Exploring AAA and TACACS Configuration with Cisco Modeling Labs
Cisco Wireless
OCTOBER 28, 2024
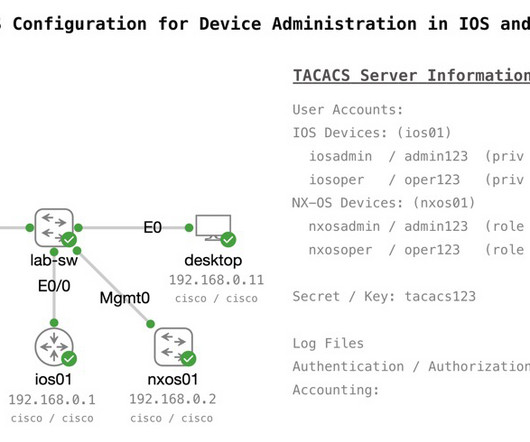
Explore AAA, an essential topic found on many Cisco Certification exams. Go from concept to configuration with Hank's step-by-step guide, complete with downloadable CML topologies to suit your learning needs.















Let's personalize your content