enables members to align their operations and strategies with 10 universally accepted principles in the areas of human rights, labour, environment and anti-corruption.

4sysops
JANUARY 29, 2025
Former Intel CEO Says After Seeing DeepSeek, He’s Done With OpenAI DeepSeek, a Chinese AI company, is challenging Western tech firms like Nvidia, prompting significant shifts in the industry. Its advancements have resulted in a decline in Nvidia’s stock prices and have sparked debates among tech leaders and political figures in the U.S., including President Trump, who acknowledged DeepSeek as a wake-up call.

DCNN Magazine
JANUARY 29, 2025
A new 5G network backbone for more advanced research initiatives and immersive learning platforms has been deployed at Rosenheim Technical University of Applied Sciences (TH Rosenheim) in Germany, thanks to a collaboration between Slovenias Kontron and Mugler SE. Slovenias Kontrons 5G Mobile Private Network (MPN), integrated by network systems integrator and telecommunications solutions supplier, Mugler SE, will provide greater speeds, low latency, and increased capacity for more than 7,500 stud

Wahl Network
JANUARY 29, 2025
Welcome to the end of January in 2025! Is the time flying for you? Because it sure is for me! The past month of switching from corporate employment to self-employment has been extremely interesting for me. Top 3 Activities: Schedule. Figured out a new schedule for my time – when I want to be available and when I don’t want to be available.
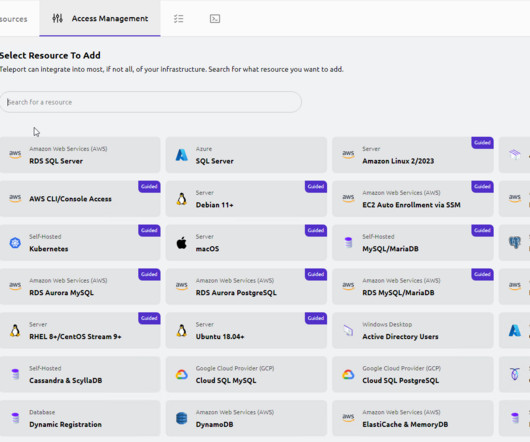
RDR-IT
JANUARY 29, 2025
Dans ce tutoriel, nous allons voir comment le dploiement du bastion d’administration Teleport l’aide de Docker. Avant de commencer ce tutoriel, un petit rappel sur les Bastions d’administration, ce sont gnralement des applicatifs qui vont permettre de grer les accs aux diffrents serveurs (Windows et Linux) et applications (Base de donnes … ) au seins.

Packet Pushers
JANUARY 29, 2025
Are you ready to go from zero to hero in GitNops? On todays podcast, we talk with Tom McGonagle, who shares and explains git, CI/CD and DevOps and how that all fits into network engineering. The conversation also covers the evolution of containerization and Kubernetes, highlighting their roles in modern network automation. Tom also encourages. Read more » Are you ready to go from zero to hero in GitNops?

4sysops
JANUARY 29, 2025
Windows 11 Canary build 27783 is out with a new File Explorer section and more – Neowin Microsoft has introduced a new preview build of Windows 11, specifically build 27783, in the Canary Channel. This version includes enhancements to File Explorer, particularly a new tab for accessing shared files and improvements in the Magnifier feature. Users signed in with a Microsoft account can easily access files shared via email or Teams.
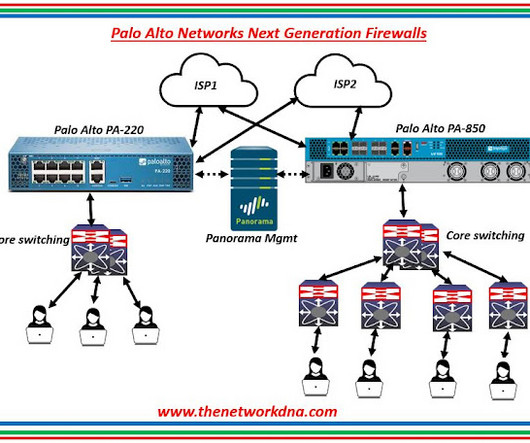
The Network DNA
JANUARY 29, 2025
How to backing up the PaloAlto Firewalls Configurations ? Backing up your Palo Alto firewalls is crucial before performing an upgrade or making any changes. You should back up both the primary and secondary firewalls in your HA pair to ensure you have a safe recovery point in case of any issues. Here's a detailed step-by-step guide to backing up the configurations of your Palo Alto firewalls.

CATO Networks
JANUARY 29, 2025
As adults, we rarely question the safety of the medicine we consume. This confidence stems from knowing that these products undergo rigorous, independent testing before reaching pharmacy shelves. Security solutions, especially those critical to enterprise operations, deserve the same level of scrutiny. Before trusting a platform to safeguard our data and systems, its essential to verify that it can counter the sophisticated threats we face today.

4sysops
JANUARY 29, 2025
Should You Learn to Code in the Age of AI? Pros and Cons TechTarget and Informa Tech have formed a combined network comprising over 220 online properties that cover more than 10,000 topics, reaching an audience of over 50 million professionals. This collaboration aims to provide original and unbiased content to assist in informed decision-making in various business areas.

Dataversity
JANUARY 29, 2025
In database management, replication has long been a cornerstone of data reliability, redundancy, and performance. For those familiar with MySQL, replication may seem straightforward simply read the binary log and apply it to a replica server, right? While this basic understanding is correct, improving replication performance is far more complex, particularly when dealing with […] The post MySQL Replication: Unlocking Performance and Flexibility with Advanced Techniques appeared first on D

4sysops
JANUARY 29, 2025
Microsoft Teams to Add Brand Impersonation Protection to Prevent Phishing Attacks Microsoft Teams will introduce a brand impersonation protection feature next month, aimed at alerting users to potential impersonation attempts in external messages. This feature automatically scans for phishing risks when external access is enabled, notifying users about high-risk interactions in their chat messages without requiring admin intervention.

Dataversity
JANUARY 29, 2025
It is obvious how essential data security has become in the face of sophisticated cyber attacks. Companies need to continue to improve their processes and systems to protect sensitive information. While advanced cybersecurity technologies help massively, they cant do it alone. Ensuring all-around safety requires the humans in the loop to work in tandem with […] The post Securing Your Companys Data Assets Depends on Both Tech and Humans appeared first on DATAVERSITY.

4sysops
JANUARY 29, 2025
Microsoft Entra Gets New Identity Secure Score Recommendations to Boost Security Microsoft Entra has launched new Identity Secure Score recommendations aimed at enhancing organizational security for administrators. These recommendations offer actionable insights to help identify and mitigate security risks, aligning with best practices and industry standards.

EA Voices
JANUARY 29, 2025
From Architecture & Governance Magazine By Wayne Cleghorn, Cyber Security Partner, Excello Law Cyber attacks are increasing in frequency, complexity, and intrusiveness. Incidents are becoming more expensive to manage and repair.

4sysops
JANUARY 29, 2025
Rollback to Windows 11 23H2, uninstall Windows 11 24H2 and downgrade (how-to) To uninstall Windows 11 24H2 and revert to the more stable Windows 11 23H2, users can utilize two primary methods: the standard recovery option within the ten-day rollback period and the use of Windows 11 23H2 ISOs for those who have surpassed that timeframe. Windows 11 24H2 has encountered significant issues since its release, leading Microsoft to stop updates for many users until these problems were resolved.

4sysops
JANUARY 29, 2025
The value of AI: How Microsofts customers and partners are creating differentiated AI solutions to reinvent how they do business today – The Official Microsoft Blog Organizations worldwide are exploring how artificial intelligence (AI) can drive innovation and create business value. Microsoft aims to assist customers in their AI transformation by offering a range of tools such as Copilots and agents, alongside robust cybersecurity foundations.

4sysops
JANUARY 29, 2025
OpenAI has evidence that its models helped train Chinas DeepSeek | The Verge Chinese AI company DeepSeek has gained attention for its affordable AI models that go against those from OpenAI, which believes that these models may have been created using its own data. Investigations by OpenAI and Microsoft are underway to determine whether DeepSeek improperly utilized OpenAI’s API to develop its models.

4sysops
JANUARY 29, 2025
AI use drives APIs to become the main attack surface APIs have become the primary target for security attacks in the past year, with artificial intelligence (AI) significantly contributing to the associated risks. A survey conducted by Wallarm among 200 enterprise leaders in the US indicates that over 53 percent of these organizations are engaged in various AI deployments facilitated by API technology.

4sysops
JANUARY 29, 2025
Apple chips can be hacked to leak secrets from Gmail, iCloud, and more – Ars Technica Two recently discovered vulnerabilities in Apple-designed chipsFLOP and SLAPexpose sensitive information like credit card details and location data, enabling unauthorized access for remote attackers. These vulnerabilities affect the later generations of Apple A- and M-series CPUs, with exploits stemming from issues related to speculative execution, which optimizes performance by predicting program control
4sysops
JANUARY 29, 2025
OpenAI: Introducing the Realtime API OpenAI has launched a public beta of the Realtime API, which allows developers to create low-latency, multimodal applications featuring speech-to-speech interactions. This API offers six preset voices, improving user experiences across various applications, such as education and customer support. In conjunction with the Realtime API, the Chat Completions API now supports audio inputs and outputs, enabling developers to utilize a single API call for natural co
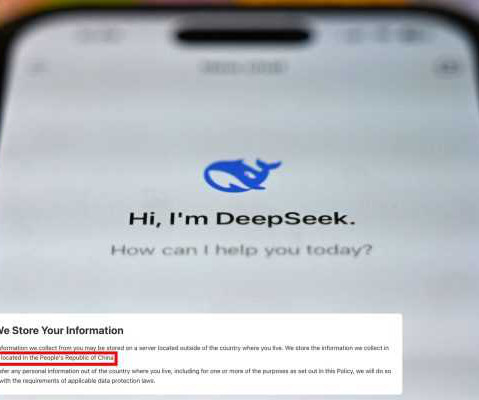
4sysops
JANUARY 29, 2025
DeepSeek app stores user data in China — sparking US security concerns: experts DeepSeek, a Chinese AI chatbot, has significantly impacted the US market, leading to a $1 trillion drop in value, as it stores US user data on servers in China, raising national security concerns. Launched on January 15, it quickly became popular, surpassing 2 million downloads and topping app store charts.

4sysops
JANUARY 29, 2025
DeepSeek’s AI avoids answering 85% of prompts on ‘sensitive topics’ related to China | TechCrunch The AI chatbot DeepSeek has gained significant attention, achieving top rankings on app stores and creating considerable buzz in financial markets. Developed by the Chinese hedge fund High-Flyer, its performance-to-cost ratio outshines competitors like OpenAI.
4sysops
JANUARY 29, 2025
Windows 11 KB5050094 24H2 adds features, direct download.msu from Microsoft An optional update for Windows 11, identified as KB5050094, was made available on January 28 for version 24H2. Users can download the update through Windows Update or via direct download links. This update includes several new features and fixes, namely addressing the bug where the mouse cursor would disappear during text selection in various Chromium-based applications.

4sysops
JANUARY 29, 2025
Qwen 2.5-Max outperforms DeepSeek V3 in some benchmarks Alibaba has introduced Qwen 2.5-Max, a new Mixture-of-Experts (MoE) large-scale model that has undergone extensive pretraining on over 20 trillion tokens. The model incorporates advanced techniques, including Supervised Fine-Tuning (SFT) and Reinforcement Learning from Human Feedback (RLHF). Developers and researchers can access Qwen 2.5-Max through Alibaba Cloud and interact with it through the Qwen Chat platform, which allows exploration
4sysops
JANUARY 29, 2025
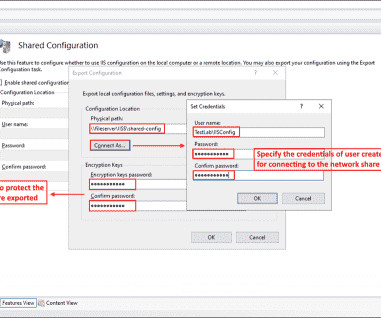
Hi. This works when you don’t have passwords set in IIS, like for example when you have the Application pools default user set with a local user and it’s password. If you try to export this to another server, that password will not be able to be decrypted, because the encryption keys are different on the other server. I know how to solve this issue for Windows 2012 R2 servers(IIS 7) but I could not find a solution for server 2022(IIS 10), where the encryption mechanism is different.
Let's personalize your content